How Cyber Adversaries Attack Each of the OSI Layers 1-7

The cybersecurity landscape is constantly evolving as threat agents find new ways to compromise systems and steal sensitive information. To effectively defend against these attacks, it is crucial to understand different types of cyber attacks, how they are carried out, and the various techniques used.
This article looks at the different network security threats broken out across the seven layers of the OSI model, methods used to carry them out, and some best practices for prevention and mitigation.
Jump to a section…
The Seven Layers of the ISO/OSI Model
Types of Cyber Attacks on Each OSI Layer
Security That Stops Attackers in Their Tracks
The Seven Layers of the ISO/OSI Model
The OSI (Open Systems Interconnection) model is a conceptual framework used for understanding the different functions of a network system. The OSI was developed by the International Organization for Standardization (ISO) in hopes of increasing interoperability between different vendors and clearer standards for network communication. Although the OSI is not used for building networks (the TCP/IP is the most recognized and widely used protocol for network communication), it provides a helpful framework for classifying different types of cyber attacks.
Most cybercriminals will target a network on one of the seven layers of the OSI, and organizing threats along the different levels can make it easier to think about prevention, detection, and remediation strategies.
For even more detail, this infographic is a great reference.
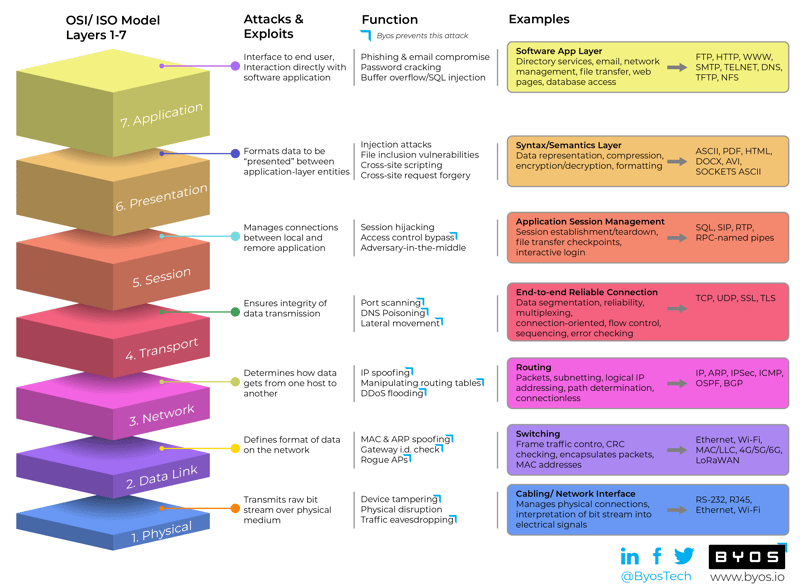
(note: in the listing of attacks below, the items with ✔ are attacks that Byos thwarts.)
Types of Cyber Attacks on Each OSI Layer
Layer 1 - Physical
Many methods are used to further the attack chain. Bad actors have been known to take temporary positions or join a cleaning crew to get inside a facility. Conference rooms, public areas, and even parking areas where a WiFi signal is available are other locations where a cybercriminal posing as legitimate personnel can access the premises.
- Tampering with devices and cables: A malicious actor may physically cut cables, unplug devices, or connect skimming devices to a network cable in order to steal sensitive information.
✔ Traffic eavesdropping: Accesses traffic through WiFi exploiting WPA2 or other vulnerabilities to acquire passwords, or by connecting to an Ethernet port on your network. Passive Ethernet tap devices are widely available, cost around $40, don’t require power, and look just like a section of a cable when the wires in fact connect to a monitoring port. This makes them both a particularly appealing tool for cybercriminals and an especially difficult one to detect for security teams.
The physical layer is the foundation of your network architecture, so a cyber attack on this layer can be incredibly damaging to the rest of your operations. Limiting access to your server rooms and Ethernet ports in public areas, and minimizing “WiFi signal leakage” are obvious places to start. If this layer is compromised, protections at the device level can prevent exploitation coming from the network from intruders with physical access to the network.
Layer 2 - Data Link
Attacks on Layer 2 usually involve an attacker spoofing valid credentials or attempting to imitate a legitimate request in order to eavesdrop on your network traffic. The good news is that most of these are preventable with basic security features, such as disabling dynamic trunking on all ports (and requiring them to be manually enabled on ports that require them). Security teams should also consider creating a BPDU guard and configuring ports to remember only a specific set of MAC addresses.
✔ MAC spoofing: There are two methods in this kind of attack. The first is adding an inline switch that routes data to the wrong MAC address. The second is changing the MAC address of a device to steal its network identity.
✔ ARP spoofing: Address Resolution Protocol opens communication to other devices on a network without requesting authentication from an unverified source. ARP requests are sent to connect a device to an attacker’s computer.
✔ VLAN hopping: With access to one VLAN, an intruder can switch (by imitating a trunking switch) or double tag (by connecting to an 802.1Q port) to other VLANs hopping across networks to acquire new targets.
✔ DHCP spoofing: Set an attacking device as the DNS server or main gateway to respond to DHCP requests, which then intercepts network traffic.
✔ Rogue access points: An access point is added on a network without the network owner’s permission and uses it to intercept data. A common example would be a cybercriminal creating an access point on an open network, like a hotspot in a coffee shop or airport, with the same or a similar name. If a user is fooled into logging into a rogue access point, the attacker can intercept passwords, gain access to data, or take control of the entire PC without the owner knowing. This attack is a form of what is also know as a “Twin Towers” technique.
|
WiFi Pineapple Though the WiFi Pineapple was created for security teams to conduct penetration testing, its affordability ($199 as of this writing) and user-friendly interface make it an appealing tool for attackers. A malicious actor can place the WiFi Pineapple (known as an “evil twin” when used for criminal purposes), on your premises, creating a rogue access point for unsuspecting users who may log into a fake SSDI with a similar name to the legitimate access point. The WiFI Pineapple’s mere existence is a great reminder to train your employees about the dangers of outside actors attempting to access your premises. It’s also a great reminder for the average consumer to be extra vigilant when connecting to an open WiFi network. |
Layer 3 - Network
The only way to prevent DDoS attacks is to cloak the device so that the devices are not discoverable by bad actors and to prevent abnormal traffic from filtering into your network by installing packet sniffers which can analyze incoming packets and compare them against a baseline. The other attacks below are generally against network devices and not the endpoints themselves, so the attacks are difficult to detect or prevent using operating system-based agents.
✔ IP spoofing: Modifies IP addresses to conceal identity or impersonate an authorized device.
✔ Manipulating routing tables: Changes routing tables to reroute the destination of packets to redirect data to a malicious server or service.
✔ ICMP redirect: Similar to route table manipulation, an out-of-band message is sent to a device informing it of a better route through a network. That route leads the host to connect to the attacker’s machine.
✔ TCP/UDP flood (DDoS): Floods ports on the host server with UDP packets.
✔ SYN flood (DDoS): A connection is initiated without finalizing the connection. Because the server has to “wait” for half-opened connections to process, it is overwhelmed and can no longer respond to legitimate traffic.
✔ Smurf attack (DDos): Floods a network with ICMP packets by making requests with a spoofed IP address.
Layer 4 - Transport
Preventing lateral movement is one of the most efficient and cost-effective ways to secure your entire network. If one device is impacted by ransomware, it can be easily restored and the ransom on a single device doesn’t break the bank. But if that ransomware spreads across your entire network, the effort and cost of restoring all of your devices can quickly become insurmountable. Attackers know this and will adjust their ransom amount based on the number of devices they are able to access.
If an attacker is only able to access one or two devices, their ability to achieve their ultimate objective is diminished greatly, and they are more likely to abandon further attacks due to the time and effort required.
✔ Lateral Movement: An attacker uses network scanning, discovery, and vulnerability exploits, to identify other devices on your network, moving from device to device and thus eventually gaining access to your entire network. This is perhaps one of the most damaging attacks on our list, so taking steps to prevent lateral movement attacks will often have the biggest payoff in terms of your overall security strategy.
✔ TCP/UDP port scanning: Port scanning discovers vulnerabilities by sending packets to specific ports and then analyzing the responses from the device.
✔ DNS poisoning: Corrupted information is inserted into a DNS server, which then responds to queries by directing users to a malicious destination. DNS does not verify entered information. DNSsec protects from this attack, and should be a priority for your team.
✔ TCP/UDP flood (DDoS): Bridges Layer 3 and Layer 4 on the target host’s ports using IP packets with UDP datagrams to overwhelm the device which makes it unable to respond.
Layer 5 - Session
A key function of protecting this layer are Identity & Access Management (IAM) platforms like Okta, BeyondTrust, and CyberArk, as well as passwordless technologies like HYPR, Trusona, and Auth0.
- Session hijacking: An internet session is monitored, for instance, an attacker watching a login to a bank account, or some other application containing sensitive information. This is often achieved by intercepting the session cookie in a malicious website or application.
✔Access control bypass: There are two methods of this attack. The first is when an attacker gains access to an existing session and is able to use those privileges in either another session or from another computer. This can be done in a browser session or within some other application. The second method is a network access control bypass. This attack method has successfully bypassed VPN, NAC, and WAF technologies used to secure network access via the network port, an endpoint agent, the cloud, or a gateway or termination point. This tactic is effective if the endpoint operating system can be compromised via a zero-day or known vulnerability, privilege escalation, or compromised credentials. Newer network security technologies suffer the same deficiency. SSE/SASE, ZTNA, network overlays, and microsegmentation rely on protection from one of the following points of enforcement: at the network port, an endpoint agent, in the cloud, or from a control appliance connected to the switch infrastructure.
✔ Adversary-in-the-middle attack: Formerly referred to as man-in-the-middle, various types of cyber attacks involve intercepting communications. These types of attacks have become more common as cybercriminals impersonate legitimate employees to gain access to protected data.
Layer 6 - Presentation
Setting up proper input validation protocols is one way to prevent attacks on the presentation layer. In fact, the easiest way to ward off these attacks is by ensuring your applications are coded properly from the get-go since most attacks on Layer 6 are the result of poorly written, vulnerable applications.
- Cracking encryption: Encryption cracking bypasses encryption to access protected information.
- Injection attacks: Code is added into a program or a query to steal data or execute commands in an application.
- File inclusion vulnerabilities: Poorly coded applications allow uploaded files into a server or submitting input.
- Cross-site scripting (XSS): An injection attack in which a malicious script is input into an otherwise safe website, usually via a browser-side script sent to another user. Once a script is accepted, the attacker can access cookies and hijack an internet session.
- Cross-site request forgery (CSRF): Usually executed via an email, a user of a web application is tricked into taking actions like transferring funds or granting user credentials to a malicious actor.
Layer 7 - Application
Browser and email protections are common for both consumer and enterprise security. Web Application Firewalls (WAF), API security solutions, and other application protections are a complicated mix of technologies far too extensive to be covered here.
- Phishing: A form of a social engineering attack, phishing (sometimes called a BEC or business email compromise attack) refers to a fake email, often sent from a supposedly legitimate source (e.g., someone the victim knows or a trusted vendor or provider), urgently requesting help or information.
- Password cracking: A cybercriminal can use a password cracking tool or a brute force attack to gain access to passwords stored in a database. Weak passwords used over and over on different websites are especially vulnerable.
- Buffer overflow: Feeds input to a vulnerable program, knowing that the program will attempt to store the input which will overflow its memory. This tricks the computer into running the attacker’s program.
- Format string attack: When an application doesn’t properly validate input, an input string fed into the application can overwrite it with malware or crash it.
SSE/SASE technologies are becoming more prevalent to protect cloud, voice/video conference, mobile, and site-to-site-level communications. Some have added network access enforcement, remote access security, and even various ways to provide some level of IoT/OT protection as well.
The complexities in Layer 7 protections can make technology selection difficult because there is overlap and duplication in the controls they address, which will lead to budget and support duplication and overlap. And some of the vendors are expanding their offerings to address controls in the other layers as well, in an attempt to “lock” their customers into a single solution, essentially asking their customers to “put all their eggs in one basket.”
Most security architects recognize that the challenges of endpoint and network security in layers 1-5 are much different than those in cloud and application security. So their approach separates network and endpoint protection from their application and cloud protections.
|
Technologies that protect Layers 6 & 7 |
Description |
Vendors |
Open Source |
|
Web Application Firewalls (WAF) |
Protect web applications from a wide range of attacks, including injection attacks, cross-site scripting), cross-site request forgery, etc.. |
F5, Imperva, Akamai, Barracuda |
ModSecurity |
|
Intrusion Prevention Systems (IPS) |
Detect and block many levels of attacks, especially those that target Layers 6 & 7 |
Cisco, Check Point, Fortinet |
Snort |
|
Endpoint Protection Platforms (EPP) |
Protect endpoints at multiple layers. EPPs are typically know as anti-malware, endpoint firewalls, ad blockers, and intrusion prevention functions. |
Microsoft, MalwareBytes, McAfee |
ClamAV |
|
Network Access Control (NAC) |
Blocks unauthorized network access to control access. Some also validate the security posture of devices, users, and applications to enforce policies |
Cisco, Forescout, Pulse Secure |
PacketFence |
|
eXtended Detection & Response (xDR) |
Merges data from endpoints, networks, cloud services, and applications. This provides a more comprehensive view of threats and intrusions. |
SentinelOne, CrowdStrike, CyberReason |
Wzuh,Open EDR |
|
Virtual Private Network (VPN) |
Provide encrypted tunnels from remote locations into the enterprise network inside the perimeter protections |
Fortinet, Citrix, Cisco |
OpenVPN |
|
SASE/SSE |
Deliver WAN and security controls as a cloud computing service directly to the source of connection (user, device, Internet of things (IoT) device, or edge computing |
CATO, Zscaler, NetSkope, Perimeter 81, Akamai |
flexiWAN |
Security That Stops Attackers in Their Tracks
Most of the cyber attacks we described have the potential for lateral movement — it takes only one unsecured endpoint in your network infrastructure for the rest of your systems to fall into the hands of a cybercriminal. Building in prevention at the lower layers in your network (1-5) will often stop adversaries from exploiting layers 6-7 (though of course protecting these layers to the best of your ability is also important).
|
The cost of an attack, intrusion, breach, or exploit that never happens has zero cost, requires no people, and suffers no loss of reputation. |
The key takeaway is that preventing initial access into assets and limiting the “blast radius” of an intrusion goes far in frustrating an adversary who is probing for weaknesses in your defenses.
Byos has created a system that prevents the exploits detailed here in Layers 1-5, plus more than 15 others not listed. Byos also compliments security technologies in Layers 5-7 like SSE & SASE, anti-malware, anti-phishing, MFA, IAM, EDR/MDR/XDR, WAF, and other protections.