🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
DNAT and Security in Industrial Networking
Operational Technology | Remote Access | Zero Trust | Industrial IoT
March 19th, 2023
Introduction
Industrial networking is complicated and time consuming for myriad reasons, not the least of which are:
- The variety of different device types from many vendors
- The plethora of management applications leveraging inconsistent ports and protocols
- And the necessity for security and availability, together, while impacting performance as little as possible.
This is a great article by Josh Varghese describing some fundamentals of NAT and DNAT in the context of an OT environment.
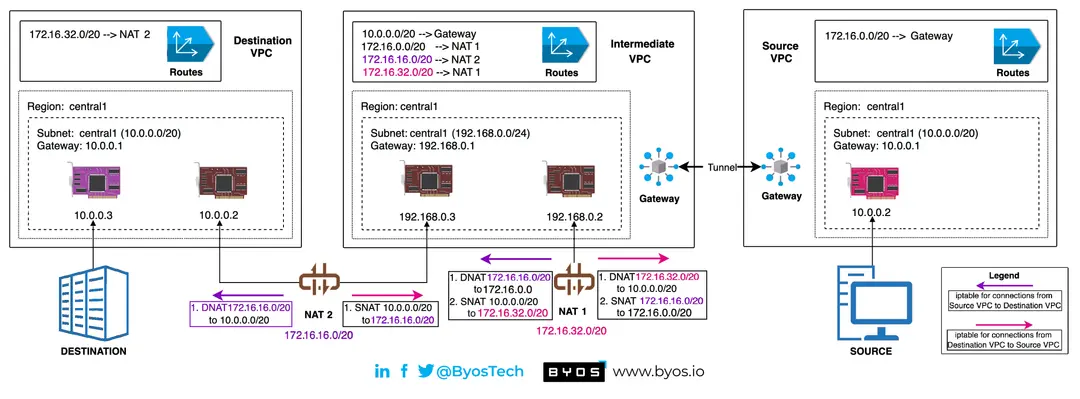
The limitations of NAT and DNAT
While NAT and DNAT are foundational networking technologies, they were originally designed with availability in mind. In the context of managing an industrial network, DNAT by itself does not provide any security. In fact, DNAT can expose valuable information to the network and the asset, which can then be exploited by an attacker to map and infect other assets on the network.
From the Byos perspective, the question of "should I implement NAT/DNAT or not" is the wrong one to ask. NAT/DNAT may be simple to install and configure, but providing 3rd party or remote access isn't. It ultimately complicates the security architect’s job. Configuring the underlying network to communicate, while applying security layers, still requires more time and expertise than it should to efficiently and securely manage an OT network. Instead, Byos offers a better approach to achieving both availability and security without relying on manual implementations of NAT or DNAT on the underlying network.
What to learn more about securing your manufacturing operation? Read more here.
The better way
There is a faster, more cost-efficient way to achieve both availability and security in your industrial network: Byos. Byos simplifies network management and provides security by default, without relying on NAT or DNAT on the underlying LAN. By isolating the physical asset (such as a PLC or HMI ) from the LAN, the Byos Secure Edge renders the asset's underlying networking settings, such as Default Gateway and DHCP, irrelevant and thus invisible to attackers on the network.
The Byos Secure Edge leverages DNAT, but with an improved approach: Byos doesn't DNAT anything over the exposed interfaces (Wi-Fi or Ethernet). Instead, DNAT is kept internally by Byos and is not advertised to the network or assets. The Byos Secure Edge only allows the translation of DNAT through our own Secure Lobby overlay network, and only after applying access control on OSI Layers 2, 3, and 4, as per the policy set by the Network Admin in the Byos Cloud control plane.
Conclusion
Manually configuring NAT/DNAT in your network is simple from the perspective of getting a device online, but deploying across a multi-site industrial network? Take note of the advantages of implementing Byos: ease-of-universal access, deploying to many devices with consistency, and overall visibility and control. Byos makes the simplicity and total cost of administering to an entire fleet the highest value decision.
Implementing Byos provides security by design and simplifies OT network access, visibility, and management. Byos ensures that only authorized and authenticated devices can communicate, while eliminating any asset exposure on the underlying physical network, lowering total risk.
Byos can help streamline your OT Network Hardening initiative. Click here to schedule a demo to find out more!
Platform
Use Cases (Industry)
Use Cases (Application)
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)