🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
Latest Blog Posts

Simplifying OT Security Configuration: Power Without Complexity
In complex industrial environments, security shouldn’t be a burden. Byos simplifies OT security configuration—delivering power, visibility, and Zero Trust control without the complexity.
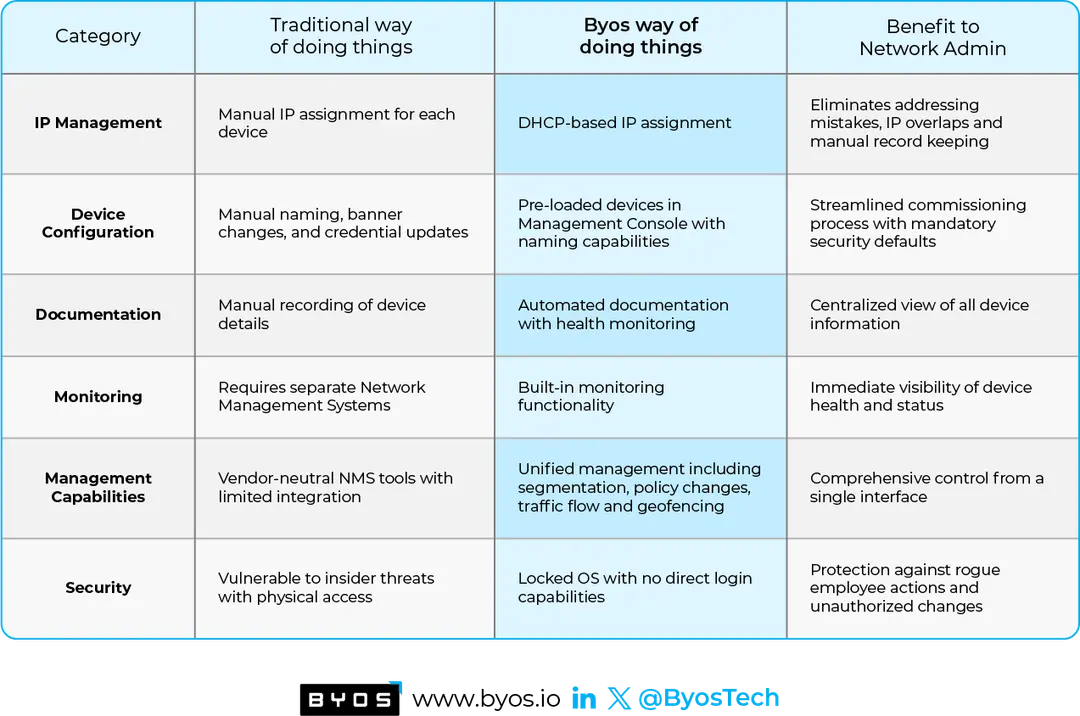
Rethinking OT Network Administration: How Byos Transforms Legacy Practices
Traditional OT networking approaches are becoming a burden. Byos takes a fundamentally different approach—one that simplifies, secures, and streamlines network administration
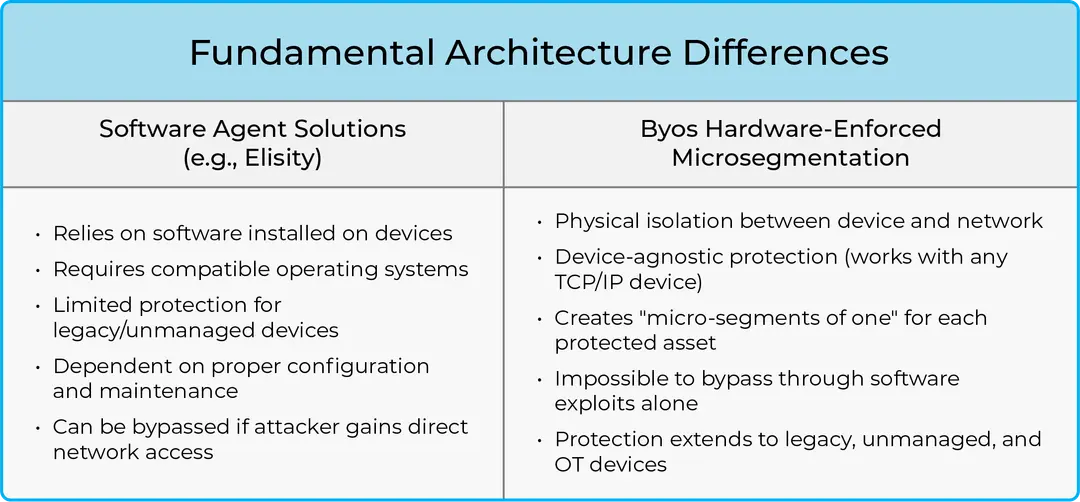
Byos vs. Software-Agent Microsegmentation: Two Paths Toward Zero Trust
Software-based microsegmentation has limits. This blog explores how Byos’ hardware-enforced approach creates true "microsegments of one," providing protection for any device—even those that can’t run agents.
How Microsegmentation Enhances OT Security: Insights for Network Security Architects
In today’s industrial landscape, the convergence of Operational Technology (OT) and Information Technology (IT) has introduced both efficiency and connectivity. However, it also brings new cybersecurity challenges. For a Network Security Architect looking to safeguard OT environments, and microsegme
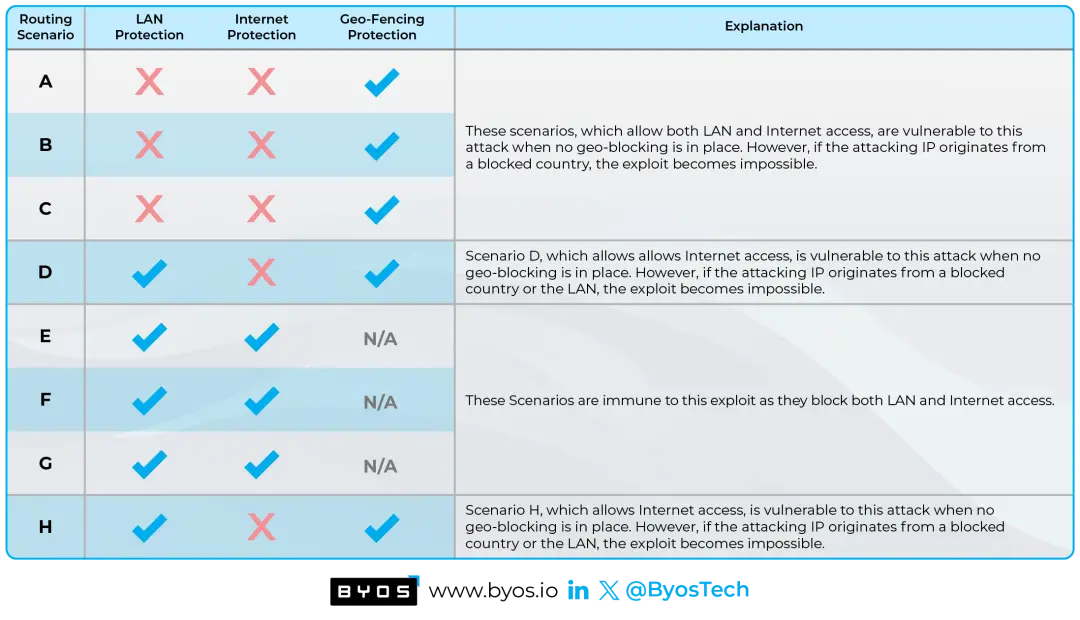
Defending against Critical Vulnerabilities by Preventing Lateral Movement
The Oligo research team has uncovered a severe vulnerability dubbed "0.0.0.0 Day," on all major consumer Operating Systems. This vulnerability has been dormant for 18 years. It exposes a fundamental weakness in browser network request handling, potentially granting malicious actors access to sensiti
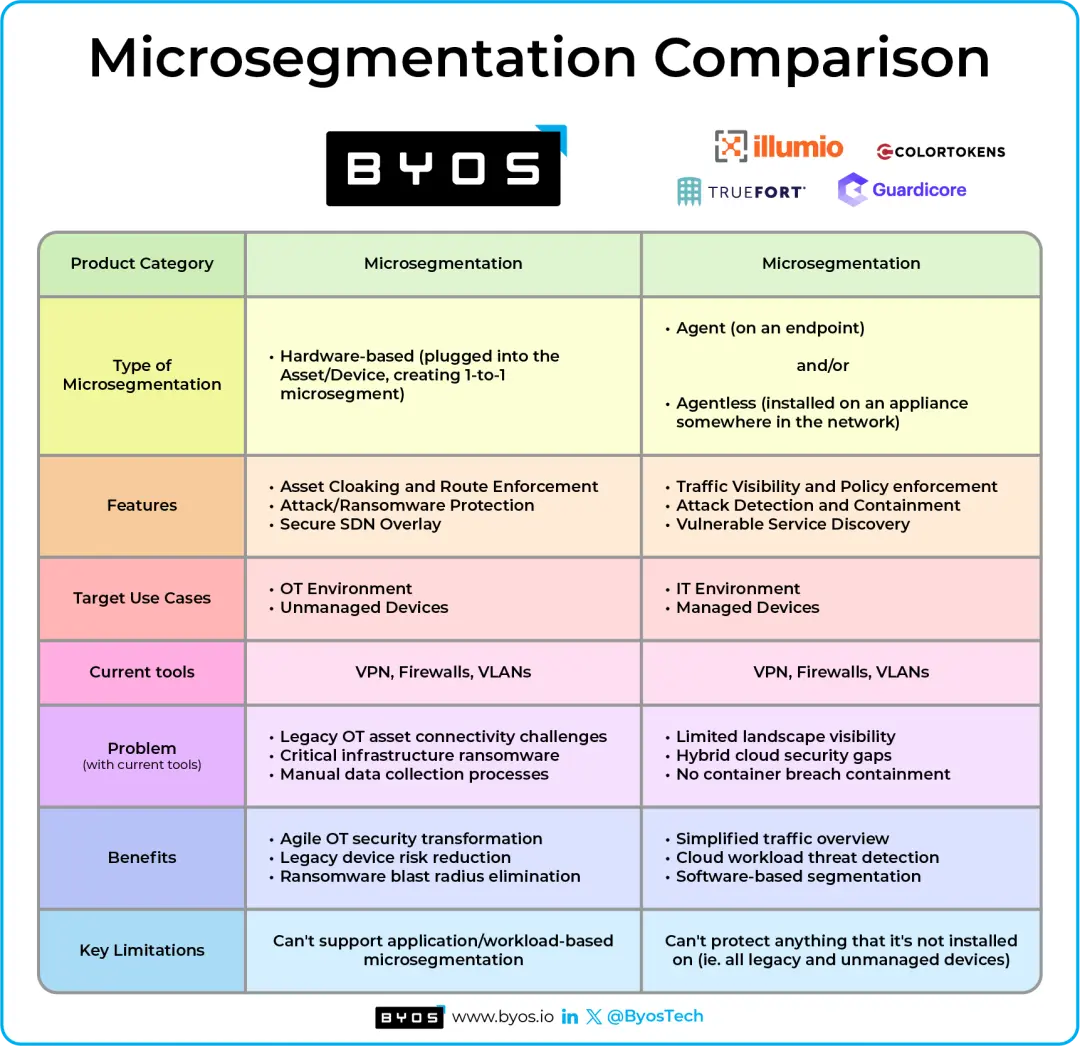
Applying Network Microsegmentation Maturity Levels in Critical Infrastructure using NSA Guidelines
The NSA recently released a new report called Advancing Zero Trust Maturity Throughout the Network and Environment Pillar. For background context, Zero Trust has 7 pillars: 1. User 2. Device 3. Application/Workload 4. Data 5. Network & Environment 6. Automation and Orches

Securing Machine Data Capture in OT Environments
In this post, we explore how to secure Machine Data Capture within Operational Technology (OT) environments. Highlighting its significance and relevance, we look at how Machine Data Capture serves as a cornerstone for informed decision-making and operational efficiency in various industries. However

Enhancing Security and Control: Third-Party Remote Access Strategies for Critical Infrastructure Networks
With third-party access, security teams face the challenge of making decisions about who, what, and how external partners, vendors, or contractors requiring network access for collaboration or service provisioning, will get it. VPNs have been the staple of Remote Access security, but networks have g
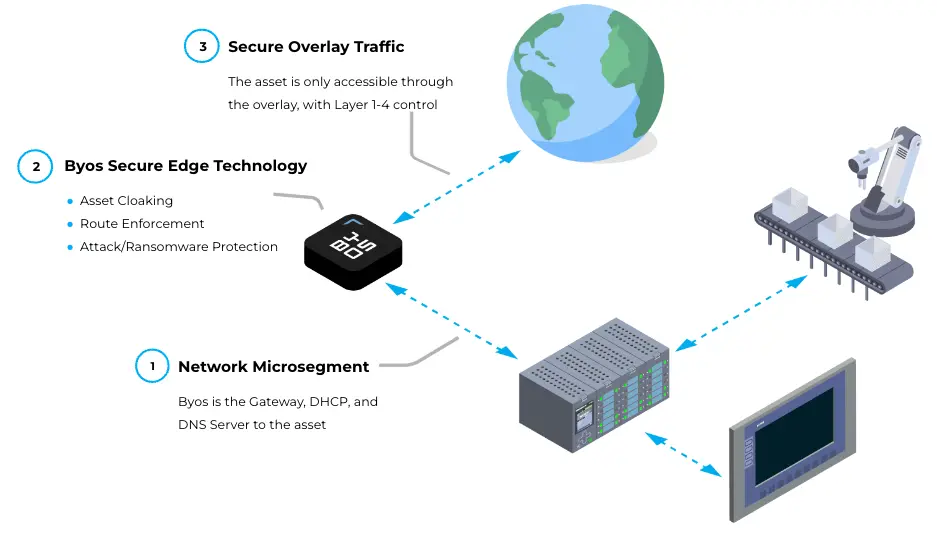
Remote Support for Your OT Network Without the Risk
The rise of remote support of robots, industrial controls, sensors and other plant floor systems is transforming OT. Most organizations find that securing access inhibits the process of providing remote support services. The issues revolve around a couple of important considerations: 1. How does an

Plant Floor Agility - Securely Connecting Legacy Assets
Over the last decade or so, OT has painfully learned that IT integration and security methods need to be adjusted significantly to adapt to the OT world. OT has significantly different business drivers, assets with different operational requirements, and different technical underpinnings. One of the

CISOs’ 12 Biggest Network Security Challenges
To gain an understanding of the challenges CISOs face, Byos interviewed 100 security leaders in major organizations and compiled their 12 biggest issues.

Network Threats: How to Detect and Prevent the 5 Most Common Attacks
Learn about the five most common network threats and develop strategies to detect, prevent, and mitigate cyberattacks.

How to Prevent Malware Attacks
This article reviews what malware is, explores the different types of malware, and explains how to prevent malware attacks.

IoT Attacks: 6 Security Risks To Be Aware Of
IoT attacks take advantage of both inherent vulnerabilities in IoT devices and their role in organizations’ broader network infrastructure.
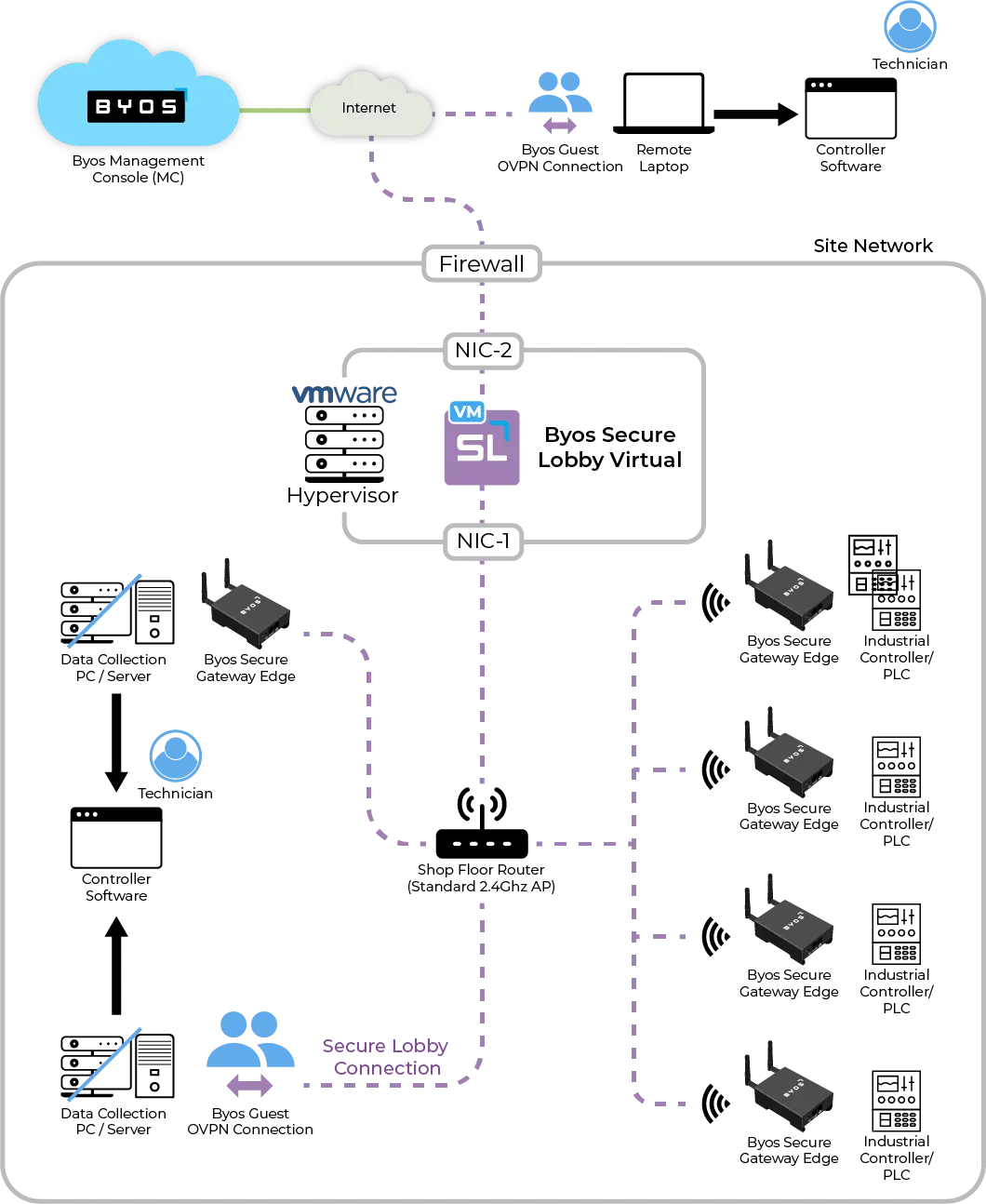
Advancing Network Security in Manufacturing: Exploring a solution for challenges caused by hybrid Static IP and DHCP environments
Uncover the complexities of securing manufacturing networks with static IP configurations and the transition to DHCP.

How to Protect Against Rogue Access Points on Wi-Fi
This article provides a complete overview of the cyber threat and explains how to protect against rogue access points.

Denial-of-Service (DoS) Attack Prevention: The Definitive Guide
After reviewing the fundamentals, this article outlines the current best practices for denial-of-service attack prevention.

Limiting the Blast Radius - Preventing Lateral Movement is Absolutely Critical
A detailed exploration of lateral movement tactics outlined in the MITRE ATT&CK framework, and best practices for detecting and preventing lateral movement

Preventing Attackers from Gaining Initial Access to Your Network
The best way to mitigate damage is to prevent attacks before they happen. Learn how to prevent initial access attacks inside.
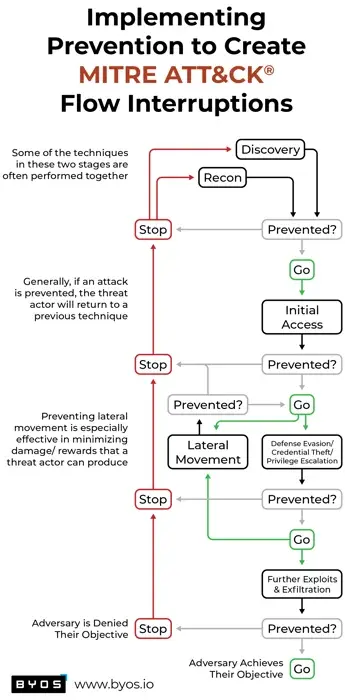
Turning the Tables on Bad Actors' Reconnaissance & Discovery Practices
The MITRE ATT&CK framework reveals adversaries’ attack chains so we can identify the “choke points”, where defenders can be in a position of power

How Cyber Defense Complexity Opens the Door Wide to Cyber Adversaries
Complex security architecture can open additional vectors for attack. Discover how simplicity can improve your organization’s approach to cyber defense.
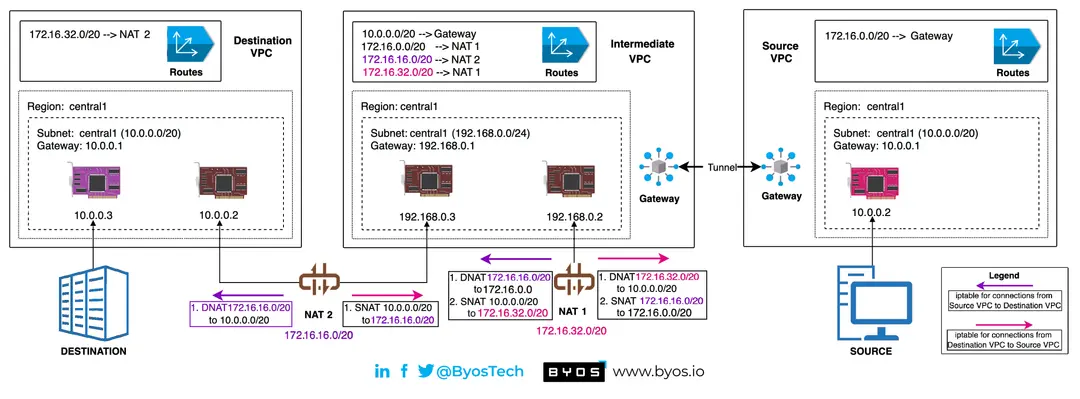
DNAT and Security in Industrial Networking
Trying to deploy DNAT across a multi-site industrial network is an immense, complex challenge. We believe in a better approach to Industrial Networking.

How Cyber Adversaries Attack Each of the OSI Layers 1-7
Learn how to recognize different types of cyber attacks using the seven layers of the OSI model.
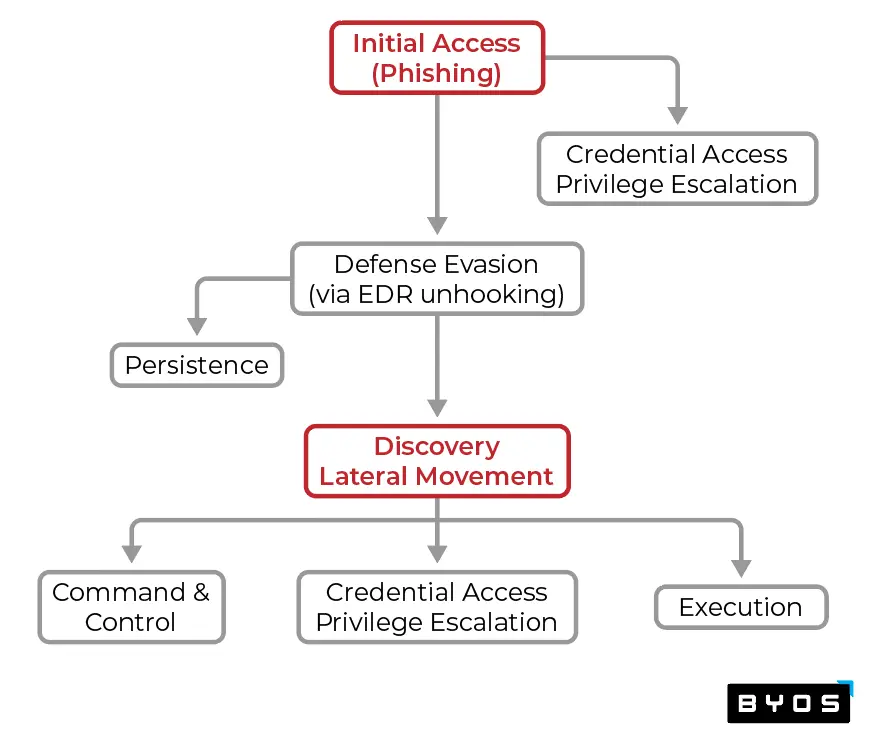
Preventing Cyber Attacks is Better than Detect and Respond - The Trick is How to Prevent
Proactive, preventative technologies and methods greatly improves the outcomes and effectiveness in a more balanced defense-in-depth strategy

Internet Security: How Vint Cerf Might Do It If He Could Start Over
Learn what Vint Cerf would do if he could design the internet all over again, and how his findings can help your organization improve its security posture.

Adversaries' Evasions are Growing Faster than Defenders' Detections - Part 2
This second part in an ongoing series frames how our adversaries think so you can make your defense strategy more effective

Adversaries' Evasions are Growing Faster than Defenders' Detections - Part 1
Why is defense evasion growing faster than defenders can detect new techniques? We cover how to bridge the increasing gap between us and cyber adversaries

What Is Operational Technology (OT) Cybersecurity?
What is OT cyber security? Check inside to discover what it is, along with common threats and vulnerabilities OT systems must defend against.

What Is Manufacturing Cybersecurity?
From unpacking questions like, “What is manufacturing cybersecurity?” to providing a cybersecurity strategy development plan, here is a primer for cyber security in manufacturing.

Industry 4.0 Blog #5: Wrap-up and Resources for Your Success
Complete list of resources and articles for a successful OT security program and Industry 4.0 digital transformation initiative

3 of the Biggest Cybersecurity Threats Facing the Manufacturing Industry
Manufacturing is one of the most targeted industries in the world by cybercriminals. Read to learn the top three cybersecurity risks for the manufacturing sector.

Industry 4.0 Blog #4: Controlling Third Party & Remote Access to OT
This blog explores the issues and tradeoffs for securing remote access, and provides a roadmap to prioritize how you build your operational security plan

The Big List of Manufacturing Cybersecurity Statistics + Infographic
The latest manufacturing cybersecurity statistics show it’s the most-targeted industry for attacks. Here’s how to proactively prevent downtime.

Industry 4.0 Blog #3: Hardening the OT Network
We address how to “harden the network” - putting the controls and protections in place to make the network much more resistant to malicious intent

Cybersecurity for Chemical Manufacturing: 5 Unique Considerations
Implementing cybersecurity for chemical manufacturing requires understanding its potential blind spots. Discover the most essential considerations inside.

Industry 4.0 Blog #2: Visibility & Security Coexisting in Manufacturing
Getting both security and simplicity of use is rare - adding more layers of security often ends up adding more complexity. Discover how to get both here

How Big Is the Operational Technology (OT) Security Market?
The operational technology security market is growing rapidly across many categories. What does that mean for your business? Read on to find out.

Industry 4.0 Blog #1: Digital Transformation
Industry 4.0 digital transformation is increasingly gaining momentum. Read this to get a step by step guide to successfully implementing your OT initiative.

11 of the Most Useful & Effective OT Network Security Vendors Currently
OT network security has become a must-have in the industrial sector. Here are the top vendors helping manufacturers protect their OT assets.

OT Network Security: What Manufacturing Executives Need to Know
Struggling with the unique challenges posed by OT network security? Learn how your organization can create an effective OT security strategy.

On Zero Trust: Modern Cybersecurity’s Most Misused Phrase
The term “Zero Trust” is often misused. Read here to find out what it is, how it works, and how your company can implement it.
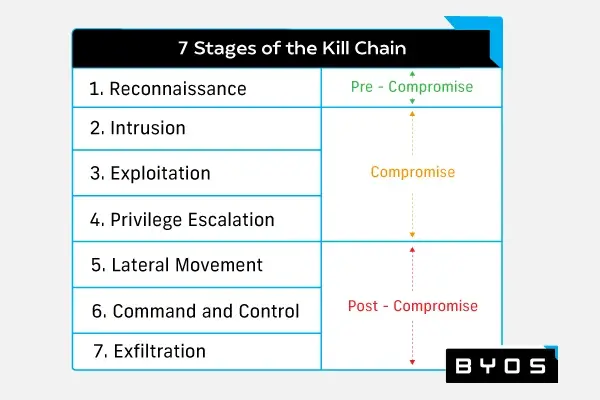
Malware Protection: Everything IT Pros Need to Know
The first step in protecting your network from malware is understanding the scope of a potential attack. Learn what you need to know about malware protection.

Enterprise Malware Removal: 4 Steps to Take Once You’ve Been Compromised
If your company is the victim of a cybersecurity event, follow these steps for effective enterprise malware removal, communication strategy, and recovery.

Malware Protection: How to Build the Ideal Tech Stack
From endpoint security to microsegmentation, this article explains how your security team can assemble a comprehensive malware protection solution.

The Ultimate List of Cybersecurity Statistics
From security trends to cybercrime rates, this article puts all the critical cybersecurity statistics and major events from the last four years in one place.

The 10 Types of Malware Every Security Pro Needs to Know
Cybercrime is on the rise globally with more and more types of malware in use. Security professionals need to understand each and how they work.

Answering 3 Common Questions About Microsegmentation for Industrial IoT Security
Industrial IoT security poses unique challenges — here are our answers to common questions about microsegmentation in the world of IIoT.

IoT Security: What Network Professionals Need To Know
The rise of the Internet of Things has also given way to new IoT security threats. Here’s what network pros need to know about common threats and how to mitigate them.

IIoT Vulnerabilities: How to Protect Your Networks Against 3 Common Threats
This article shows how organizations can boost their industrial IoT security by protecting networks against its most common vulnerabilities.

4 IoT Device Security Best Practices for Every Organization
As more smart devices and internet-connected equipment enter the workplace, IT departments must prioritize IoT device security.

3 Malware Mitigation Techniques For Keeping Cyber Attacks Contained in 2022
No network can completely escape compromise. This article explores the latest malware mitigation techniques.

Edge Microsegmentation Startup Byos Appoints New Chief Operating Officer
Former SVP and GM at Atmel, Rob Valiton join the company to double down on go-to-market efforts

Byos Launches the Byos Secure Gateway Edge™ With Secure Lobby™ to Bring Zero Trust Security and Remote Access to IoT Devices
By creating a micro-segment of one for each endpoint on a network, Byos provides unprecedented security and remote management for IoT devices

Byos Announces Partnership With Insight Enterprises Inc.
Insight will sell and support the Byos Inc. family of patented plug-and-play Secure Endpoint Edge solutions built to provide secure connectivity for the remote/roaming workforce and connected devices

Enterprise Malware Protection: How to Build the Ideal Security Stack
Looking to build an enterprise malware protection stack? This article will help you navigate the provider landscape.
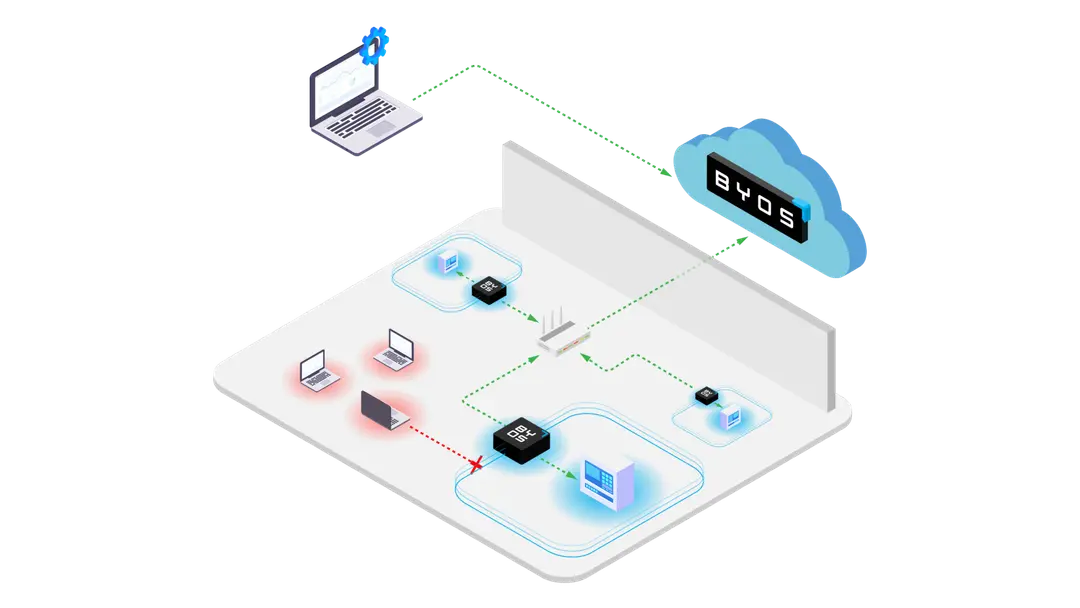
How Byos Prevents Lateral Movement In Corporate Networks
Edge microsegmentation is one of the strongest ways to protect against lateral movement. Here’s how Byos does it.

How to Prevent a Man-in-the-Middle Attack
Want to learn the latest on man-in-the-middle attack prevention? This article is your guide to the current best practices for neutralizing this threat.

3 Reasons CISOs Choose Edge Microsegmentation To Secure Their Distributed Workforces
This article explores the top three reasons CISOs choose hardware-enforced microsegmentation to protect their devices at the edge.

Microsegmentation: The Ultimate Guide
Find everything you need to know about protecting your network at the edge in our ultimate guide to microsegmentation.

A Guide To Attack Surface Reduction Through Microsegmentation
Attack surface reduction is a key element of any modern security strategy, and microsegmentation is the most powerful way to achieve it.

What Is Zero Trust Networking?
This article defines Zero Trust network security and examines how organizations can implement Zero Trust network architecture with just a few steps.

What Is Lateral Movement in Network Security?
Protect your company by understanding the techniques attackers use to move freely through infected networks without being detected.
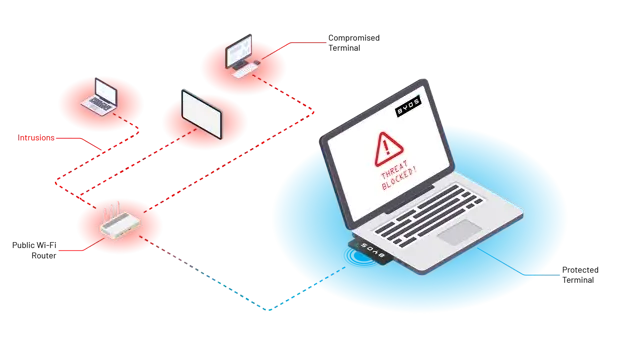
How to Prevent and Detect Lateral Movement In Your Network
Learn how to detect lateral movement and prevent attackers from strengthening their foothold in your organization’s network.

What Is Microsegmentation?
Strengthening your organization’s security posture? Our introduction to microsegmentation will get you ready to better protect your network.

Cleaning up “Dirty” Wi-Fi for Secure Work-from-Home Access
The best way to ensure that a home worker doesn’t corrupt the corporate network or otherwise expose key assets is to isolate their devices from their untrusted home Wi-Fi networks. In essence, this means micro-segmenting the remote device and creating a network of one. This step extends Zero Trust a

Securing Work from Home Wi-Fi Access
Assuming all networks are dirty is fundamental to any effective remote work security strategy such as Zero Trust. To ensure that a home worker doesn’t corrupt the corporate network, it’s crucial to find a way to isolate their devices from their untrusted home Wi-Fi networks. The answer lies in micro

RSAC Insights: Matias Katz, CEO and Founder of Byos - Enterprise Security Tech
Today’s public and private networks are by their very nature dirty. Security professionals know that and warn that we should just assume that every network carries significant risk to our devices, data and resources. At Byos, we believe that organizations need to be able to take advantage of low cos
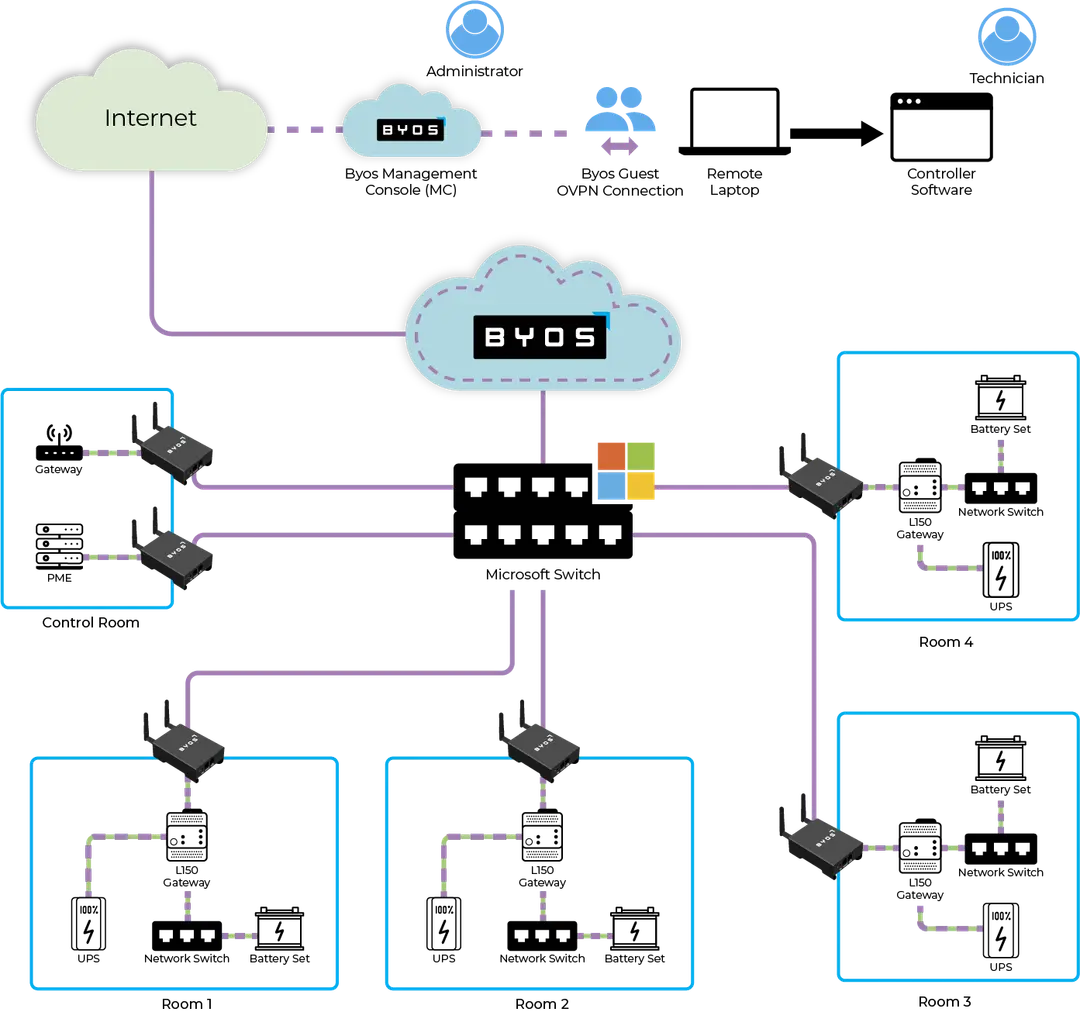
Initial Access Brokers Are Breaking Into Corporate Networks and Selling Access to Bad Actors
Understanding the traffic at the edge of the corporate network is something that network administrators have long desired since they know their devices are exposed when connecting to any network.

Closing Network Pathways to Sensitive Data to Help Secure Medical Devices
There are a few significant challenges healthcare delivery organizations face in protecting their networks from security threats. The first is the trend of the escalating frequency of vulnerabilities found in networked medical devices.

Securing Connectivity for Remote Workforces
In the ongoing Work from Home (WFH) evolution, the need to better secure employee endpoints has emerged as a main priority for CISOs. Many organizations have discovered what network and security professionals have long known: once the endpoint outside the perimeter, the level of security is degraded
Byos Caution RSA Conference Attendees, Travelers and General Public to“Dirty Half-Dozen” Public Wi-Fi Risks
Byos, Inc., an endpoint security company focused on concept of Endpoint Micro-segmentation through Hardware-Enforced Isolation, recommends caution for attendees of major conferences and events such as the RSA Conference 2020, a leading cybersecurity conference in San Francisco, February 24-28, and t
Byos Awarded Patent for Cybersecurity Protection Technology for Securing Endpoint Devices
Byos, Inc., whose award-winning solutions protect endpoints using the novel approach of hardware-enforced isolation from the risks of home and public Wi-Fi networks, announced the receipt of their Canadian patent, covering its Device and Method for Securing a Network Connection. Byos’ technology is

Defending Against Lateral Movement in the Remote Work Era
After recent events, it is clear that no organization is immune from attacks that leverage lateral movement on untrusted, dirty networks and that in the remote work era, lateral movement that requires a different approach to defend against. Endpoint Micro-Segmentation using hardware-enforced isolati

How To Better Secure Remote Wi-Fi Connections
The remote Wi-Fi networks corporate endpoints are connecting to remains a weak point in any security architecture. By giving corporate devices their own protected micro-segment of one that security teams can control, the risk posed by this new normal of remote work is greatly reduced.

Extending Zero Trust to any Remote Wi-Fi Connection
Zero Trust Network Access (ZTNA) solutions validate every access request based on the identity of the user, the device, and the context. However, the last mile security problem of exposed devices on untrusted dirty networks leave Security teams needing a way to monitor and control their remote devic

Protecting Remote Workers from Dirty Networks - TAG Cyber
“It’s imperative to protect mobile employees using dirty networks—public Wi-Fi in coffeeshops, at airports, in hotel lobbies—and all networks should be considered compromised. Even if your organization has a VPN, the devices on those networks are exposed. An attacker can re-route packets or throw ex

Byos pushes microsegmentation security approach to device level - The Last Watchdog
Micro segmentation takes the fundamental principle of network segmentation and drives it down to smaller and smaller subnetworks. One security vendor pushing micro segmentation just about as low as you can go — all the way to the individual device level — is a Nova Scotia-based startup called Byos

Entrevestor: CDL-Atlantic Graduates 11 Teams
Operating out of Dalhousie University, the CDL-Atlantic just finished its second cohort, which began last autumn with just over two dozen companies being mentored by some of the region’s top business leaders. The organization never reveals its participants until they graduate as the numbers dwindl
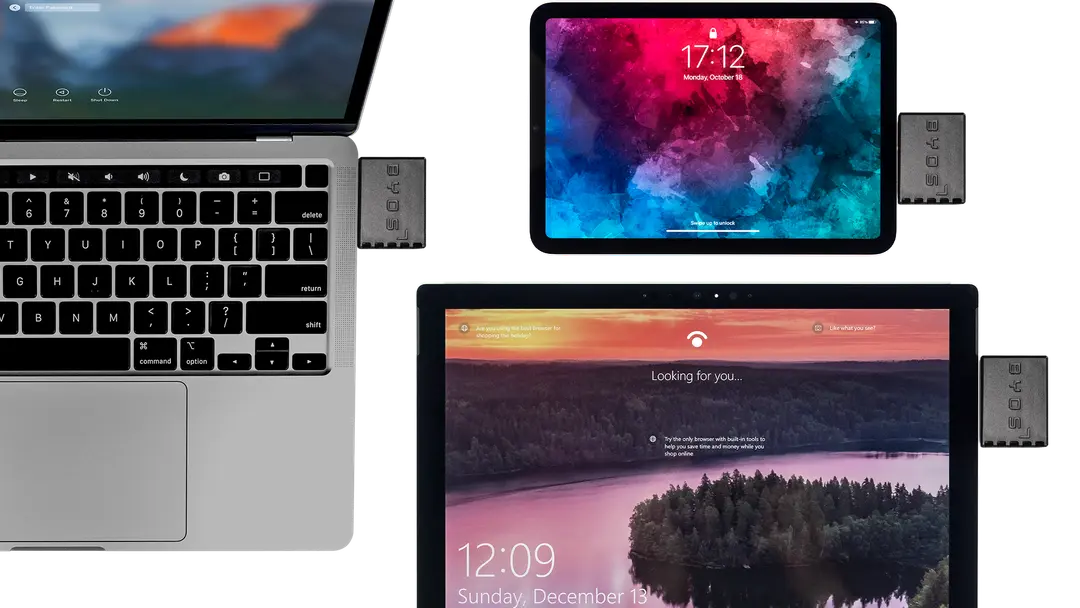
Byos Brings New Security to Remote Networking, Enabling Zero Trust Access on Any Remote Wi-Fi Connection
Discover how Byos secures Users and Their Organization’s Network Against Attacks that VPNs Can’t Protect Against

Byos at DemoCamp HFX
Byos demoed the Byos Secure Endpoint Edge™ and Management Console™ at DemoCamp HFX.

How to Secure the Work From Home Initiative
Exploring fundamentals for establishing a baseline of home Wi-Fi hygiene and comparing strategies for securing the Work From Home (WFH) initiative. Compared to setting up a more secure Home Wi-Fi network using traditional Network Segmentation techniques, Endpoint Microsegmentation using Byos µGatewa

Three Ugly Work From Home Wi-Fi Security Realities
Many experts agree that security teams aren’t ready for the spike in employees working on their home networks. Attacks on employees working from home are likely to increase as threat actors adjust their tactics to this new reality. IT Security teams should be aware of the following when supporting w

The Half Dozen Risks of Using Dirty Public Wi-Fi Networks
Wi-Fi Networks, whether public or private, are by their nature insecure and dirty. In fact, security professionals know that we should just assume every network carries inherent risk to our devices, data and resources we access. These are half dozen risks of using dirty public Wi-Fi networks.

Byos Introduces Endpoint Microsegmentation Solution to Extend Zero Trust Access to Any Remote Wi-Fi Connection
Today Byos Inc. introduced its first plug-and-play security product that protects endpoints from threats on local Wi-Fi networks through endpoint micro-segmentation.

Byos' Endpoint Solution Wins 2020 Cybersecured Award for Best WFH/VPN Security Technology
First Solution to to Extend Zero Trust Access to Any Remote Wi-Fi Connection Protecting Users and Organizations from Security Risks in Unmanaged and Unprotected Home/Public Wi-Fi Networks HALIFAX, NS, December 22, 2020 – Byos, Inc ., the endpoint micro-segmentation company dedicated to helping

Byos Bug Bounty #2 - Hardwear.io HardPWN 2019
Our second Bug Bounty event took place at the Hardwear.io conference from Sept. 23-27 in The Hague, Netherlands, during the HardPWN Hacking contest. Read more here.

Byos Bug Bounty - Vegas 2019
e first of three Bug Bounty events held in Las Vegas, NV during the week of BlackHat and DEF CON. Over the course of 3 days, more than 20 security researchers from North America, South America, and Europe participated, trying to crack the Byos µGateway.
Platform
Use Cases (Industry)
Use Cases (Application)
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)

