🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
All you need to know about Byos
Short Demo Video


See what Byos can do in just 5 minutes!
Full Platform Demo


Want to see more? Request a personalized Demo from one of our Solutions Engineers.
Looking for something else?



Short Videos
Watch short videos on specific capabilities of our Platform



Long Videos
Watch long-form videos on popular Platform Use Cases
Explore Our Data Sheets
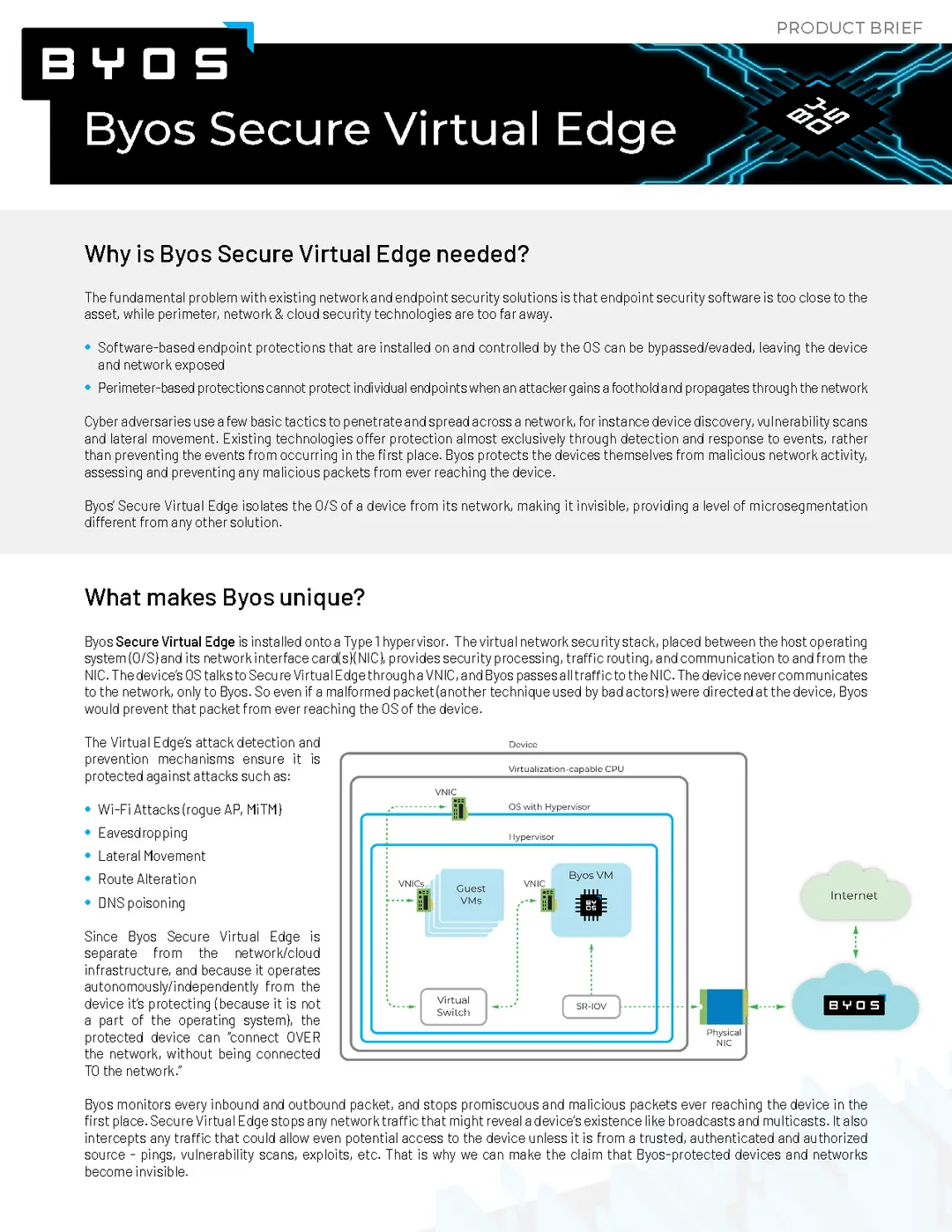


General Byos Resources
White Papers, Market Analysis, and Product Comparisons



Product Solution Overviews
Specifics of the Byos Secure Networking Platform Components



Use Cases
Learn how Byos' solutions can solve your specific challenges

Get the Guide
Check out our Network Threat Prevention Guide
Check out our latest Blog posts
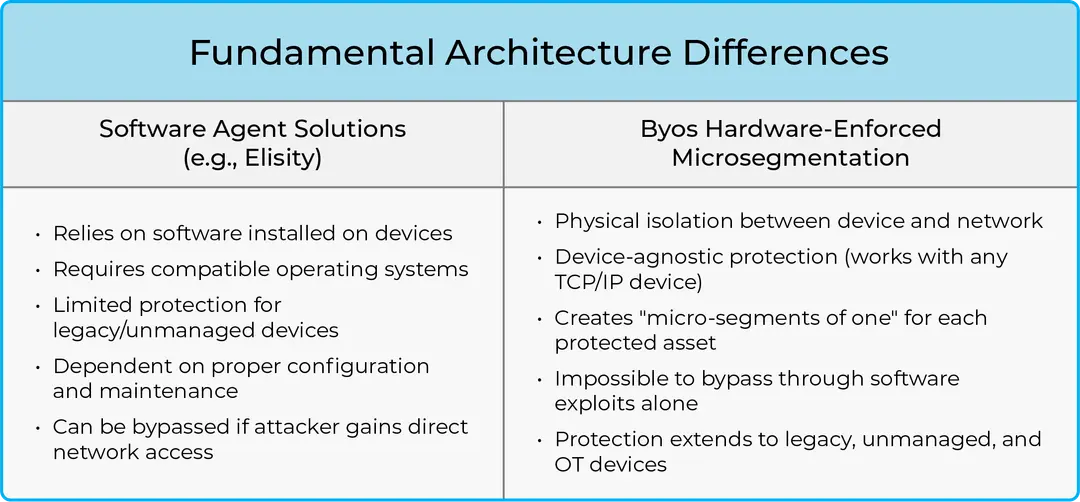
Byos vs. Software-Agent Microsegmentation: Two Paths Toward Zero Trust
Software-based microsegmentation has limits. This blog explores how Byos’ hardware-enforced approach creates true "microsegments of one," providing protection for any device—even those that can’t run agents.
See Our Latest Blog Posts
Read expert takes, latest insights, and cybersecurity trends on our blog.
Download the Byos Secure Edge app
Get the App to make using your Secure Edge™ easier

macOs

Windows

iOS
Download Wallpapers
Platform
Use Cases (Industry)
Use Cases (Application)
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)