IIoT Security
How Byos can help protect your connected industrial devices
The advent of Industry 4.0 has given rise to a variety of technology advances and opportunities. One of the key themes of the fourth industrial revolution is interconnection, with machines, devices, sensors, and people all working together via the Industrial Internet of Things (IIoT). This presents network administrators and CISOs with new challenges: keeping the devices on their networks safe from malicious attackers.
On top of that, the modern distributed workforce means that employees are often connecting remotely to IoT devices from public and home Wi-Fi networks, increasing the attack surface and thus cyber risk. As the Industrial Internet of Things continues to expand, network administrators and CISOs need security technologies that combine security and remote access, without the historical challenges of complex deployments and excess overhead. Byos can help. Click the button below to request a demo or read on to learn more.
IIoT Security Devices
What is IIoT security?
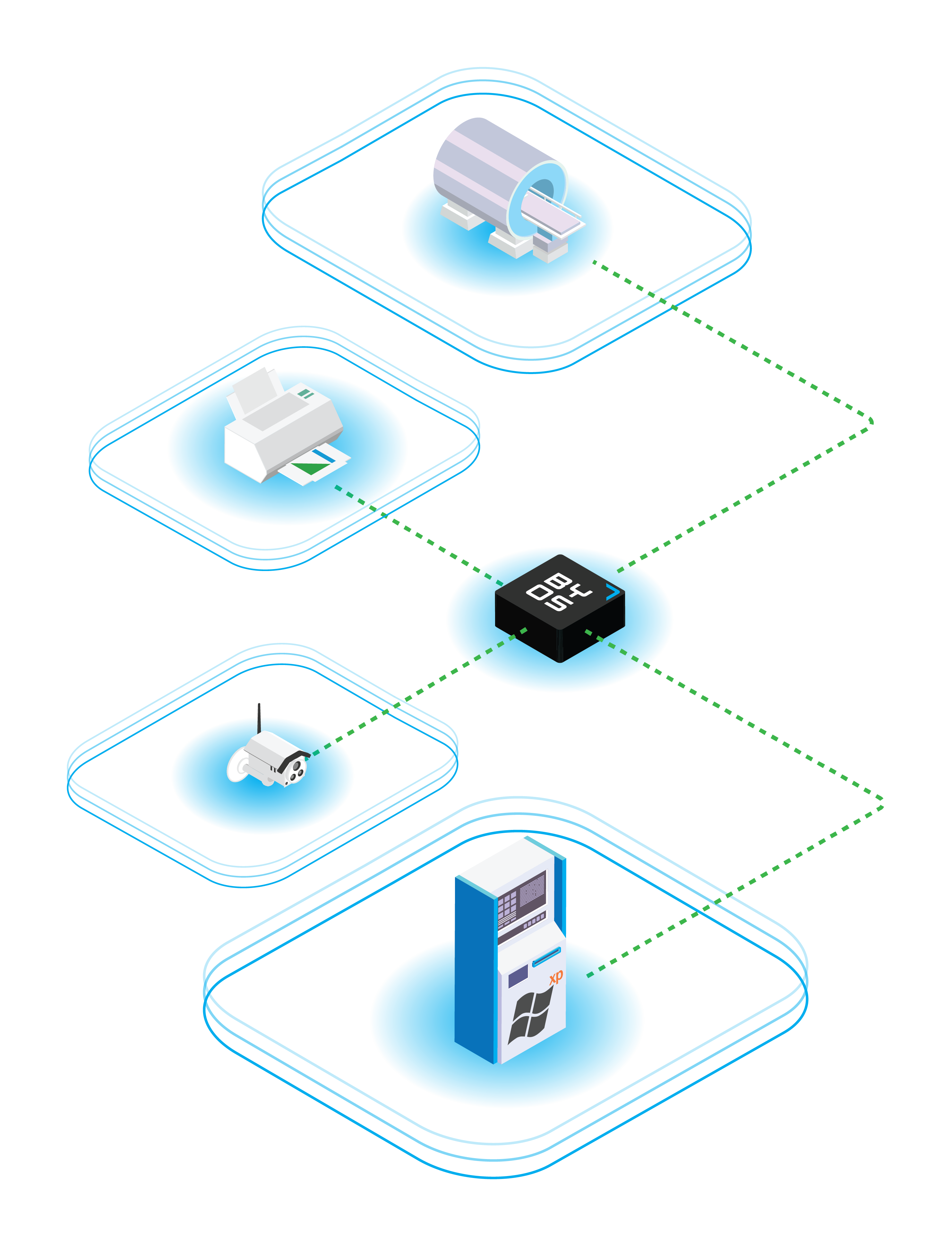
IIoT security allows CISOs, network administrators, and OEMs to protect and manage the connected device endpoints on their network. This includes:
- IIoT endpoints: The use of internet-connected devices for everything from data analysis to predictive maintenance means more endpoints to potentially become targets of attacks.
- Remote connections: With remote work becoming increasingly common, many IIoT devices are now being accessed from untrusted and possibly insecure Wi-Fi networks.
- Legacy devices: Older devices are often unpatchable, introducing “low-hanging fruit” vulnerabilities.
IIoT Security Challenges
What are some challenges of securing IIoT devices?
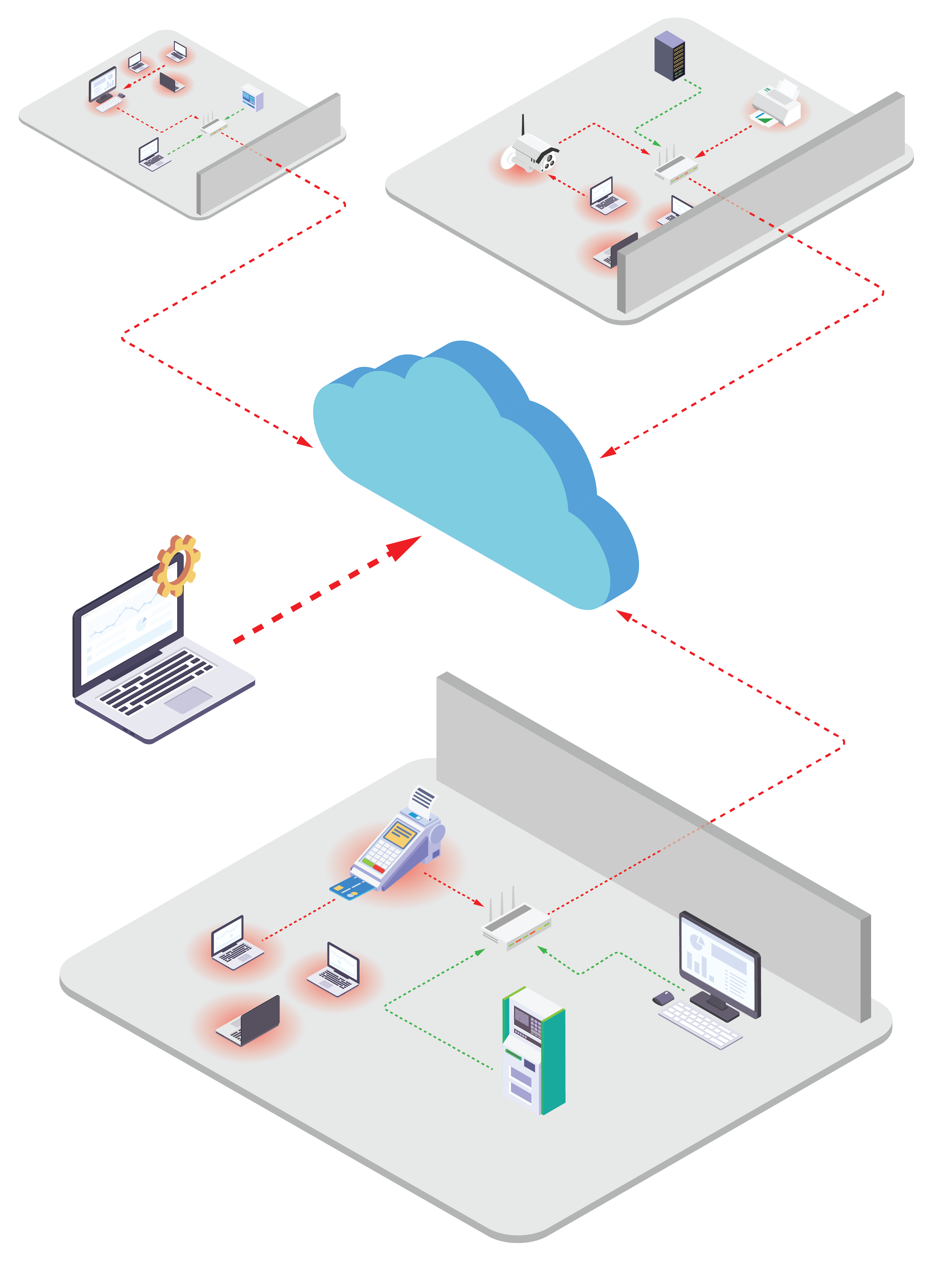
- 3rd-Party Contractor Access
- Giving technicians and contractors broad access to the network adds risk and is difficult to manage efficiently.
- Legacy systems
- When systems can no longer be patched or updated to protect against vulnerabilities, they become a security risk.
- Inconsistent network segmentation
- Strategies for limited malicious lateral movement are often inconsistently applied on the diverse array of networks used today.
- Network blindspots
- Because of the rapid growth and diversity of IoT devices and systems, monitoring and controlling the network is becoming a complex task.
IIoT Security Threats
What are some common threats to IIoT security?
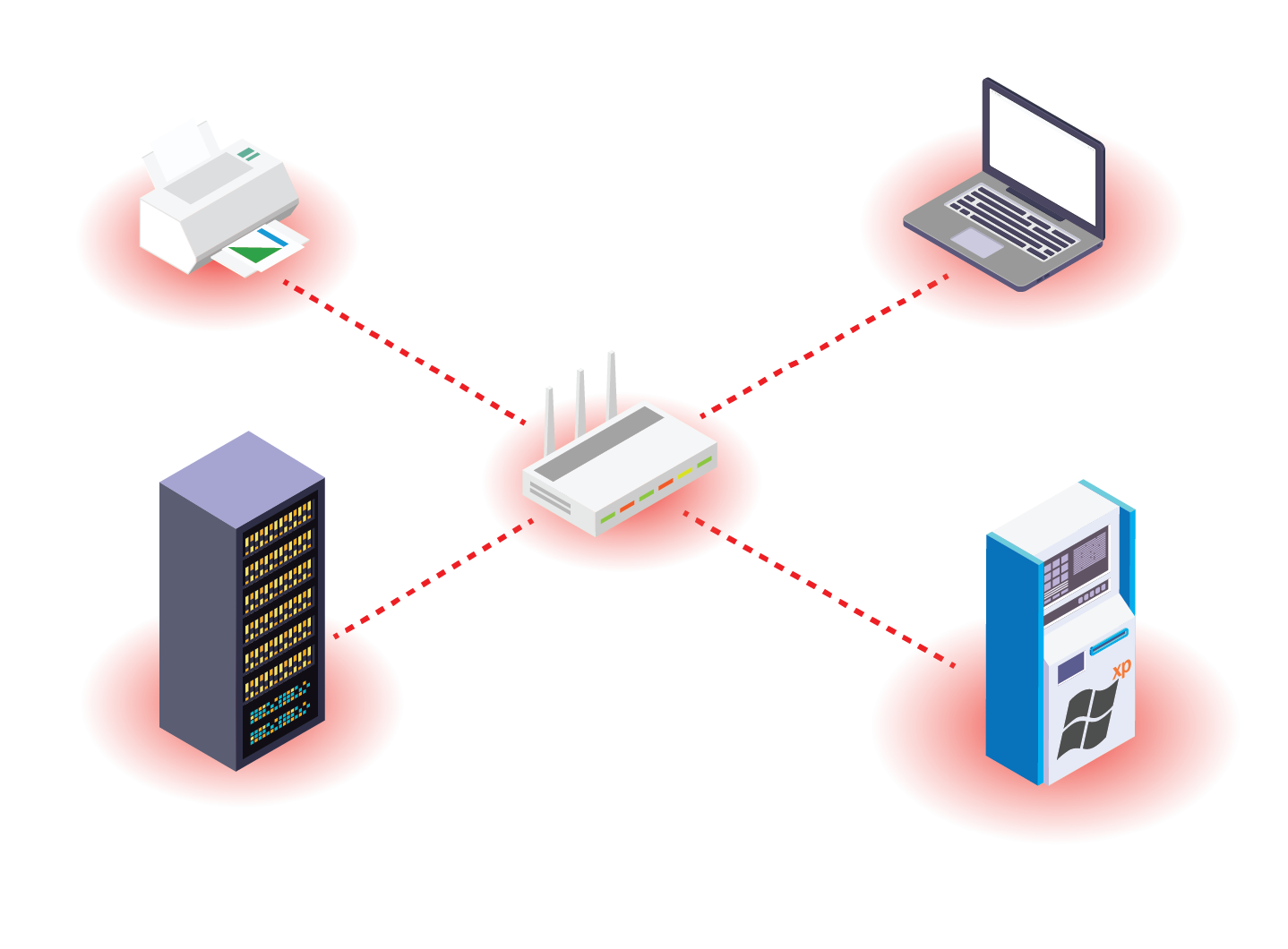
- Device hijacking:
- If endpoints or sensors are compromised, they could fall under the control of malicious actors.
- Data siphoning:
- Attackers can “eavesdrop” on network traffic and gain access to private information and proprietary data.
- DDoS attacks:
- Amazon, Github, and Bank of America are just a few of the major companies that have suffered distributed denial of service attacks. These increasingly common attacks can render services inoperable across a complete enterprise.
- Spoofing:
- When an attacker places themselves between a centralized network and an unsecured endpoint, they can send fraudulent information that appears to be coming from the endpoint.
IIoT Security Standards
Why are IIoT security standards required?
A breach in an IIoT network could have devastating consequences. These consequences range from ransomware attacks taking entire production networks down or proprietary information and data being leaked in critical infrastructure industries.
IIoT Security
How can network admins & CISOs protect their networks and devices right now?
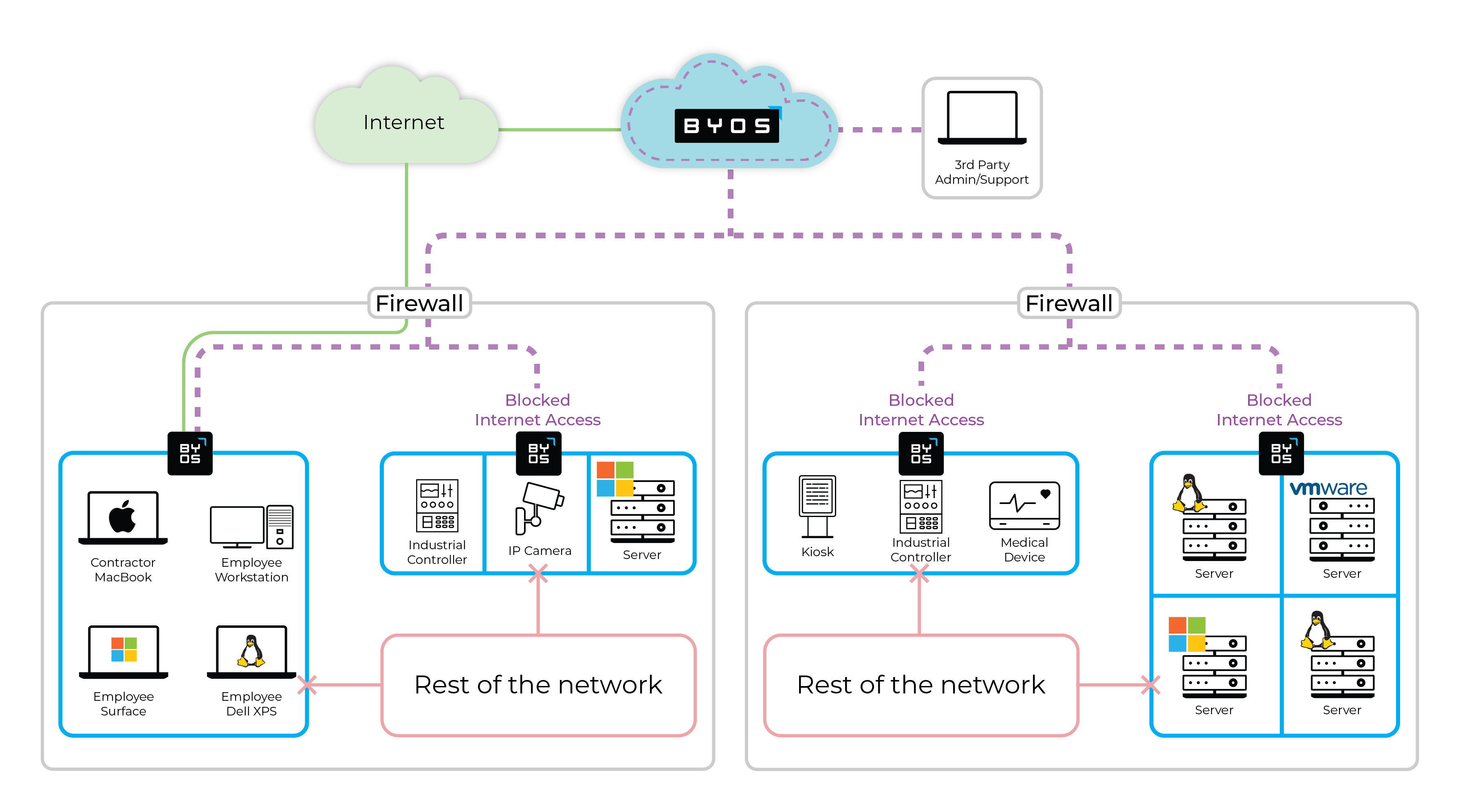
IIoT security can be challenging, but the experts at Byos can help get you up and running quickly and efficiently. The Byos Secure Gateway Edge uses edge microsegmention to secure IIoT devices, helping to meet Zero Trust security objectives. Here are a few benefits of the Byos Secure Gateway Edge:
- Legacy device protection
- Securely prolong the life of IT infrastructure running legacy applications and unsupported OS that are not ready to be retired.
- Simplify and centralize remote access
- Connecting previously air-gapped devices to the network for more efficient and secure remote maintenance and monitoring.
- Efficient incident response
- Upon detection of malicious traffic, deploy kill switches to immediately stop all traffic to specific microsegments without impacting the operations of the underlying devices
- Immediate time-to-value
- Easy deployment without needing to change to existing network configurations and without having to expose internal devices to the internet.
- Reduced attack surface
- Eliminated exposure of unpatched legacy networked devices to internal threats like lateral movement and ransomware.
- Reduced field service time
- Reduced technician trips onsite for service and maintenance saving operational expenses.

How Byos Can Help
Edge Microsegmentation for Zero Trust IIoT Security
Byos is dedicated to helping organizations protect their IoT devices against threats, vulnerabilities, and malicious attacks. Want to learn more? Click the button below to learn more about the Byos Secure Gateway Edge, or download the PDF.




