🚀 Byos Secure Embedded Edge - Back-Ordered: Reserve Yours Today
Make Your NetworkInvisibleByos Secure Networking Platform
Network Security Made Simple: Cloak assets with the Byos Secure Edge™, and easily manage your network using Byos Secure Lobby™
Redefining Your Security Approach
Secure Connectivity and OT Remote Access
Securely connect OT and legacy devices to the network, for faster data collection and better decision making.

Protect and Isolate Assets from Lateral Movement
Byos shrinks the attack surface, limits lateral movement, and minimizes the blast radius of any attack.

Simplified Granular 3rd-Party Access Control
Allow 3rd-parties into your network to specific assets without adding exposure risk to the rest of the network.

Features
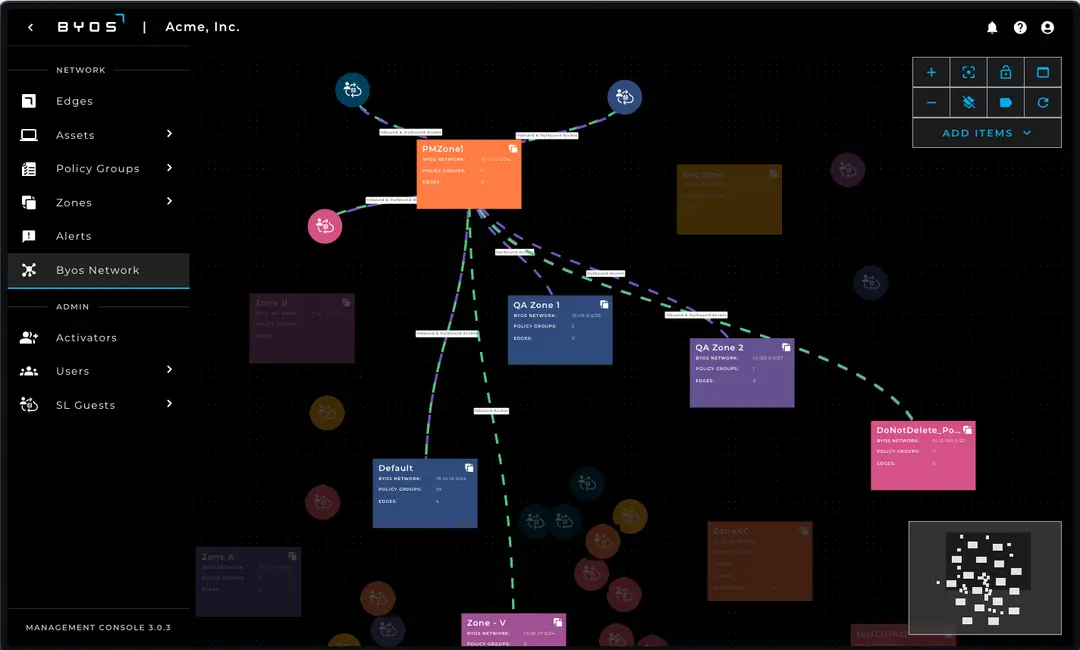
Byos Network Map
View all of your Edges and connected Assets in the Byos Secure Lobby™ Overlay network. Control and Manage access control traffic rules, asset visibility, and third-party access from a single screen.
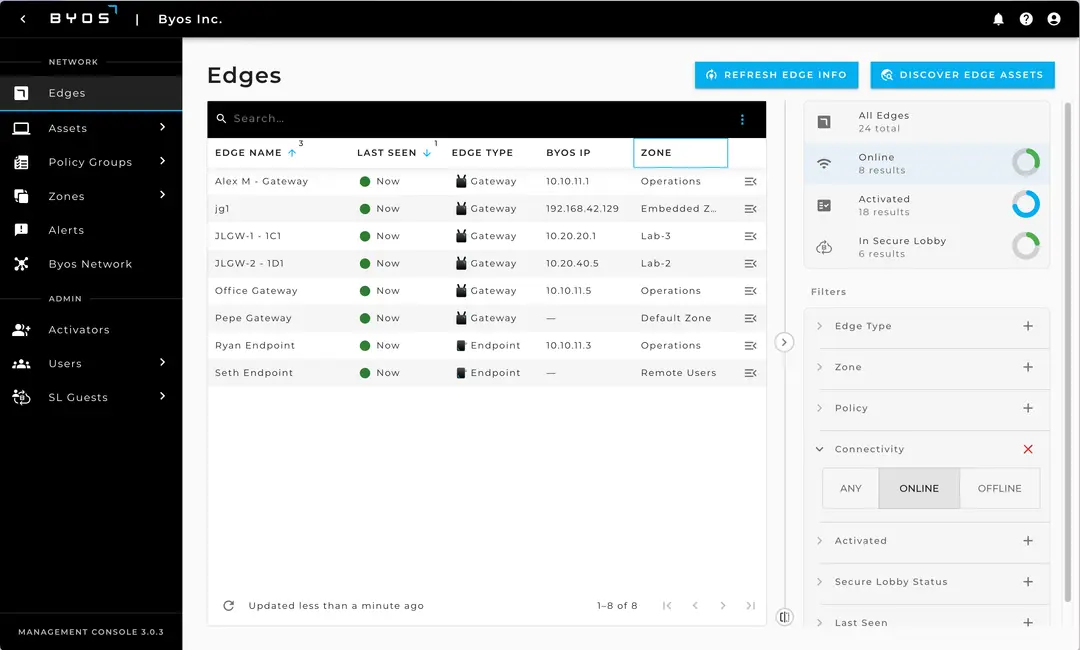
Central Edge Management
Manage your fleet of Byos Edges centrally with real time policy provisioning and enforcement, regardless of the underlying network.
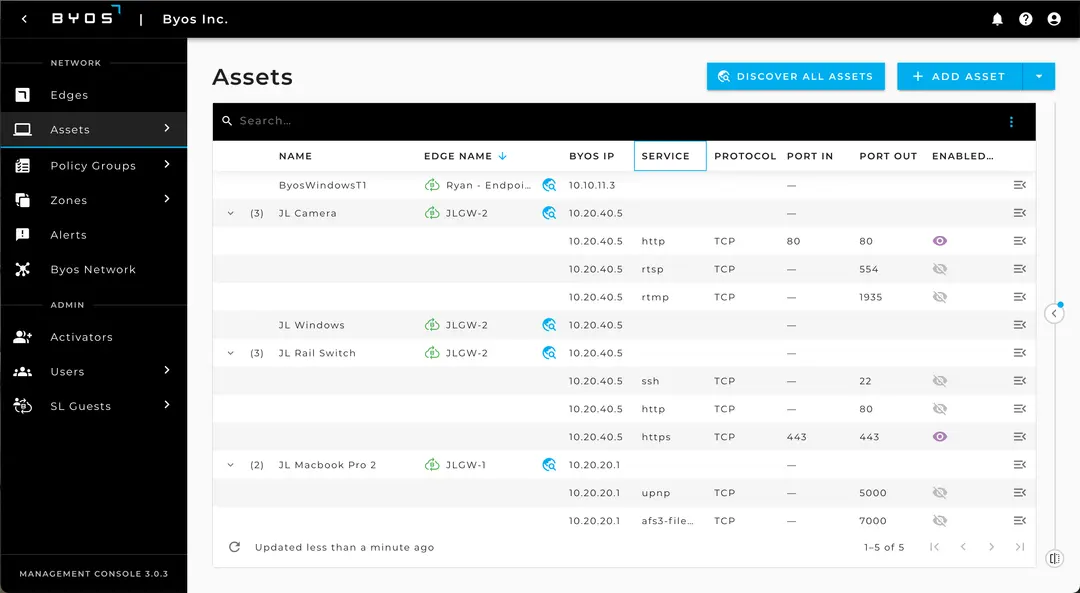
Granular Asset Control
Automatically discover and precisely control access to all Assets connected to Byos Edges. All of the access control, none of the exposure!
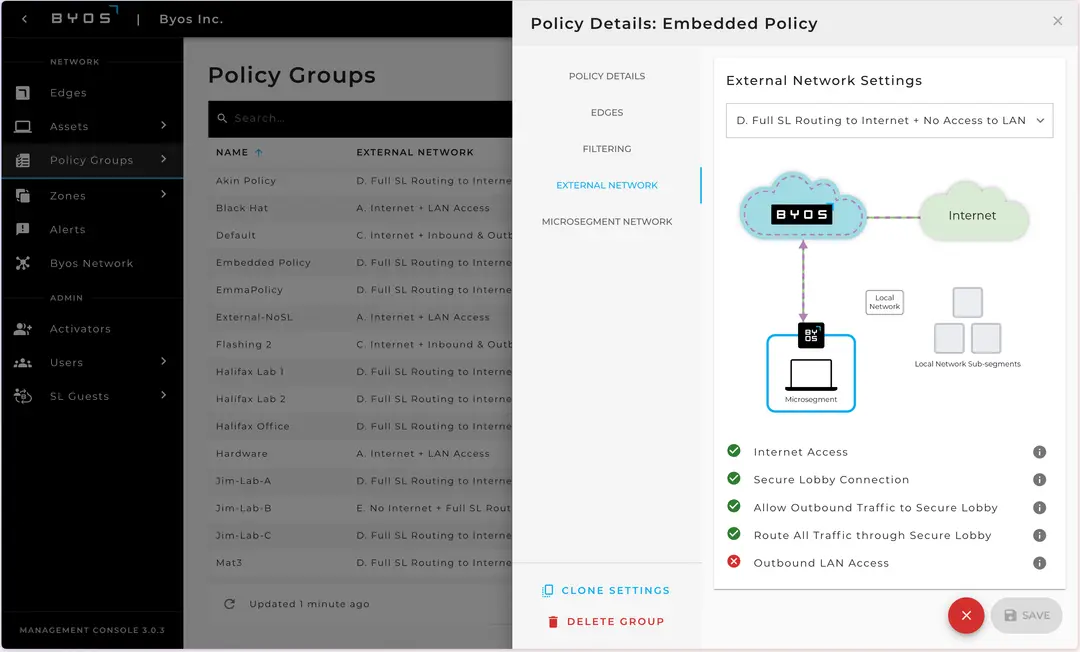
Customizable Route Enforcement
Determine how Assets can route to the network with flexible Edge Routing Policies - full vs. split tunnelling, internet access or not, or regular clean TLS traffic.
How The Platform Works


FAQ
Resources
Stay updated with all our news and the latest contributions in the industry!


