Industrial Control System (ICS) Security
How to protect your industrial control systems
Cyberattacks on critical infrastructure have been on the rise around the world in recent years. In 2010, the infamous Stuxnet worm was deemed responsible for causing potentially catastrophic damage to the centrifuges used in Iran’s nuclear program. In 2015, the BlackEnergy attack left hundreds of thousands of homes in Ukraine without power, in sub-zero temperatures, in the first known outage caused by malware. 2021 saw large-scale attacks on major insurance companies like CNA Financial Corp. and oil infrastructure like Colonial Pipeline.
In today’s world, industrial control systems are increasingly converging with IT networks and are no longer air-gapped and separated from the internet; instead, standard operating procedure has Industrial Control Systems (ICS) devices networked in order to better share and transmit data. As the industrial control systems that support critical infrastructure are increasingly online, CISOs will need to more efficiently secure those systems without interrupting operations or incurring excess overhead. Byos can help. Click the button below to request a demo, or read on to learn more.
ICS Security Devices
What is ICS security?
ICS security allows CISOs, network administrators, and OEMs to protect and manage the digital devices designed to execute industrial processes on their network. These can include:
- Industrial automation and control systems: IACSs are basic systems that rely on a combination of sensors, hardware, and software communicating and sharing information to contextualize and give meaning to individual data points.
- Programmable logic controllers: PLCs are single unit ICSs that can store instructions for making decisions and monitoring inputs in their programmable memory. PLCs are often networked to share information, but each one is considered an ICS on its own.
- Remote terminal units: RTUs are microprocessors that remotely monitor and control the field devices that eventually connect to broader control systems like SCADAs, for example. Like PLCs, RTUs can support multiple inputs and outputs.
- Human-machine interfaces: HMIs are the technology (either hardware or software) that allow operators to interact with controllers and ICSs. Examples of HMIs include control panels with simple buttons and industrial computers with full graphics displays.
- Supervisory control and data acquisition: SCADA systems apply operational controls to the data gathered and processed by their networked devices. SCADAs can report threats and alerts in real-time to the appropriate security teams for resolution.
- Distributed control systems: DCSs decentralize the intelligence collected from various devices, distributing the responsibility of deployment and control to counteract the vulnerabilities that come from many individual ICSs’ positioned controls.
ICS Security Vulnerabilities
What are some common ICS security vulnerabilities?
- Internet-exposed devices: Connecting ICSs to the internet without implementing appropriate security measures can create vulnerabilities and backdoors that allow attackers to access the ICS environment.
- Relying on default configurations: Default ICS configurations don’t typically offer sufficient security, but companies don’t always have the resources to address patches and create policies to reconfigure those devices.
- Weak segregation between IT and OT: Strong segregation between environments is a critical step to stop attacks from spreading from the IT network into OT systems and the ICS devices they support.
- ICS application weaknesses: ICS and HMI applications can be particularly vulnerable to attacks like credential sniffing, session hijacking, parameter manipulation and SQL or command injection.
- Insufficient security training: Employees can easily fall victim to all kinds of attacks (like social engineering and phishing, for example) if they haven’t been trained to develop basic security awareness.
IIoT Security Threats
What are some common ICS security threats?
Because they underlie critical infrastructure, industrial control systems are particularly appealing to cyber attackers. The day-to-day importance of oil and gas companies, water utilities, and manufacturing plants, for instance, positions ICS environments as high-value and lucrative targets in the eyes of bad actors. Popular ICS security threats include:
- Malware attacks: It’s easy to transfer malware on media storage devices as employees move between the office and the ICS environment; Stuxnet was first introduced at Siemens when an employee used an infected USB drive.
- Denial of service attacks: ICS systems rely on high availability in order to function, so interruptions are incredibly costly. DoS attacks on individual components (like PLCs) or on wired or wireless ICS connections can cause major operational interruptions.
- Third-party breaches: When organizations outsource their ICS support, the vulnerabilities that providers experience transfer to their clients. Without any control over a provider’s infrastructure, client companies are at the mercy of that third party’s security.
- Insider attacks: Employee behavior can lead to insider attacks regardless of whether or not the malpractice is malicious. Disgruntled employees, employees receiving payments or bribes, and employees without security training can all pose serious threats.
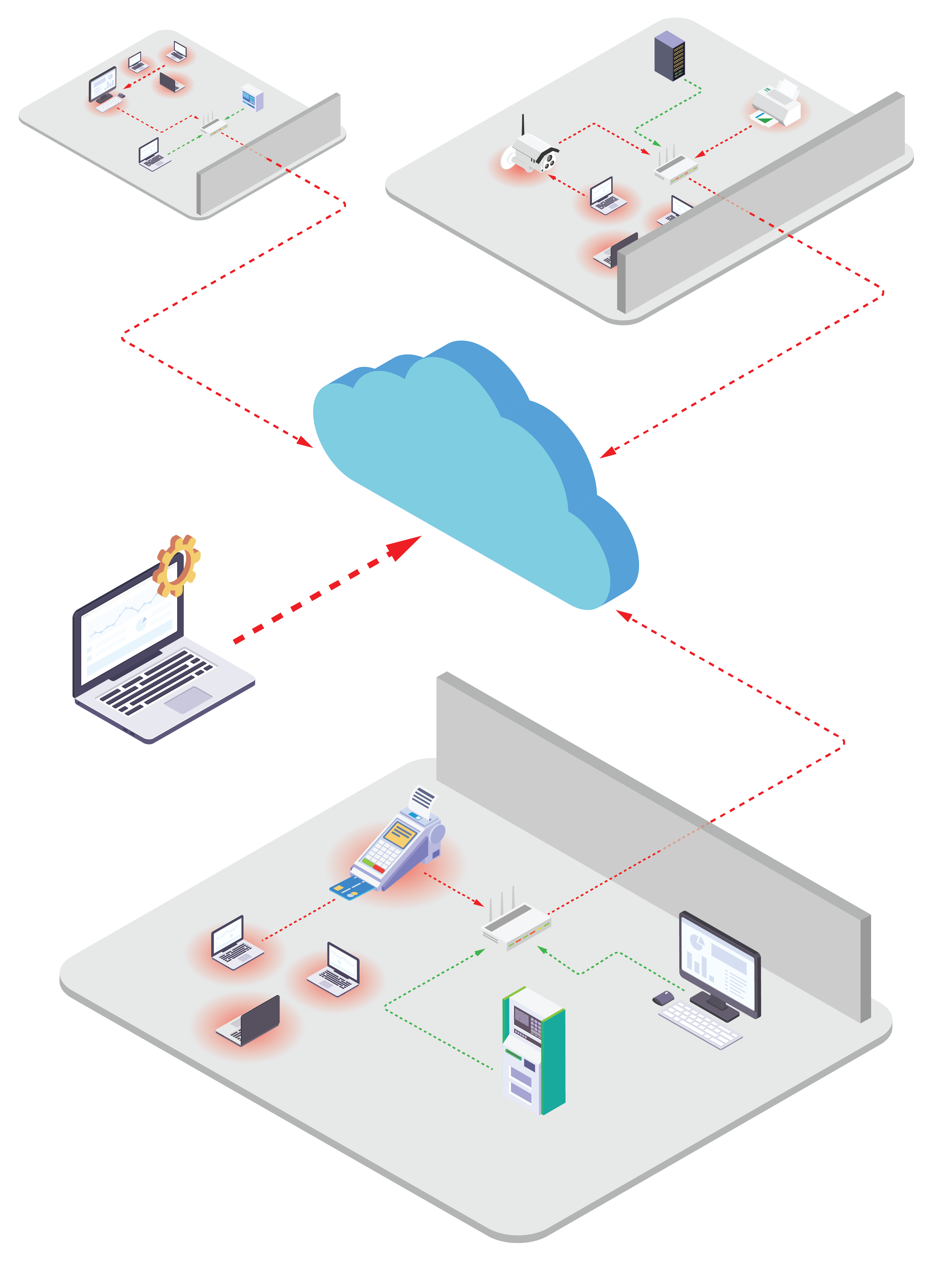
ICS Security Challenges
What are some challenges of securing ICS devices?
- Proprietary ICS protocols are insecure and unpatchable: Standard ICS protocols are often missing security basics like access control and encryption, and many can’t be updated. That makes them ineffective at stopping bad actors from accessing the data flowing between devices and their operators.
- 3rd-Party Contractor Access: 3rd-party Contractors and OEMs often need access to the devices for monitoring and servicing, but giving broad access to the network adds security risk and is difficult to manage efficiently.
- Critical infrastructure requires high availability: Because availability and uptime are crucial for the ICS devices that underlie critical infrastructure, manufacturing plants, etc., it can be difficult to take devices offline long enough to install patches and run security updates.
- Detection methods supercede a prevention approach: The high availability requirement of ICS devices pushes security teams toward an approach focused on detection instead of prevention, which means waiting for an attack to occur before it can be addressed instead of stopping it from happening in the first place.
ICS Security Installation
How can network admins & CISOs protect their ICS networks and devices right now?
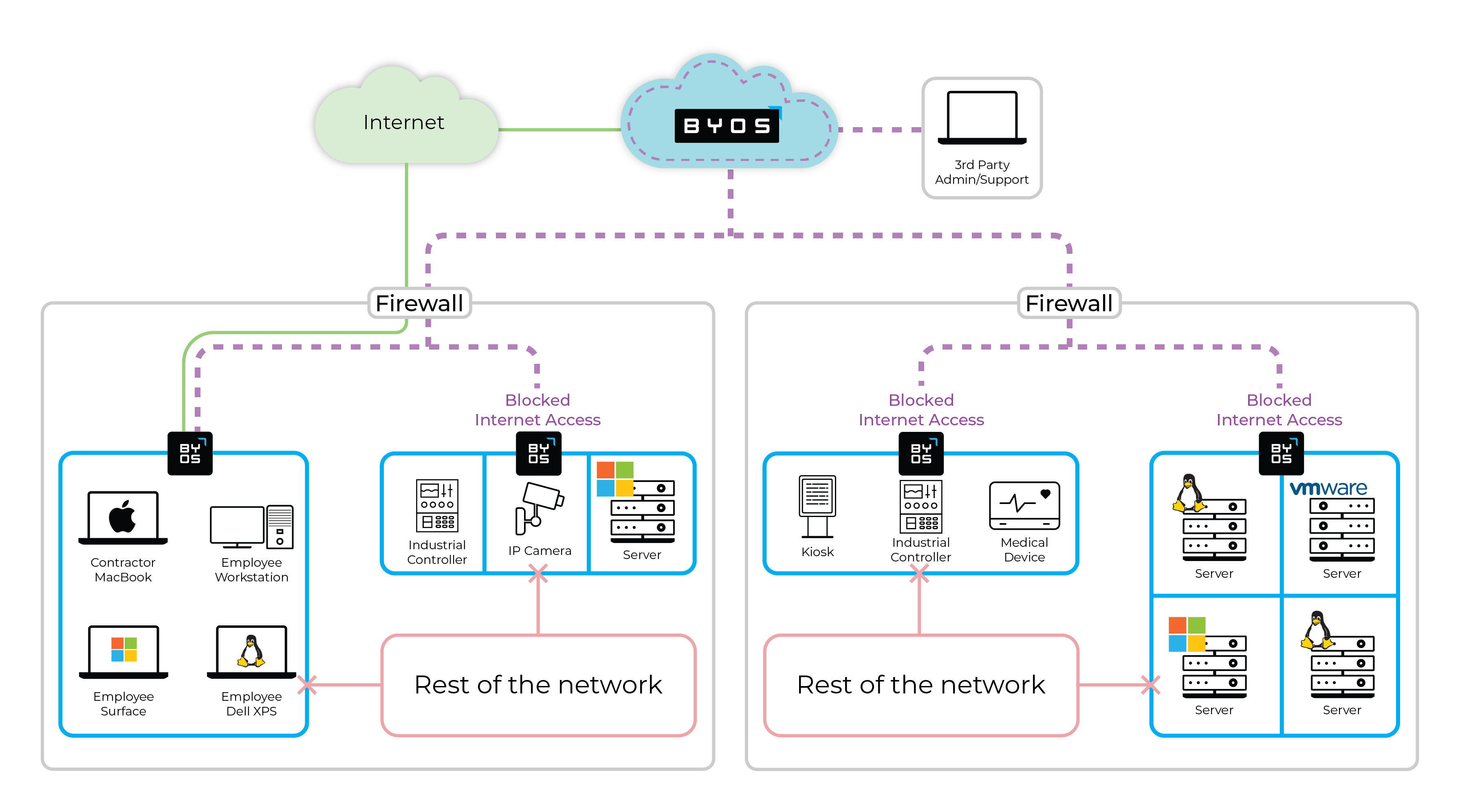
ICS security can be complex, but Byos’s team of experts can help secure your IT and OT environments quickly and efficiently. The Byos Secure Edge uses edge microsegmention to secure ICS devices and implement Zero Trust security principles. Here are a few benefits of the patented Byos Secure Edge:
- Reduced attack surface
- Protect networked devices in order to eliminate exposure to internal threats like lateral movement and ransomware.
- Secure remote access
- Secure and efficient remote maintenance and monitoring of previously air-gapped devices that are now connected to the network.
- Immediate Time-to-Value
- Easy deployment without needing to change existing network configurations and without having to expose internal devices to the internet.
- Protect legacy devices
- Secure and protect IT infrastructure running legacy applications and unsupported OS that are not yet ready to be retired.
- Immediate incident response
- Deploy kill switches to stop all traffic to specific microsegments immediately upon detection of malicious activity, without impacting operations.
- Efficient field service
- Reduce the number of on-site service and maintenance trips technicians need to make to on-site premises, saving on operational costs.
Top Choice in Industrial Cybersecurity: Byos feature in Annual Buyer's Guide
Byos has been featured in the 2024 Industrial Cybersecurity Buyer’s Guide by Industrial Cyber. Read more here to understand why Byos features among the industry-leading solutions to safeguard your critical infrastructure.