🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
Preventing Cyber Attacks is Better than Detect and Respond - The Trick is How to Prevent
Lateral Movement | Data Breach | Malware
March 13th, 2023
The Good, The Bad, and The Ugly
In great movies, the hero must confront an insurmountable turning point - that moment when all is lost, yet a twinge of hope propels an inspiration. What made the first “Star Wars” movie so great was that the change came from inside Luke, and that altered the shift in ‘The Force’.
The cybersecurity industry is coming to that kind of turning point, where we must look at ourselves and question which of our assumptions leads to undesirable outcomes. Doing that will impact why, how, and what we do.
Cisco, Microsoft, Okta, and LastPass were included in the top ten largest breaches of 2022. When market-leading cybersecurity vendors are experiencing such events, we are approaching “Houston, we have a problem” time. You know the numbers:
- HackerOne’s 2022 "Hacker-Powered Security Report" reports over 65,000 new vulnerabilities in 2022, a 21% increase over 2021.
- Kaspersky Lab puts the users impacted by targeted ransomware doubled in the first 10 months of 2022.
- Netscout's 2022 DDoS Threat Intelligence Report put the number of DDoS attacks at just over 6 million attacks globally, with the bandwidth increasing 57% over a six-month period.
- Hiscox Cyber Readiness Report 2022 says a single attack -- Data Breach, malware, ransomware, etc. -- cost US companies a median of $18,000 in 2022, up $10,000 from 2021, with 47% suffering a cyber attack.
There is a Silver Lining in Our Battles with Adversaries
All the above has been bad news. But there are achievements from which we can take comfort. For instance, in Verizon’s March 2022 Data Breach Industry Report[1], the median time to identify a breach is 44 days. The “dwell time” has decreased over the last 10 years, as indicated in the following chart:
| Year | Dwell Time (Days) |
|---|---|
| 2011 | 365+ |
| 2019 | 56 |
| 2020 | 24 |
| 2021 | 21 |
Mandiant’s M-Trends 2022 Report has also observed a trend of decreasing dwell time over the past few years.
Despite the progress with dwell time, adversaries having a three-week or more window to exploit vulnerabilities means that reducing that number to zero will require a different approach. This paper will present the changes that our industry must make, and provide a roadmap that you can use to begin making the changes to your organization’s cybersecurity strategies and execution.
Where to Begin
Previously, we discussed how preventing exploits and key attack techniques, especially early in the attack flow (e.g. kill chain), is far superior to detecting and responding.
There is a fundamental difference in the mindset and approach between good and bad actors in cybersecurity. Our adversaries think in attack vectors and outcomes. Cyber defenders tend to think in lists & structures. We have to face the fact that “Vectors and outcomes will win every time.” When we change our thinking, we will change the outcomes.
A report by McKinsey & Company shows that there has been a radical shift in spending (see chart below). That shift has certainly contributed to reducing dwell time. But it has not reduced the number of successful attacks, exploits, or exfiltrations.
Detect & Respond
We are bombarded with the constant message that detecting faster and automating more solves our problem. It hasn't worked and it won't. And here’s why. Detect&Respond is:
- Retroactive - triggered only after an attack has occurred. Threats are already active before response teams can begin chasing the attack.
- Costly - expensive and takes too long to detect , respond and remediate.
- More Staff - requires human management, maintenance, and tuning due to the wealth of event data. That only increases the demand for experts with relevant skill sets as adversaries produce much greater volumes of attacks with AI.
- More Work - There’s a lot of chatter about AI. Looking into the future, AI is not anticipated to relieve security teams. The reason is that most applications of AI applied to cyber defense employs adaptive machine learning which primarily recognizes patterns that are based exclusively upon the training datasets which it is fed. Even deep-learning-based technology only mimics the data upon which it is trained. So adversaries retain a slight advantage because they will accelerate inputs deliberately designed to fool machine learning classifiers. We can anticipate attacks intended to create false positives, which will consume SOC and incident response teams’ already-stretched time and attention. Their objectives areto make legitimate attacks and evasions “slip past undetected”.
Prevent
Why is preventing cyber-attacks significantly more effective than detecting & responding to them? Because prevention focuses on addressing vulnerabilities before they can be exploited , while detection and response only occur after an attack has occurred. By preventing an attack, the potential damage and disruption to the organization can be avoided entirely. Additionally, preventing an attack saves resources and time that would be spent on detection, response, and recovery. Nor can we forget false positives, and that not all cyber-attacks are detected. Some attacks may go undetected for long periods of time, making prevention even more crucial.
Proactive, preventative technologies and methods are needed to provide a quality defense-in-depth strategy. Included in commonly implemented preventative measure are closing known CVE vulnerabilities and using passwordless MFA authentication (such as HYPR). Both are examples for how process and technology reduce incidents and exposures. That layered defense should work at all 7 Layers of the OSI/ISO Model. At Layer 7, you can find a wealth of SSE/SASE vendors such as CATO, ZScaler and NetsCOPE. Zero Trust application security vendors like Tetrate provide Layer 7 API gateways and protection for IaaS, while cloud platform-specific vendors like DigitSec work “inside’ SaaS-specific applications.. Technologies that address prevention against network and endpoint attack vectors include cloaking devices from being discovered or accessed, microsegmentation, SASE, and ZTNA.
The Obvious Argument Against Prevention
Of course, the naysayers are thinking, “We tried that and failed… firewalls, IPS, NAC, DLP, antivirus, anti-phishing, anti-DDoS… it has all failed.” And yes, they raise excellent points. So let’s address this objection.
Let’s take firewalls for example. Firewalls can be 100% effective. Put them in line, block all ports, and they are virtually impenetrable. (Yes, anything connected to a network can be hacked. But, given the configuration of “all ports blocked”, in the real world, the effort required to circumvent the firewall prevents access to the devices behind the firewall from being accessed.) The vulnerabilities arise when exceptions are made to all ports being blocked:
-
Perimeter protection - Once traffic is allowed to flow through the firewall, the opportunity for adversaries to take a position “inside”, the firewall’s protections are only at the perimeter.
-
Complexity - The number of rules and exceptions tends to grow over time. Firewall configurations are managed by different individuals or teams over time. Gaps and conflicts occur, sometimes referred to as “configuration drift”.
-
Endpoint Protection -Endpoint firewalls, VPNS, and NAC complement perimeter firewalls because they offer local protection. The same holds true for anti-malware, configuration enforcement, and other endpoint protections. This too has flaws:
- When a device is compromised, through an attack sequence that includes other tactics such as privilege escalation, the attacker gains control over the operating system. Once that occurs, endpoint and network protections can be modified, bypassed, or disabled. Removing the security stack from the operating system is the only way to prevent access to device and network protections.
- The variety of tasks performed by endpoints and hosts to which they communicate is vast. Centralized control over the devices helps, but the same thing faced with perimeter protections applies to the other “prevention technologies” – IPS, antimalware, A/V, anti-DDoS, and DLP really aren’t true prevention because they all rely on recognizing known patterns, sequences, or behaviors – so zero-days and new techniques circumvent their “prevention”
Addressing Attack Vectors, Rather than Controls
The most common method of architecting a cybersecurity strategy is to perform a gap analysis against a security controls framework like CIS, NIST, or ISO 27001. Combined with risk and threat modeling, security teams can build a good architecture, technology portfolio and metrics from which to measure their success.
While the combination of those tools provides a good set of controls,a more tactical approach is absolutely the better way to meet the attackers head-on and to be more effective in breaking the kill-chain. By identifying specific techniques and tactics used by adversaries to carry out cyberattacks, we e can build our defenses to prevent specific attack vectors necessary for an adversary to achieve their goals. Put simply, we don’t have to stop every attack technique, just those that are critical in the adversaries’ playbooks. For instance, every initial access or lateral movement event we prevent, the entire subsequent attack flow is subverted.
The MITRE ATT&CK framework is the predominant framework that defines attack flows that adversaries use to progress through to achieve their objectives. Understanding MITRE, you can identify the stages of the kill chain where adversaries are most vulnerable, and architect the optimal defenses to disrupt attacks at those stages.
- Do more with less : An incident/event/false-positive/compromise that never happens requires zero processes/people/time/effort/frustration. Our industry struggles with finding qualified staff and then keeping them. A more proactive approach leads to better culture, better retention, and opportunities for successful projects and professional recognition.
- Defense-in-depth : By prioritizing on preventing an initial foothold, organizations can strengthen their defense-in-depth strategy, which involves implementing multiple layers of security controls to protect against cyber threats. This can include using technologies such as endpoint protection, network segmentation, user education and awareness, vulnerability management, and regular penetration testing and red teaming.
- Continuously improve : It's important to note that preventing an initial foothold is an ongoing process and requires continuous improvement. Organizations should regularly assess their defenses, keep up to date with the latest threats, and adapt their defenses accordingly.
- Early detection and prevention : By focusing on preventing an initial foothold, organizations can detect and prevent attacks early in the cyber kill chain, before attackers are able to establish a persistent presence on the network or exfiltrate sensitive data. This reduces the risk of a successful attack and limits the potential impact of an attack.
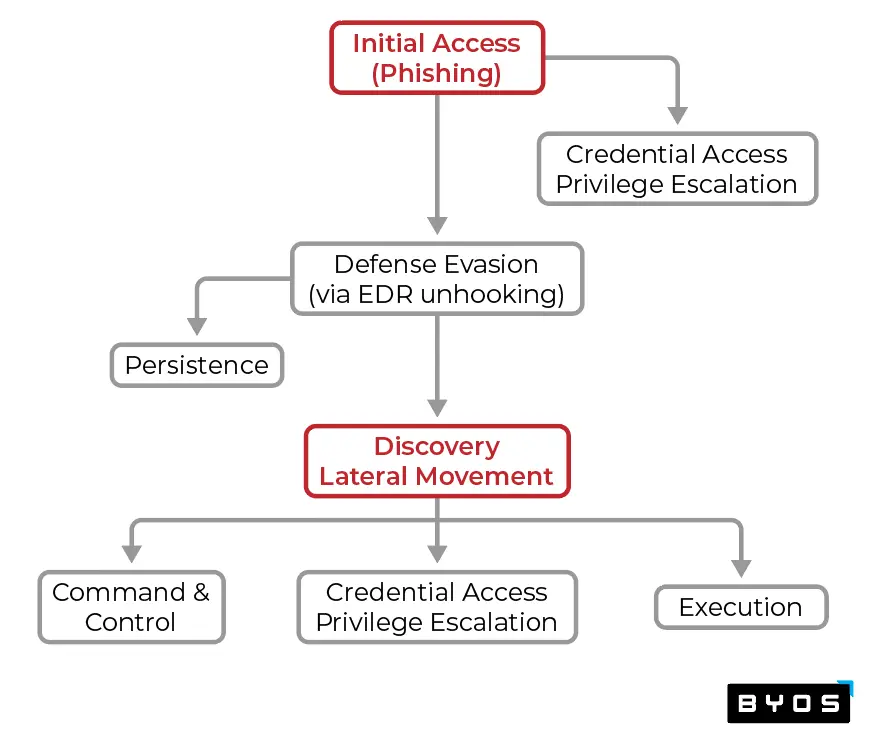
Let’s explore an example where the appropriate controls are in place, but an adversary is able to achieve their objective of gaining initial access at the endpoint. Throughout the rest of the kill chain, the attacker is able to avoid detection and bypass controls, step-by-step, through a process of probing for gaps and other tactics. In the example below:
- ‘Initial Access’ is Critical Step #1.
- Once initial access is achieved, the next Critical Step #2 is ‘Lateral Movement’. Even if other attack techniques are achieved, without the ability to move east/west, and with limited ability to move north (via the implementation of absolute least privilege port/application access controls), the blast radius is contained to one device.
- Even if an adversary were to gain a foothold in a device, subsequent attack techniques – ‘Defense Evasion’ using unhooking EDR or ‘Privilege Escalation’ using credential dumping – have little impact without the ability to access any other devices.
- There are other Critical Steps, such as preventing ‘Exfiltration’ and various sub-techniques. Our purpose of this illustration is to bring forward the methodology of defense strategy using attack vectors vs. controls.
It becomes fairly apparent that by leveraging MITRE ATT&CK, we gain a deeper understanding of the threats facing us. From there, we are able to develop a more targeted and proactive approach from thinking the way our adversaries do – not in lists and priorities - but in attack vectors and outcomes. It levels the playing field. And with that advantage, there is little doubt that our industry will reduce the rewards for the effort that our adversaries must expend. We’ll beat them at their own game.
Of course, compliance frameworks and controls have their place, and they’ll be used in conjunction with attack vector analyses. That leads us to the next step, which is how do we begin the process of truly preventing critical attack vectors through which all attack flows will pass?
So what are the characteristics of true prevention for ‘Initial Access’ and “Lateral Movement’? For endpoints and networks, true prevention holds the following qualities…
- Moves the control function away from the perimeter and closer to the edge. (Ideas for How to Do This)
- Removes the security stack from the operating system. Yet, enforce at the device, but not in the device, nor at the network/perimeter.
- Prevents the successful execution of specific attack tactics used by adversaries.
- Prevents attacks, even those that have never been seen or conceived.
- Minimizes the growth of enforcement and policy complexity. (We use the word “minimize” here, because as anyone reading will appreciate, there’s no way to prevent “just plain stupid”. Of course, we’re attending to that challenge as well.)
Conclusion
Here’s a list of recommendations for how to return your organization to a more effective, more proactive, yet simpler protection posture.
- Move back toward a focus of preventing attacks, as opposed to detecting them.
- Retain detection as a key part of your defense-in depth strategy. It’s not going away, you’re simply shifting your focus toward prevention.
- Prevent early stage attack vectors, like ‘Initial Access’ and ‘Lateral Movement’. Interrupting adversaries at those stages keeps them from being able to do anything else in the kill chain.
Renew your confidence that we can not just improve our defense posture, but that we can make our adversaries’ successful outcomes so rare that they will conclude that attacking our networks is not a good use of their time. Demotivated adversaries are ones that we can defeat, not just keep their intrusions at bay.
Platform
Use Cases (Industry)
Use Cases (Application)
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)