Malware Protection: Everything IT Pros Need to Know

Managing the security demands of an enterprise network in the post-COVID landscape is a massive undertaking. Malware attacks are increasing in severity and scope, as 61% of businesses reported experiencing some form of ransomware attack in 2021. Understanding the fundamentals of malware protection will give you the tools you need to keep malicious actors out of your network and mitigate damage if and when your network is compromised.
Read on to learn how to prevent attacks before they happen, make essential upgrades to your tech stack, and what to do if you find yourself the victim of a cybersecurity incident.
Jump to a section…
Ransomware is common — and costly
Prevent malware attacks before they happen
Understand the seven stages of the kill chain
Upgrade your tech stack to prevent malware attacks
Compromise protection strategies
Post-compromise protection strategies
Deploy malware mitigation techniques when a cyber attack occurs
Provide clear communication and transparency during a cybersecurity incident
Ransomware is common — and costly
Ransomware is one of the most devastating forms of malware used across the world, and the costs associated with preventing attacks — or dealing with the fallout — have increased along with it. A report from the U.S. Treasury shows that ransomware payments hit $600m for the first half of 2021, totaling more in payments than the entirety of 2020.
Ransomware isn’t just hitting large enterprises, either. Targets for ransomware are diverse. Since 2021, ransomware has struck graphics card manufacturer Nvidia, a major parts supplier for Toyota, the Virginia state legislature, US fuel supplier Colonial Pipelines, and more.
It may be tempting to give in to the ransom demands, but law enforcement generally suggests not paying malicious actors as there’s no guarantee that they will return your data upon payment. Further, paying the ransom enables further ransomware attacks as actors continue to see an opportunity for huge payouts.
Ransomware isn’t the only threat you need to keep an eye out for. Read The 10 Types of Malware Every Security Pro Needs to Know to learn more.
Take care of the basics
Some of the most effective malware protection strategies are the boring basics of cyber:
- Implement and update antivirus, anti-malware, and anti-ransomware software to protect against initial infection from common attacks.
- Maintain password best practices — longer than eight characters, use a combination of letters, numbers, and symbols, keep passwords secure and avoid storing them in obvious locations — and employ multi-factor authentication whenever possible.
- Keep software, operating systems, browsers, and other potential vectors for attack up-to-date to ensure use of the latest security features.
- Keep users in your organization informed about policies and best practices, and engender healthy skepticism of links, files, and emails sent by external or unfamiliar sources.
Keep these tips in mind as you develop your security team’s protocol for day-to-day operations.
For more details on malware prevention and recent examples of ransomware attacks, read our guide How to Prevent Malware Attacks.
Understand the seven stages of the kill chain
Effective malware protection means knowing how malicious actors surveil and initiate attacks against vulnerable systems. Here are the seven stages of a typical cyber kill chain:
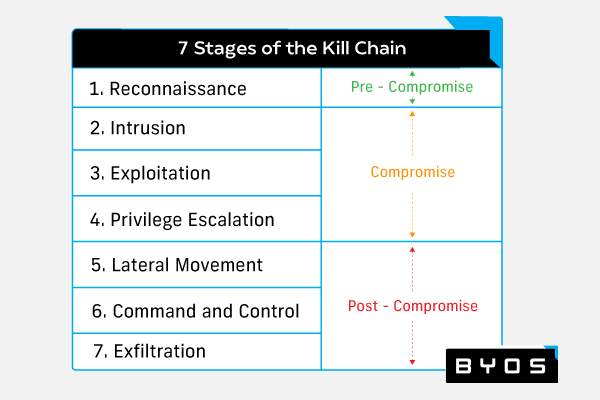
- Reconnaissance: The pre-compromise phase of the kill chain begins with the initial surveillance of the target system and selection of an attack strategy.
- Intrusion: The compromise phase of the kill chain begins when the malicious actor gains initial access to the target system.
- Exploitation: The malicious actor gains greater access to the target system
- Privilege escalation: The malicious actor maximizes access by gaining admin privileges
- Lateral movement: The post-compromise phase of the kill chain begins as the malicious actor moves from system to system to gain further access while avoiding detection
- Command and control: The malicious actor gains full network access.
- Exfiltration: Theft, destruction, or encryption of data begins.
Once you know how malicious actors attack and gain control of your systems, you can implement solutions to keep them out or mitigate damage.
Read Enterprise Malware Protection: How to Build the Ideal Security Stack to learn effective compromise solutions and discover vendors who can help.
Upgrade your tech stack to prevent malware attacks
Now that you understand the kill chain, you can implement solutions to ward off attacks during either the compromise or post-compromise phases. Each phase of the kill chain requires its own specialized set of tools and techniques.
Compromise protection strategies
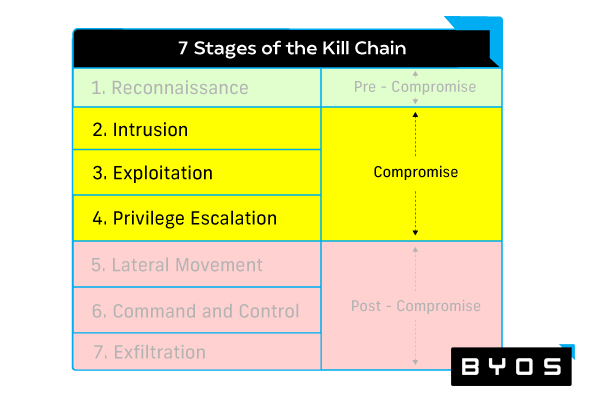
Implementing the following malware protection solutions will help prevent the initial compromise from taking root or spreading:
- Vulnerability management provides effective analysis of devices on your network, assessing potential attack vectors, then shoring up vulnerabilities.
- Implementing cloud-based security solutions like secure access service edge (SASE).
- Identity management prevents unauthorized users from achieving deeper access to critical systems.
- Endpoint security, detection, and response solutions monitor for suspicious endpoint activity and respond to endpoint attacks.
Post-compromise protection strategies
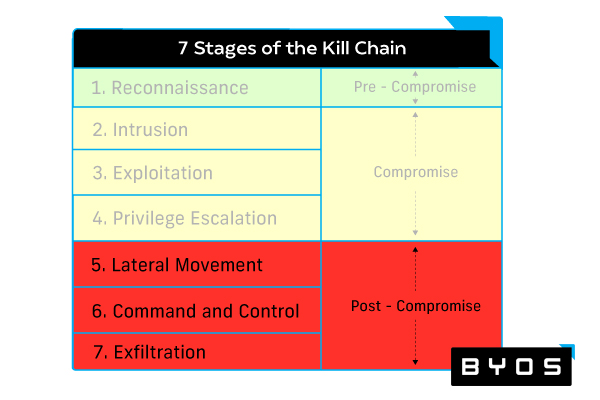
Once a compromise is in progress, the following solutions will help mitigate damage and prevent further malware spread:
- Cyber monitoring and analytics tools like security information and event management (SIEM) and user and entity behavior analytics (UEBA) analyze historical data to pinpoint out-of-the-ordinary network activity.
- Microsegmentation shrinks the attack surface by reducing the network into smaller microsegments that are more easily protected and controlled.
- Web access protection through secure web gateways (SWG) and cloud access security brokers (CASB) allow application of security policies to provide threat protection for web- and cloud-based access points.
Get more detail on these protection strategies and learn how to strengthen the security of your network by reading Malware Protection: How to Build the Ideal Tech Stack in 2022.
Deploy malware mitigation techniques when a cyber attack occurs
With the sheer volume of attacks occurring and new breach techniques being developed all the time, you should assume a successful intrusion is a question of when, not if. Knowing the most effective mitigation techniques against a cyber attack can provide malware protection for your network when reaction time is critical. Here are the three most effective strategies for stopping a cyberattack before it compromises your entire network.
- Kill switches: Defensive kill switches can be deployed to deactivate internet connections to vital systems, preventing attacker propagation and lateral movement. Malicious actors can also use kill switches to hide their actions, however, so using intrusion detection systems (IDS) and malware detection tools can help keep your systems secure.
- Prevent lateral movement: Malicious actors secure their hold on your system through lateral movement through your network’s systems. To stop lateral movement before an actor gains full control, you need to be able to isolate your most vulnerable systems, restrict communication through your network, and deploy context-based access controls to ensure only authorized users have access to critical systems or information.
- Edge microsegmentation: Microsegmentation is one of the most effective forms of malware protection during a security breach, essentially breaking your network down into smaller, isolated networks. By decreasing the potential attack surface, you’re able to improve the total security of your entire system.
Learn more about how to use kill switches effectively, prevent lateral movement, and implement edge microsegmentation in our guide, 3 Malware Mitigation Techniques For Keeping Cyber Attacks Contained in 2022.
Provide clear communication and transparency during a cybersecurity incident
Your security team should have a game plan in place in the event of a successful malware attack. Part of this plan should include steps for contacting the appropriate authorities, as well as working with your public relations team to begin crafting messages for delivery to key stakeholders (like public officials and shareholders), as well as the general public.
Provide open and transparent communication about the extent of the data breach, what has been affected, and steps being taken to protect public information and prevent further attacks as quickly as possible. Doing so can mean the difference between salvaging your brand’s reputation (along with future revenue) and having to deal with expensive lawsuits on top of the damage already done.
For an example of effective incident management, look at how Norsk Hydro responded after being compromised by a LockerGoga ransomware attack. The Norwegian energy company held a press conference shortly after the damage from the breach was properly assessed and mitigated, and documented recovery efforts via videos and social media posts. Even though the company lost revenue from the attack, their stock value increased due to their clear and trustworthy approach.
For more tips on how to mitigate impact from cyber attacks, manage your response to the public, and update your processes to ensure security in the future, read Enterprise Malware Removal: 4 Steps to Follow Once You’ve Been Compromised.
An ounce of prevention
Getting informed is only half the battle. Implementing solutions across your tech stack and staying on top of the latest prevention measures will ensure that you’re prepared should malicious actors strike, and having plans in place during a crisis will help you manage the worst effects of a cyber attack.
If you’re searching for ways to improve network security — especially on remote endpoints where you don’t have as much control — Byos can help - we have developed a technology that makes networks invisible to attackers trying to move laterally. This approach isolates devices from the network, protecting them from exploit and DDoS attacks, enumeration, and eavesdropping using edge microsegmentation. It is for distributed workforce security, protecting legacy devices in IoT/OT networks, and embedding a dedicated network security stack in any endpoint from the product line. Ready to learn more? Get in touch with us here.
