
Although denial-of-service attacks have been around since the nineties, they have never been more relevant. There were 9.5 million denial-of-service attacks in 2019, and that number has been projected to reach 15.4 million by 2023. This rapid growth makes it essential for every security professional to be proficient in denial-of-service attack prevention.
After reviewing the definition and exploring the history of this cyberattack, this article outlines the current best practices for neutralizing this threat.
Jump to a section…
What is a denial-of-service attack?
How can denial-of-service attacks be prevented?
The importance of denial-of-service attack prevention
What is a denial-of-service attack?
A denial-of-service (DoS) attack is a cyberattack that attempts to keep the authorized users of a device or network from using that device or network. DoS attacks use two primary strategies to accomplish that goal. The first — and most popular — strategy is flooding: overwhelming a device or network with traffic. The second strategy is crashing services: exploiting weaknesses in the device or network’s security in order to cause it to shut down.
Unlike other cyber attacks, DoS attacks do not typically result in stolen, destroyed, or corrupted data. Instead, DoS attacks cause damage by making an organization incapable of running essential systems and services, which can be costly to recover. Banks, media companies, governments, and other large organizations are all popular targets due to the high level of disruption that their inability to function causes.
One of the most challenging DoS attacks to prevent and recover from is a distributed denial-of-service attack (DDoS). In a DDoS attack, numerous malicious external systems work in tandem to execute the attack, which makes the source of the attack both harder to find and harder to stop.
Denial of service attacks are among the most common cybersecurity threats, and a 2021 Cloudflare report indicates their frequency is trending upward at a record-breaking pace. For more information on other cybersecurity threats, watch the webinar Zero Trust: The Most Overused, Misused & Abused Cybersecurity Phrase Today.
Different DoS attacks have different methods of execution. The most common types are:
- UDP flood exploits targets with User Datagram Protocol (UDP) packets, overwhelming it with traffic and causing it to crash.
- TCP SYN floods exploit the three-way handshake process used by TCP to establish a connection between two devices. The attacker sends SYN packets to the target, which responds with a SYN-ACK packet. The attacker does not respond with a third ACK packet, causing the server to hold the connection open and eventually run out of resources.
- HTTP flood sends HTTP requests to web servers, overwhelming it and causing it to crash or become unresponsive.
- Ping flood attacks assets with ICMP (Internet Control Message Protocol) Echo Request packets, consuming all the bandwidth and making it impossible for legitimate traffic to get through.
DoS attacks can have a significant impact on businesses and individuals, both in terms of financial losses and damage to brand reputation. Some of the consequences of a successful DoS attack may include:
- A DoS attack can make a website or service unavailable to legitimate users, causing lost revenue and damage to customer relationships.
- Sites may remain online during a DoS attack. They may become slow or unresponsive, making it difficult or impossible for users to interact.
- The aftermath of a DoS attack can be expensive. Extensive damage can be done to the target or legal fees may be incurred.
- A successful DoS attack can damage a company's reputation, especially if it results in extended downtime or data breaches.
- IT staff, focused on DoS mitigation, can be a diversion from other attacks, and take time away from projects and tasks.
Detecting a DoS attacks early is crucial in minimizing its impact. Indicators that a DoS attack may be underway include:
- Abnormally high traffic
- Slow or unresponsive servers
- High server utilization
- Unusual traffic patterns
- Unusual traffic sources
How can denial-of-service attacks be prevented?
Preventing a DoS attack can be challenging, but there are several effective techniques:
-
Network segmentation - Segmenting networks into smaller, more manageable pieces, can limit the impact of a DoS attack. This can be done by creating VLANs, and firewalls can limit the spread of an attack. The optimal solution is zero trust microsegmentation. Adding device-level and device-cloaking firewalling, external to the operating system remains the most reliable form of DoS protection.
-
Load balancing - Distributing traffic across multiple servers, a DoS attack can be prevented from overwhelming a single server or resource. Load balancing can be achieved using hardware or software solutions.
-
IP blocking - Blocking traffic from known or suspected malicious sources can prevent DoS traffic from reaching its target.
-
Rate limiting - Limiting the rate of traffic to reach a server or resource can prevent a DoS attack from overwhelming it.
-
Content Delivery Networks (CDNs) - Distributing website content across multiple locations makes it more difficult for an attack to bring down an entire site.
Byos has a unique and reliable way to protect devices from DoS. To learn how Byos can protect your network from DoS and so much more, reference this chart and read this article.
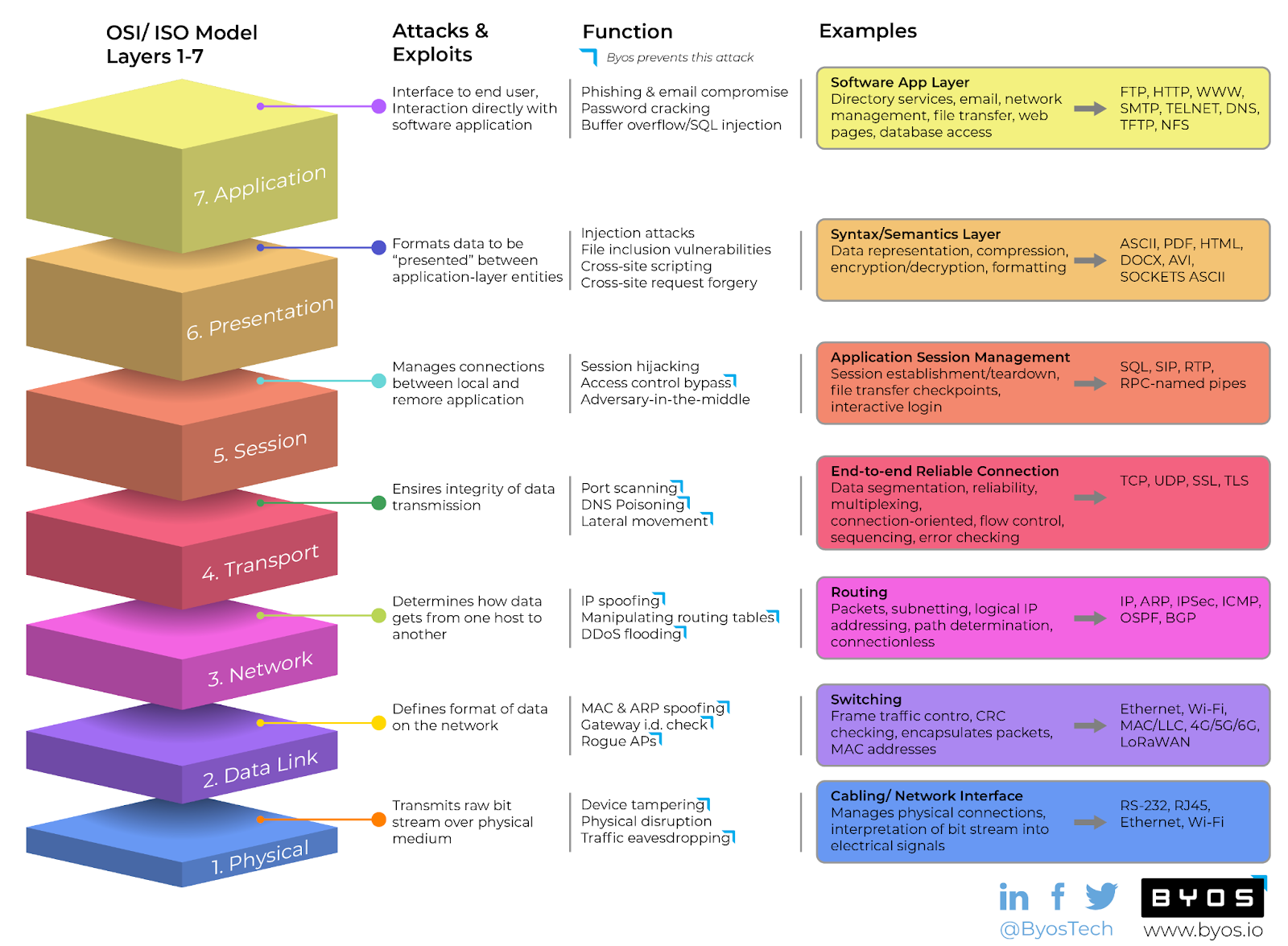
DoS mitigation: what to do during an attack
If a DoS attack is underway, there are several steps that can be taken to mitigate its impact:
-
Traffic filtering can eliminate known or suspected malicious sources.
-
Blackhole routing involves redirecting all traffic to a null route, effectively dropping all incoming traffic. This can be an effective way to mitigate a DoS attack, but it can also impact legitimate traffic.
-
Scrubbing services identify and filter out malicious traffic, allowing legitimate traffic to reach its destination.
DoS protection: choosing the right solution
Approaches to DoS protection on the market today:
- Cloud-based services
- On-premise hardware
- Hybrid (combines cloud and on-premise)
- Asset cloaking (each asset is undiscoverable and inaccessible, with asset-specific firewalls running outside the operating system, blocking malicious packets from reaching or leaving the device)
These tools offer a range of protection and mitigation capabilities, from basic IP blocking to advanced traffic filtering and scrubbing.
|
Vendor name |
Product Name |
Method |
Open Source |
|
Cloudflare |
DoS Protection |
Cloud-based |
No |
|
F5 Networks |
Silverline |
Cloud-based |
No |
|
Imperva |
Incapsula |
Cloud-based |
No |
|
Byos |
Secure Edge |
AssetCloaking |
No |
|
Fortinet |
FortiDoS |
On-premise |
No |
|
A10 Networks |
Thunder TPS |
On-premise |
No |
|
Snort |
Snort |
On-premise |
Yes |
|
NGINX |
NGINX Plus |
Hybrid |
Yes |
|
Radware |
DefensePro |
Hybrid |
No |
|
Arbor Networks |
Peakflow |
Hybrid |
No |
- Network size and complexity
- Type of traffic protected
- Budget available
The importance of denial-of-service attack prevention
As is often the case, preparation and planning are critical to denial-of-service attacks prevention. Assessing your network for vulnerabilities is time-consuming, as is drafting a DoS response plan and ensuring your security staff can distinguish the early warning signs of an attack in progress. Each pillar of prevention is a challenge in its own right, but the product is peace of mind.
One of the most effective ways of protecting your network against DoS attacks is to reduce the attack surface via microsegmentation. At Byos, we use endpoint microsegmentation to shrink network exposure to its most defensible component and optimize its resilience to attack. If you are interested in learning more, then get started here.
FAQs
How common are DoS attacks?
Some estimates suggest that there are thousands of DoS attacks per day worldwide.
Who is responsible for protecting against DoS attacks?
The responsibility to protect against DoS attacks is with the organization. Some internet service providers (ISPs) offer DoS protection as a service.
How long can a DoS attack last?
DoS attacks can last for hours, days, or even weeks, depending on the complexity and severity of the attack.
Can a DoS attack be stopped?
While challenging to stop a DoS attack entirely, there are techniques that can be effective in mitigating the impact of an attack.
Is DoS protection expensive?
DoS protection costs vary widely, depending on your network’s size and complexity and the type of protection needed. However, the cost of not having protection can be much higher.
If you're looking for a reliable DoS protection solution, consider our product, which offers cloud-based protection services with advanced traffic filtering and scrubbing capabilities. With flexible pricing and scalable solutions, we can help protect your business from the potential damage of a DoS attack. Contact us today to learn more.

