How to Prevent and Detect Lateral Movement In Your Network
A cyber attack that spreads through a network using lateral movement is a threat to all organizations. Attackers typically use lateral movement to disguise themselves as legitimate users and their activities as normal traffic, making the technique very difficult to detect. With that said, there are steps that security teams can take to strengthen organizations’ security postures and more effectively prevent and detect lateral movement tactics on the network.
In this article, we’ll briefly explore the definition of lateral movement before exploring how to detect lateral movement in your network and, ideally, prevent lateral movement before it happens.
Jump to a section…
Strategies for preventing and detecting lateral movement in your network
Restrict network communications
Develop internal network intelligence
Implement edge microsegmentation
What is lateral movement?
Lateral movement is a technique that attackers use to move freely between compromised networks, devices, and applications, spreading through a system in search of valuable data. After gaining access, attackers use lateral movement to explore the network, map out its structure, and search for resources like applications and devices. Lateral movement also allows attackers to maintain access and escalate privileges, simultaneously moving deeper into the network and avoiding detection by disguising themselves within the flow of permitted east-west traffic in order to avoid detection.
Network security professionals have historically spent more of their security budgets on protecting the perimeter from external threats, and are therefore better equipped to monitor the north-south traffic that crosses the firewall into an organization’s network. But the threat of tactics like lateral movement makes visibility into east-west traffic an equally important security strategy.
Strategies for preventing and detecting lateral movement in your network
Lateral movement is especially difficult to detect because it is difficult to differentiate between legitimate and malicious network traffic. Understanding the concept of lateral movement and how it works is the first step toward detecting it when it happens, and ideally, prevent it from occurring at all.
These are some of the best ways for organizations to prevent and detect lateral movement.
Audit your security hygiene
One of the simplest ways to protect against lateral movement is to ensure you cover the fundamentals of network security. Security posture weaknesses arise when organizations have poor or inconsistently applied security hygiene; in order to develop and maintain a robust security posture, every element of the organization — from users to the applications they run and networks to individual endpoints — must adopt security best practices.
Update software regularly
Every service, application, operating system, and device should be running the most up-to-date software available.
Isolate unpatched systems
Protect vulnerable legacy technologies that can’t be patched by isolating them from the rest of the network.
Filter open ports
Ensure there are no unnecessary open ports to help protect against common exploits and malware.
Issue least privilege access
Grant access only to what’s required for users to complete their work or applications to serve their functions.
Maintain unique passwords
Make sure to use strong, secure passwords backed by SSO, MFA, and restricted login protocols.
Restrict network communications
Eliminate nonessential communications from application to application, device to device, or network to network.
Back up sensitive data
Implementing a strong strategy to back up critical data, systems, and applications helps ensure continuity in the event of a security incident.
Create shared policies
Standardize the implementation of these best practices with policies that mandate scheduled software updates, data backups, password changes, etc.
In the same way people visit the doctor for regular check-ups, it’s a recommended practice to perform regularly scheduled health checks on your security posture. Frequent audits — even when there’s no indication of specific issues or threats — can help uncover potential vulnerabilities before they become dangerous and identify opportunities to strengthen, improve, or update basic security protocols. Lateral movement occurs after an attacker gains access to the network, so protecting against that initial breach is a strong first step toward preventing it.
Develop internal network intelligence
Developing deep internal knowledge of regular network traffic helps create a benchmark against which to measure rogue usage and scan for potential threats. That way, only the activity that falls outside legitimate users’ typical patterns of login and usage behavior will trigger alerts. The alert fatigue that security professionals experience when inundated by harmless security alarms can make it more difficult to notice and react to legitimate threats. Focusing on signs of credential theft or abuse in this way helps reduce the number of security alerts that crop up, instead of sending up a red flag every time someone logs in.
Visibility and control go hand in hand with developing that internal network intelligence. Network administrators with complete visibility into north-south and east-west traffic are better equipped to proactively secure critical devices, detect and identify threats, and isolate compromised devices when breaches do take place. This detailed understanding of network traffic also allows admins to design the identity-based policies (enabled by effective network microsegmentation) that govern the flow of traffic in and out of applications, devices, and endpoints.
Assess your endpoint security
As the modern workforce adapts to the new normal of distributed teams and remote work, it’s even more important for organizations to secure each individual endpoint connecting to the corporate network, regardless of its physical location. The importance of visibility applies to laptops and mobile devices connecting remotely as much as it does to in-office desktops and devices plugged directly into the network.
Logging network activity is a common security practice, since collecting a record of network traffic is a valuable tool for both threat monitoring and post-compromise investigations. Strong endpoint security also feeds back into the goal of developing internal network intelligence, since the age of remote work requires an expanded understanding of what can be considered “internal”. Increased visibility into every endpoint — including laptops and mobile devices, for example — will lead to a more detailed picture of what constitutes normal activity and user behaviors. The more detailed your internal network intelligence is, the easier it is to identify threats and protect devices remotely.
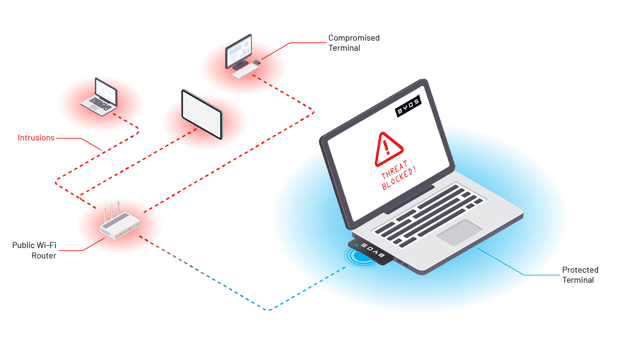
Implement edge microsegmentation
Implementing edge microsegmentation is arguably the strongest way to prevent and detect lateral movement. High profile worms like WannaCry and NotPetya, for example, used lateral movement to transform what could have been containable breaches into full-scale attacks. In short, microsegmentation divides networks into precisely defined zones that can be protected independently in order to strengthen the overall network’s security posture. Securing each endpoint as a microsegment of one reduces the available attack surface, decreasing risk while increasing security teams’ ability to prevent, detect, and respond to attacks on devices anywhere in the world.
By granting security administrators control at a distance, edge microsegmentation makes it easier not just to prevent and detect lateral movement, but also to contain and remediate attacks if there is a breach. While isolating a network from potential risk is certainly a priority, edge microsegmentation also offers a wide range of other benefits, like streamlining the work of network administrators and IT technicians, enabling remote troubleshooting for distributed devices, and unifying security strategy across an entire fleet.
We created the patented Byos Secure Edge in order to introduce microsegmentation at the edge, protecting all of an organization’s device fleet at once no matter where your team is located. Users can connect safely and confidently to any network from any device because Byos turns each endpoint into an isolated microsegment, reducing the threat of attacks and making it easier to prevent and detect lateral movement. Ready to learn more? Contact us to learn more today

