How Byos Prevents Lateral Movement In Corporate Networks
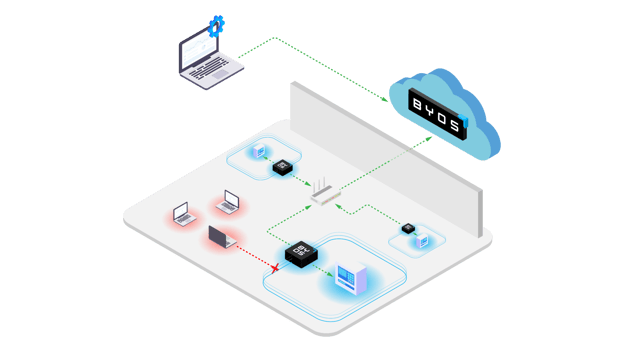
Lateral movement tactics have been in the spotlight lately, thanks to their use in high-profile attacks like WannaCry and NotPetya. At Byos, we believe that edge microsegmentation is the strongest method for preventing and detecting lateral movement. By using granular microsegments to isolate endpoints, security administrators are able to stop attackers from escalating privileges and spreading throughout a network.
Breaches are seemingly uncontainable given currently-existing defensive techniques. Why? Lateral movement. That’s why Byos gives security teams the ability to prevent, detect, and respond to lateral movement on any kind of device, anywhere in the world. Here’s how we do it.
Jump to a section…
Adding host-independent security
Providing remote visibility and control
Protecting legacy and IIoT devices
In summary, edge microsegmentation
Reducing the attack surface
Perimeter-based security strategies no longer suffice as organizations see their users and devices spread across public and private networks all around the world. This device sprawl increases the risk of network-based threats like exploits, enumeration, and Wi-Fi and DDoS attacks. Byos protects against those attack vectors by reducing the available attack surface using edge microsegmentation.
The Byos μGateway provides hardware-enforced isolation from the network with lower layer security processing at the edge. This allows for complete control of all ingress and egress traffic, enabling security administrators to stop malicious traffic from entering the device in the first place. Your immune system makes for a good analogy; like endpoint security software, the immune system works from within to protect against infections that may enter the body, while preventative measures such as masks work to stop contaminants from entering the body in the first place, keeping them out at the edge, just like hardware-enforced microsegmentation.
Adding host-independent security
Isolating a network from potential risks is one of the main benefits of edge microsegmentation. By introducing a layer of security independent of the host, the Byos μGateway provides protection that security software simply cannot. Attacks that use lateral movement tactics often start by scanning for and corrupting or disabling any existing antivirus and endpoint detection response software solutions. That’s why it’s critical to apply a layer of security independent from the operating system. Edge microsegmentation provides protection outside the host in order to prevent attackers from jumping between compromised endpoints, escalating privileges, and spreading across the network.
Providing remote visibility and control
The granularity of edge microsegmentation gives security teams increased visibility and control, enabling them to access and manage all protected endpoints inside of the microsegments. With the ability to more easily monitor all traffic passing in and out of an endpoint, security administrators can more efficiently prevent and detect lateral movement, and contain and remediate attacks if a breach does occur.
Byos grants security administrators that level of visibility and control at a distance, which is particularly important for organizations with distributed devices and remote workforces. The world of work is changing quickly, and as business travel and work from home policies continue to evolve, securing and managing remote workers is a top priority for CISOs.
In addition to supporting virtual workforces, the Byos μGateway provides a plug-and-play security solution for organizations with BYO device policies. BYO devices connect to an organization’s applications and networks all the time, but if they are compromised or infected they become a vehicle for lateral movement. The Byos solution is a simple and practical way to prevent that.
Protecting legacy and IIoT devices
Continuing that simplicity, Byos also makes it possible for administrators to unify a single security strategy across endpoints typically not able to be protected by agent-based security solutions. For example, Industrial Internet of Things (IIoT) devices, industrial controllers, point-of-sale terminals, and medical devices often run unsupported and unpatched operating systems. Because legacy, operational, and unmanaged devices can’t be protected by incompatible security software, they require an agentless form of protection.
These networked devices are particularly vulnerable to attack, and they are popular points of entry for attackers with the intention of moving laterally to spread through the system. Byos provides the agentless protection these kinds of devices require with powerful visibility and control, allowing administrators to prevent, mitigate, and remediate attacks that use lateral movement techniques.
In summary, edge microsegmentation
Edge microsegmentation enables security teams to securely and effectively protect against lateral movement, one of the major tactical threats on today’s cyber landscape. That’s why the Byos Secure Gateway isolates endpoints in granular microsegments, preventing the risks associated with public and private networks, legacy, IIoT, and BYO devices, and remote and distributed workforces. Ready to learn more?
