Distributed Workforce Security
How to make security a priority for remote endpoints
As enterprises embrace the remote workplace, security teams face a new host of challenges. Many employees are now connecting to unsecured Wi-Fi networks for the majority of their working hours. As a result, businesses are seeing a rise in data breaches — in 2021, ransomware attacks increased by 6%, phishing grew by 11%, and companies faced 15x more misrepresentation cases.
It’s time for enterprises to put a renewed focus on distributed workforce security; it requires a comprehensive security strategy that accounts for the threat vector of public and home networks but is scalable for employees around the world. Thankfully, that’s what Byos can offer. Click the button below to request a demo, or read on to learn more.
Distributed Workforce Security Categories
What is distributed workforce security?
Distributed workforce security broadly refers to the strategies and technologies that protect endpoints from viruses, malware, data breaches, and attacks. It refers to device security, local area network security, and cloud security for workers accessing applications remotely.
%20Deploy-3b-2.png)
Remote Work Security Challenges
What are the obstacles to securing a distributed workforce?
Securing the remote workforce is challenging given its distributed nature. Any long-term solution must be able to overcome the following challenges:
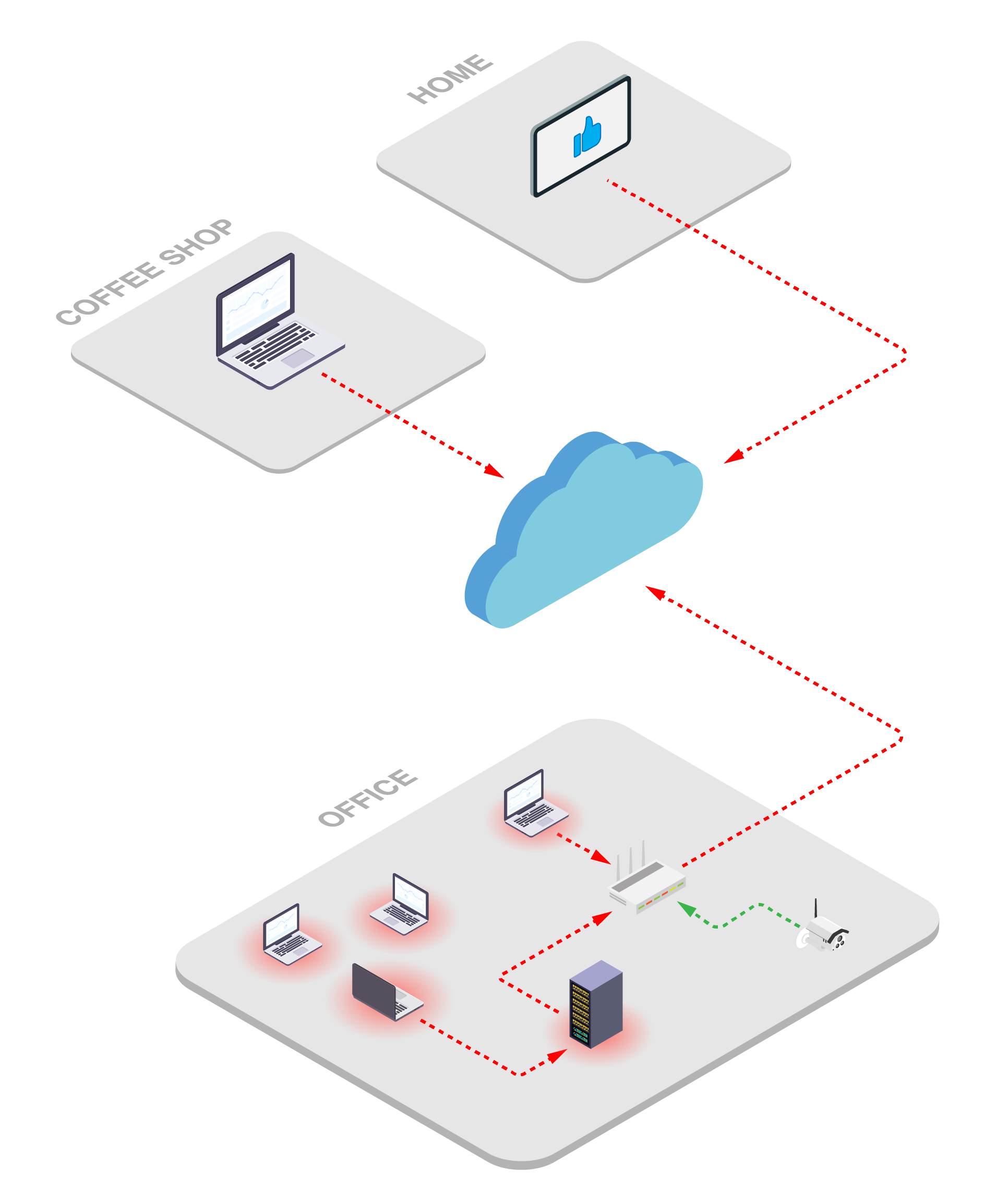
- Insecure Network Connections: Devices are connecting to unmanaged and uncontrolled networks , and the threats that live and spread throughout these networks are infecting exposed endpoints.
- Lack of visibility: Admins have a limited view of the traffic and sessions their employee's devices have established when on remote networks.
- Unsecured endpoints: Recent studies suggest that remote workers collectively use hundreds of thousands of unsecured devices to interact with their workplace and other cloud services.
- Distributed threats: Many workforces are international, driving connections from networks anywhere in the world, making it harder to identify potential security breaches.
Remote Work Security Threats
What threats do employees face in a distributed workforce?
In the wake of COVID-19 and the growing distributed workforce, 67% of security attacks now target remote employees. In a traditional perimeter networks, administrators could secure individual endpoints and prevent ransomware attacks at each workstation. Unfortunately, these benefits are limited in remote workplaces, which increases the dangers of:
- Wireless hacking: Attacks on wireless routers or linked access points to gain unauthorized access to private networks.
- Eavesdropping: An attempt to electronically intercept information from conversations and web activity without the user noticing.
- Traffic manipulation: A strategy of injecting malicious data packets into communication streams to redirect traffic or exploit IP fragmentation.
- Phishing: A form of email fraud where criminals pretend to be reputable companies to trick recipients into sharing personal information.
- Ransomware: A malware variant that threatens to publish personal data or blocks access to critical files until a ransom is paid.
.png)
Distributed Workforce Security Solutions
What are the common solutions?
Most businesses use a combination of endpoint and cloud security.
Endpoint Detection and Response (EDR)
EDR technologies protect endpoints using a combination of next-gen antivirus software, threat detection tools, and data loss protection. They protect devices from the attacks that are caused by user-error: phishing, downloading malware, etc. These platforms are managed by IT security.
Unfortunately, while EDR can protect endpoint devices, it cannot prevent attacks from reaching them in the first place (ie. lateral movement). Since EDR technologies are installed on the endpoint, they’re governed by the OS, and thus susceptible to bypass vulnerabilities and other evasion tactics.
Secure Access Service Edge (SASE) and Zero Trust Network Access (ZTNA)
Many businesses leverage network or cloud-level security to identify suspicious activity throughout their networks. This technique relies on zero-trust principles, which assume endpoints cannot be trusted. In response, these security platforms make granular security assessments by confirming user identities, verifying device posture, and monitoring app activity.
SASE and ZTNA solutions allow for security at Layer 7, performing URL filtering, traffic inspection, and data encryption. Since SASE and ZTNA solutions exist in the cloud, they cannot protect the device from networking attacks, such as fingerprinting, exploiting, and eavesdropping.
Distributed Workforce Security Solutions
How does HANA complement to EDR and cloud-based security?
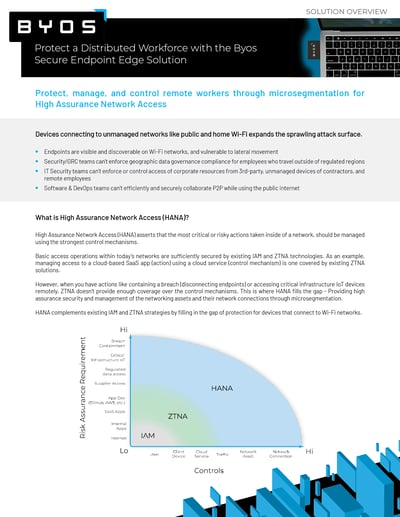
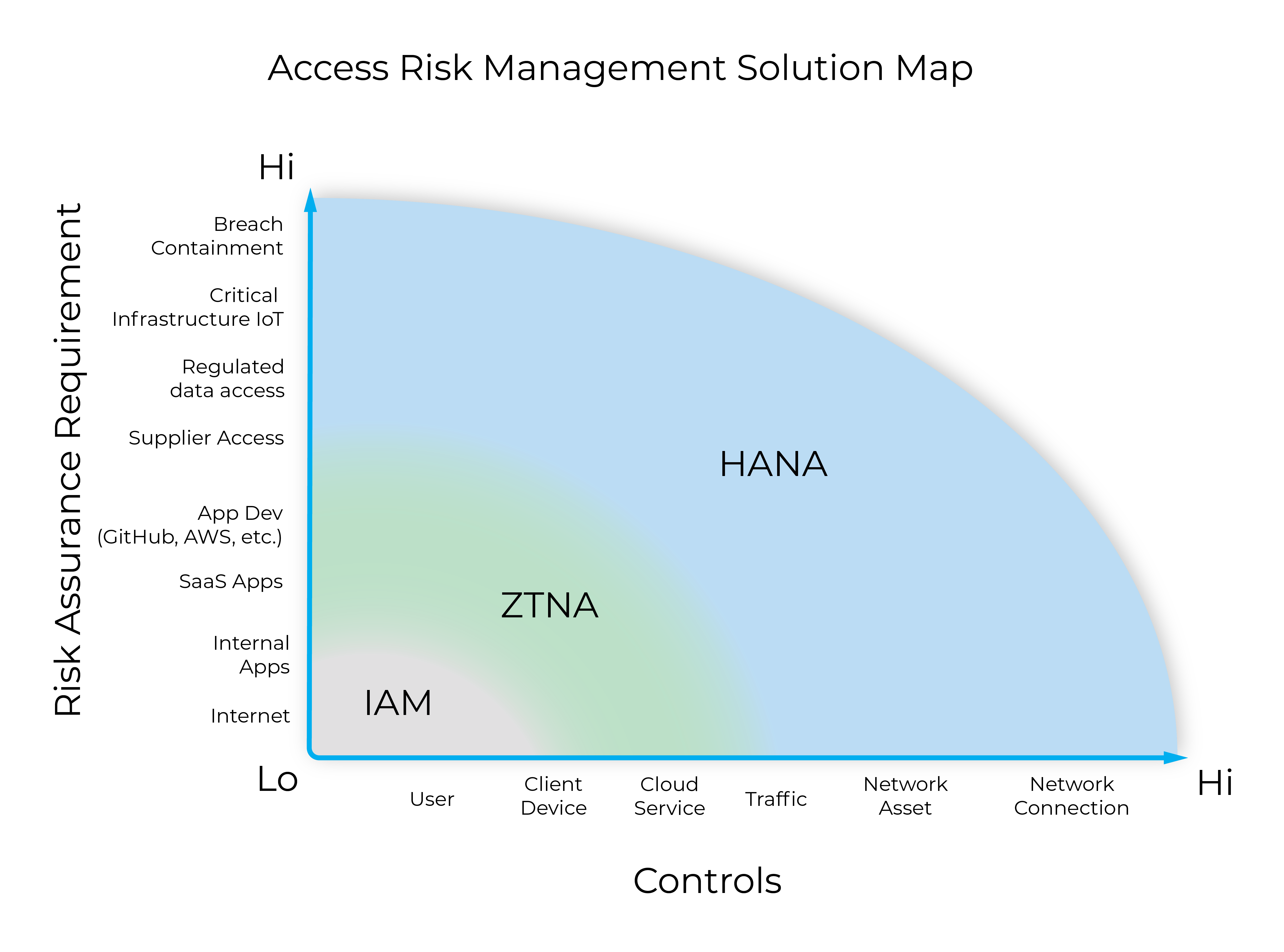
For all the benefits of EDR and SASE/ZTNA security, there is still a gap in protection when devices connect to untrusted Wi-Fi networks. As workplace networks continue to expand and diversify, a new approach for securing remote employees is necessary — High Assurance Network Access (HANA).
HANA asserts that critical actions within a network should be managed with the strongest control mechanisms. Each mechanism is measured against both the degree of control administrators need to secure the system and the level of risk for actions performed within network infrastructure.
HANA provides high assurance security and management of networking assets and their network connections through microsegmentation, complementing IAM and ZTNA solutions.
HANA and Edge Microsegmentation
How can network admins and CISOs secure their distributed workforce today?
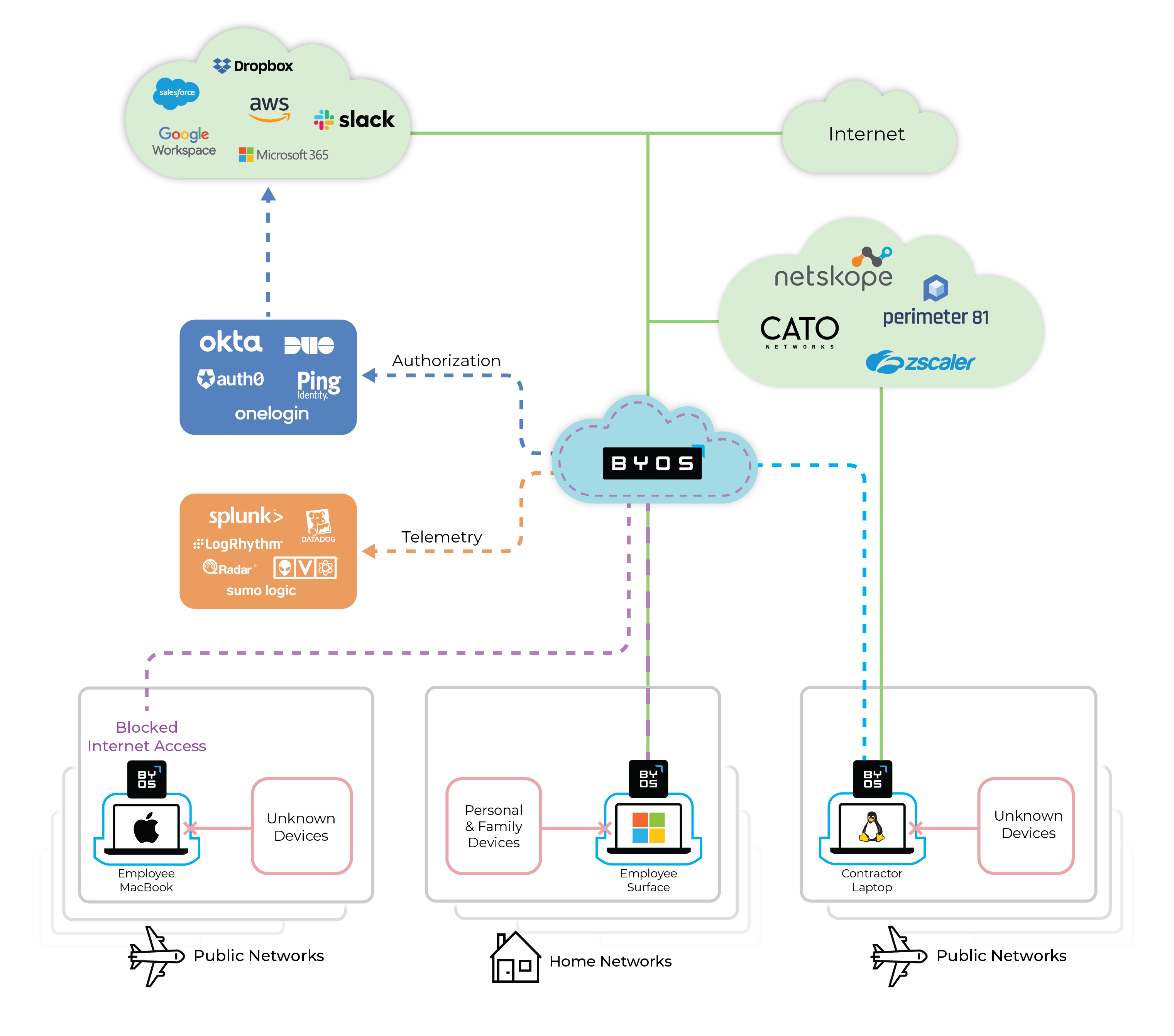
Edge microsegmentation is the first example of HANA-based security — protecting against network attacks while allowing administrators to manage and control remote endpoints. The Byos Secure Endpoint Edge uses edge microsegmention to secure all endpoints within a public network to meet Zero Trust security objectives more effectively. Here are a few benefits of Byos Secure Endpoint Edge:
- Secure connectivity using edge segmentation
- Each Secure Endpoint Edge isolates the connected device onto its own micro-segment to protect endpoints from compromised networks and networks from compromised endpoints.
- Reduced attack surface
- Byos eliminates exposure of networked devices to threats like wireless hacking and ransomware.
- Remote IT management
- All security policy administration is handled centrally through the Byos Management Console, which allows IT teams to deploy and manage µGateways at scale
- Maintaining Data Compliance
- Ensuring all traffic and data originating from endpoints on unmanaged networks flows through controlled exit nodes.

How Byos Can Help
Edge Microsegmentation for a fully remote workforce.
Byos is dedicated to helping organizations protect their network and remote workers against all threats, vulnerabilities, and malicious attacks. Want to know more? Read the FAQ or click the button below to request a demo.