🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
Securing Machine Data Capture in OT Environments
Industrial IoT | Operational Technology
March 20th, 2024

In this post, we explore how to secure Machine Data Capture within Operational Technology (OT) environments. Highlighting its significance and relevance, we look at how Machine Data Capture serves as a cornerstone for informed decision-making and operational efficiency in various industries. However, alongside its benefits, we also consider the security threats and risks that accompany the capture and analysis of machine data. From Ransomware incidents of unauthorized access, the landscape of Machine Data Capture security remains fraught with challenges. Moreover, we explore additional hurdles, ranging from interoperability issues to the complexities of legacy systems integration. Nevertheless, amidst these challenges, we present best practices tailored for safeguarding Machine Data Capture in OT environments.
Introduction
In today's rapidly evolving technological landscape, having consistent, near real-time machine data has become indispensable for optimizing operations and enhancing efficiency across various industries. Within Operational Technology (OT) environments, which encompass industrial processes, manufacturing, and critical infrastructure; Operations and Analytics teams rely heavily on machine data capture to monitor, control, and manage their production systems. However, the push for more and better data within an operation, means that more emphasis is put on the security of the network, because there are more opportunities for compromise. With the rising dependence on machine data across different industries, ensuring integrity, confidentiality and availability of the data captured is becoming an increasing challenge for these teams.
Machine Data Capture, MDC for short, refers to the process of collecting and recording data generated by various machines and devices in an automated and structured manner. This data can come from a wide range of sources, such as industrial equipment, sensors, electronic devices, vehicles, and more. The captured data includes information about the operation, performance, status, and behavior of these machines. This data is typically in a digital format and can encompass various types such as logs, sensor readings, timestamps, event records, and more.
Importance and Relevance of Machine Data Capture in OT
One of the key reasons machine data capture forms the backbone of modern OT environments is that MDC provides valuable insights that drive informed decision-making. By collecting and analyzing data from sensors, devices, and machinery, organizations can gain valuable information about performance, efficiency, and potential areas for improvement. Predictive maintenance, a key outcome of machine data analysis, enables businesses to identify maintenance needs before equipment failure occurs, reducing downtime and maintenance costs. Moreover, process optimization fuelled by machine data insights allows for streamlined workflows and enhanced productivity.
Beyond operational insights and predictive maintenance, machine data capture also enables:
- Process Optimization: Machine data capture enables businesses to optimize processes by identifying bottlenecks, inefficiencies, and areas for improvement. Analyzing this data can help organizations streamline their operations and increase productivity.
- Quality Control: In industries like manufacturing, machine data can be used to ensure product quality. By monitoring various parameters during production, companies can identify deviations from desired quality standards and take corrective actions.
- Regulatory Compliance: Many industries have regulations and standards that require data collection and reporting. Machine data capture helps organizations meet these compliance requirements by providing accurate and comprehensive records of machine activities and processes.
- IoT and Industry 4.0: The Internet of Things (IoT) and Industry 4.0 concepts rely heavily on machine data capture. These technologies involve connecting devices and machines to gather data and make data-driven decisions. This process can be used for any machine with an embedded controller or PLC (programmable logic controller). Signals are collected from the controls by data collection units. These signals are then processed and standardized in the data acquisition unit. Machine data forms the foundation for these transformative technologies.
- Data-Driven Decision-Making: Machine data capture supports data-driven decision-making. Organizations can make informed choices based on real-time and historical machine data, leading to better strategic planning and operational outcomes.
- Enhanced Customer Experience: Machine data can also play a role in enhancing customer experience. For example, in the transportation industry, companies can use machine data to provide real-time updates on vehicle locations, estimated arrival times, and more.
- Innovation and Research: Researchers and engineers can use machine data to innovate new products and technologies. Analyzing large datasets can reveal patterns, correlations, and opportunities that might not be apparent through traditional methods.
- Security and Monitoring: Machine data capture is also crucial for security purposes. Monitoring network and system logs can help detect and prevent security breaches by identifying unusual or unauthorized activities.
Overall, machine data capture brings in clear benefits with data-driven decision-making, operational efficiency, heightened security, and adaptability to emerging technological trends. It’s evident OT systems need to be empowered, in a secure manner, with MDC rather than allowing OT equipment to be air-gapped, not integrated with data acquisition units or limited in connectivity in order to fully realize these benefits.
Machine Data Capture Security Threats and Risks
While the benefits of machine data capture in OT are obvious, risk of down time and exposure of networks to cyber threats is a growing concern. Ransomware and unauthorized access are the two most significant risks to the integrity and operation of critical systems. Beyond this, there are other threats that are common to OT environments that present risks to the network such as insider threats and supply chain vulnerabilities that can lead to data loss or persistent footholds. Third-parties may also need access to the data captured for system maintenance and other functions, presenting additional challenges.
Many organizations resort to full IT and OT network segregation, and in some cases, even full air gapping to ensure the integrity of the network. These choices have direct trade offs towards how effective machine data collection and analysis is, increasing operational costs associated.
Legacy Device Challenges in Securing Machine Data Capture
Legacy assets are the machinery, control systems, and sensors deployed prior to the Industry 4.0 era, typically single purpose in nature and were built to only be networked on a LAN. Securing these types of assets pose certain challenges such as:
- Many times they cannot be protected by modern software solutions because they don’t have enough compute or storage to have applications installed on them.
- The wide range of different types of devices, protocols, and systems from dozens of vendors, means that protection is difficult to deploy and often disparate in nature.
- Vulnerabilities are difficult to patch because of legacy asset brittle operating systems. Some vulnerabilities are also unpatchable because they exist at the hardware level.
The increased focus on capture of machine data has not surprisingly aligned with the rise of cloud-enabled software and applications across businesses, but these multi-side, multi-network operations operations can often also lead to complexity in securing these networks, because these segregated networks now need internet-access to operate at maximum feature functionality .
Best Practices for Securing Machine Data Capture in OT Environments
When Operations and Security teams are evaluating solutions for improving machine data capture in OT environments, security is one of their main concerns. “How can we effectively secure the network and devices so that we have consistent, reliable data, without adding risk?”
Teams have previously approached the problem using a number of point solutions - Firewalls, VPNs, IP/DS, and vulnerability management systems, but this has led to more complexity for less operational benefit. Platforms built for the exact use case will always perform better.
Some of the best practices for securing machine data capture include:
- Protecting against ransomware and lateral movement using Microsegmentation - Microsegmenting production assets so that they are isolated from threats on the local network ensures that the blast radius of any attack is contained to the smallest possible attack surface. This does not impact an asset’s operation.
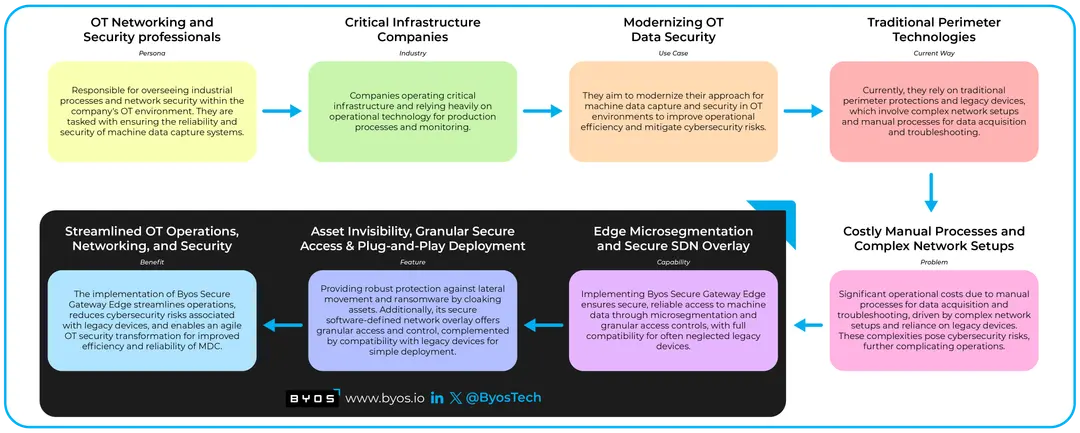
- Legacy Device Compatibility - The Byos Secure Gateway Edge does this by being a plug-and-play, device-agnostic IoT Gateway that connects directly to PLCs and Controllers, or any legacy device that speaks TCP/IP. All it needs is an ethernet connection to the Assets and a Wi-Fi or Ethernet connection to the network
- Secure, reliable, and granular access to systems using an overlay network - Long gone are the days of broad access into a network. By implementing a Secure Software Defined Network (SDN) Overlay with OSI Layer 2, 3, and 4 protections and access controls, assets are not accessible by East-West traffic on the local network, but can be accessed via controlled North-South traffic. Data capture and real-time monitoring of network devices, traffic, and user activities can continue without adding unnecessary exposure to the network.
- Control over 3rd Party access into specific resources - With Byos, Admins can specify exactly which port and service an Asset has access to, without exposing the rest of the Asset itself, or other devices within the underlying network
- Simple, scalable deployment - Deployment of Byos goes as fast as you want. Scale asset by asset, site by site, and requires minimal changes to the underlying network architecture.
Example Use Case
A Fortune 100 manufacturer with over 50 plant operations worldwide recently modernized their approach for their OT systems and data capture using these practices, as part of a much broader plant floor transformation project. A longstanding decision was in place that prohibited connecting OT assets to their network, driven by the high cost challenges, complexities, and cybersecurity risks. Their existing strategy was complicated by legacy devices, a combination of hardware and client-based VPNs, and traditional perimeter protections that necessitated time-consuming manual processes for data acquisition and troubleshooting. Recognizing the need for a more agile and cost-effective approach, their CISO and Director of Manufacturing & Analytics worked together with Byos to formulate a strategy that turned OT security from being an operational inhibitor into a business enabler.
Read more about the Use Case here: Securing Industrial Control Networks in Manufacturing
Conclusion
In the age of digital transformation, securing machine data capture in OT environments is a necessity. The symbiotic relationship between data-driven insights and operational efficiency underscores the need to safeguard machine data from ever-evolving cyber threats. By adopting a proactive and comprehensive approach to network security, with microsegmentation and a secure overlay network, organizations can protect critical systems, maintain the integrity of operations, and ensure a resilient and secure OT landscape in an increasingly interconnected world.
From a business perspective, this approach helps in optimizing operations, reducing costs, enhancing safety and compliance, and supporting data-driven decision-making while reducing the risk of security incidents. Ultimately, organizations would be best served with a two-pronged solution that delivers both greater visibility as well as defense-in-depth protection that detects, blocks, and reduces the risk of threats to machine captured data.
FAQ
What is Machine Data Capture (MDC) and why is it important in OT environments?
Machine Data Capture refers to the collection and recording of data generated by various machines and devices in automated processes. It is crucial in OT environments as it provides valuable insights for informed decision-making, operational efficiency, and predictive maintenance.
What are the primary benefits of Machine Data Capture (MDC) in OT environments?
The primary benefits include process optimization, quality control, regulatory compliance, support for IoT and Industry 4.0, data-driven decision-making, enhanced customer experience, innovation and research, and security and monitoring.
What are some common security threats and risks associated with Machine Data Capture (MDC) in OT environments?
Security threats include ransomware, unauthorized access, insider threats, supply chain vulnerabilities, and challenges related to legacy devices.
How can organizations address the security challenges posed by legacy devices in Machine Data Capture (MDC)?
Organizations can address legacy device challenges by implementing solutions like microsegmentation, secure overlay networks, and ensuring compatibility with legacy devices using plug-and-play IoT gateways.
What are some best practices for securing Machine Data Capture (MDC) in OT environments?
Best practices include protecting against ransomware and lateral movement through microsegmentation, ensuring legacy device compatibility, implementing secure overlay networks, controlling third-party access, and deploying solutions that are simple and scalable.
What role does network security play in securing Machine Data Capture (MDC) in OT environments?
Network security is paramount in securing MDC as it helps in protecting critical systems, maintaining operational integrity, ensuring data confidentiality, and mitigating cyber threats.
How can organizations ensure reliable access to machine data while maintaining a secure network environment?
Organizations can ensure reliable access to machine data by implementing secure overlay networks with granular access controls, monitoring network devices and user activities in real-time, and controlling third-party access to specific resources.
What are the implications of full IT and OT network segregation on Machine Data Capture (MDC) efficiency?
Full IT and OT network segregation can increase operational costs associated with machine data collection and analysis, limiting the effectiveness of MDC and hindering operational efficiency.
How can organizations balance the need for connectivity with the security of Machine Data Capture (MDC) systems?
Organizations can balance connectivity and security by adopting solutions that offer secure access controls, implementing proactive security measures like microsegmentation, and ensuring compatibility with legacy devices.
What are the business benefits of adopting a proactive approach to securing Machine Data Capture (MDC) in OT environments?
Business benefits include optimizing operations, reducing costs, enhancing safety and compliance, supporting data-driven decision-making, and reducing the risk of security incidents, ultimately enabling a more resilient and secure OT landscape.
Platform
Use Cases (Industry)
Use Cases (Application)
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)