🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
Rethinking OT Network Administration: How Byos Transforms Legacy Practices
Operational Technology
May 8th, 2025
In the fast-paced world of cybersecurity and network management, traditional networking approaches are becoming a burden. OT Administration teams often deal with manual IP assignments, outdated security protocols, and fragmented management tools. These inefficiencies lead to increased security risks, operational headaches, and wasted resources. Byos takes a fundamentally different approach—one that simplifies, secures, and streamlines network administration.
Out with the Old, In with the New
Networking Admins are used to dealing with the traditional methods , and issues, of managing networks: manual configurations, complex security policies, and reliance on multiple, often incompatible management tools. This is inefficient, error-prone, and increasingly leaves networks vulnerable to threats. Byos’ platform is designed to replace these outdated processes with a modern, automated, and secure solution.
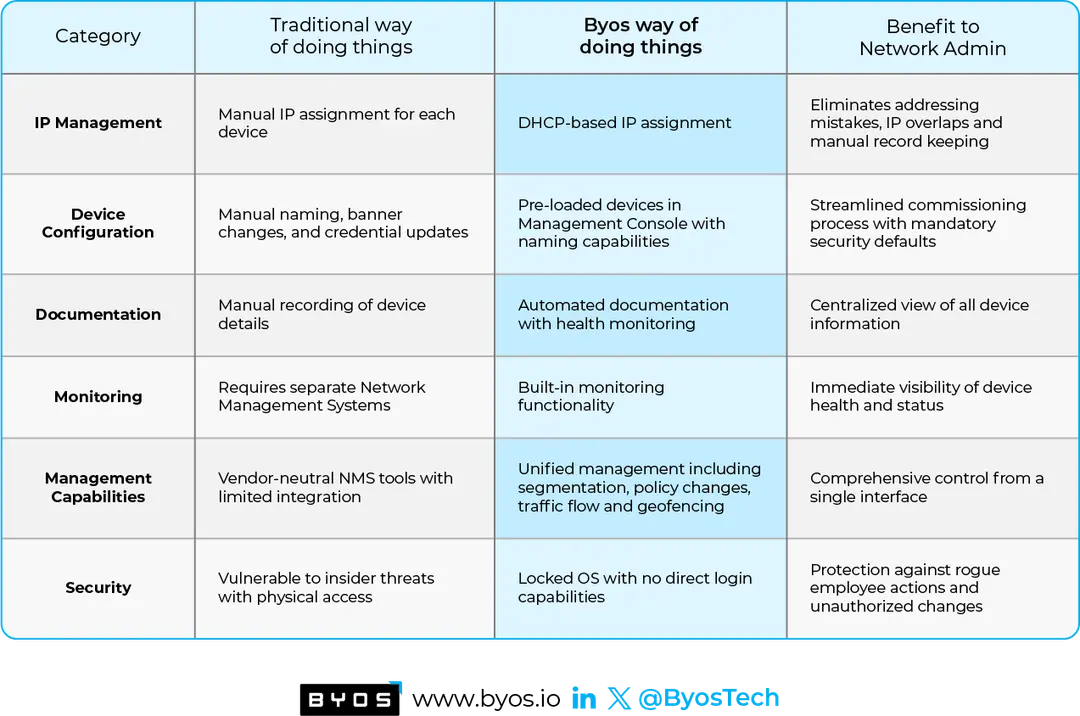
The comparison table below details how Byos streamlines network administration compared to traditional networking practices:
The Byos Advantage
By replacing manual processes with automated solutions, Byos not only enhances security but also improves efficiency across the entire network. Here’s how Byos transforms networking:
- Automation Reduces Errors: Manual IP assignments and device configurations often lead to mistakes that cause downtime and security risks. Byos eliminates these risks with automated DHCP-based IP assignment and pre-loaded device configurations.
- Built-In Security: Legacy systems rely on traditional access controls that can be bypassed. Byos enforces a Zero Trust model with a locked-down OS and network cloaking to prevent unauthorized access.
- Unified Management: Instead of juggling multiple tools, administrators can manage segmentation, policy changes, and traffic flow from a single, centralized console.
- Enhanced Visibility: Byos enables secure connectivity for previously air-gapped devices - without allowing any internet exposure. Byos also facilitates more secure data capture for remote and dispersed assets across multiple sites in real time - without introducing additional security risks. This allows organizations to get greater oversight and control over their critical infrastructure without exposing it to traditional network vulnerabilities.
- Scalability and Adaptability: The Byos platform is designed to scale easily, making it an ideal solution for organizations of all sizes. Byos platform was also designed to be truly network agnostic, securing any device that speaks TCP/IP and working seamlessly across IT, OT, and IIoT environments. Whether protecting a handful of devices or an extensive enterprise network, Byos ensures consistent security and management.
- Reduced Administrative Overhead: Traditional OT networking requires significant manual intervention, consuming valuable resources. Byos automates documentation and many tasks, freeing up administrators to focus on higher-value strategic initiatives.
A Network Approach without the Headaches - Byos has you covered
Traditional networking approaches no longer meet the demands of modern security and operational efficiency. Byos provides a streamlined, secure, and easy-to-manage solution for OT administrators looking to simplify their networks without sacrificing security.
Organizations that have adopted Byos’ hardware-based microsegmentation platform are already seeing the benefits of its modernized networking approach. From industrial operations to government and defense agencies, Byos is helping organizations simplify security and ensure reliable network connectivity. OT teams report reduced deployment times, fewer misconfigurations, and improved compliance with security policies.
Byos’ approach also plays a critical role in securing legacy and mission-critical systems, which often lack built-in security features. By deploying Byos, organizations can extend the lifespan of their existing infrastructure while ensuring robust protection against cyber threats.
It’s time to rethink networking. Are you considering moving beyond legacy network tools? Book a demo with us to learn how Byos can redefine your network security.
Platform
Use Cases (Industry)
Use Cases (Application)
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)