🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
Remote Support for Your OT Network Without the Risk
August 29th, 2023
The rise of remote support of robots, industrial controls, sensors and other plant floor systems is transforming OT. Most organizations find that securing access inhibits the process of providing remote support services. The issues revolve around a couple of important considerations:
- How does an enterprise ensure that devices outside of its control do not introduce a threat into the network?
- If some sort of compromise were to get past the protective layer around the internal systems, no matter how unlikely, how can the impact be minimized and be isolated to the device that is compromised so that it is unable to spread to any other device on the network?
This article explores how to let vendors remotely access OT without jeopardizing security.
Jump to a section...
Understanding Third-Party Remote Support
Challenges Opening Remote Access for Support
The Cybersecurity Team’s Concerns about VPN Access
Why Remote Access Poses a Security Risk
Benefits of Controlling Remote Access with Device Isolation
Creating Robust and Highly Secure Processes for Remote Support
Introduction
To provide remote support access, organizations are typically required to open firewall ports and provide an encrypted path of communication in and out of the protected network, most commonly using a VPN. But cybercriminals have developed ways to bypass or evade the traditional technologies that most organizations rely upon, even today.
Understanding Third-Party Remote Support
Network and endpoint security for OT differs from traditional IT environments due to the variety of devices, a multitude of legacy systems, and unique remote access requirements. Limiting access in the most restrictive way is vital in maintaining the security and integrity of OT networks.
The challenge lies in finding a way to enable remote access without adding unnecessary exposure to the network that could lead to compromises in its integrity. The growing demands for cloud access, data collection, and digital transformation are changing the requirements of remote access and remote support in industrial networks.
Challenges Opening Remote Access for Support
Allowing remote support in OT networks poses several challenges that aren't commonly found in IT security. The sensitive nature of OT networks requires strict access controls and limitations. Ensuring the authenticity and integrity of remote support vendors is crucial in preventing unauthorized access.
Cybersecurity teams are rightfully concerned about using VPNs and firewall segmentation. Opening the firewall for remote access exposes the OT network to a range of risks, while devices connected via VPNs become "trusted devices," making them ideal launchpads for network attacks. Notably, trusted third-party access played a critical role in major cybersecurity failures like the Target breach and the SolarWinds incident.
The Cybersecurity Team’s Concerns about VPN Access
Both traditional PC-based VPNs and newer hardware VPNs have limitations when it comes to OT networks. Once a VPN connection is established within perimeter protections, it has overly broad access to the network, negating the intentions of the firewall protections. Maintaining granular policies becomes complex, leading to misalignments with the original design over time.
Mature cybersecurity teams understand these risks and sometimes resort to air-gapping devices entirely to prevent compromised remote devices from spreading contamination to the protected OT network. However, these requirements burden the operations team and can limit the opportunities for data collection and real-time monitoring.
Why remote access poses such a security risk
Once there is a way into the network, very few protections are often in place to prevent attackers from moving laterally between plant floor assets. If these devices are connected to the network, they have open ports; and if they have open ports, they can be enumerated and exploited. It is crucial to find a solution that provides the necessary access for remote support while removing this ‘exposure by default’ posture of critical assets.
Remote Access of Isolated Assets
To address the challenges and limitations of traditional approaches, organizations are isolating each asset onto their own protected microsegment. Unlike VPNs, where only inbound traffic is filtered, inspected, and monitored, isolating each device in a communication pair provides total control over the entire connection.
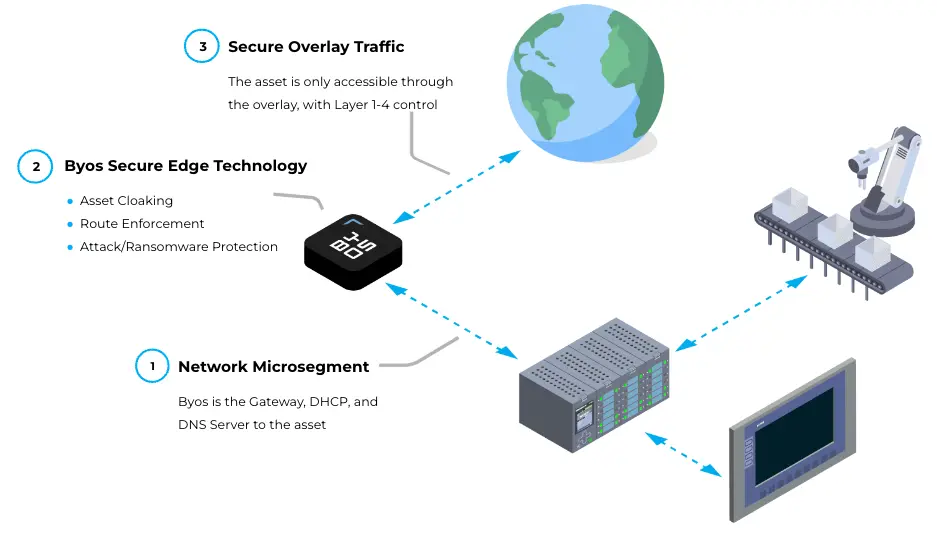
This concept works by sitting between each protected asset and the network interface port to which it is attached, establishing a secure overlay network that is invisible to all except those assets who’ve been isolated.This approach enforces absolute least privilege access policies. The result is that each asset can only perform authorized tasks and it limits their access to the specific device or devices they are authorized to communicate with. If an attacker is on the local network, they won’t be able to find the asset, nor will they be able to communicate laterally within the overlay. The isolation method used prevents the paired devices from knowing that the other device is even attached to a network.
Completely isolating remote access is unique to how OT cybersecurity is enhanced. Unlike traditional approaches, its enforcement does not sit in the cloud, at the perimeter, or on the endpoint. Instead, it is positioned between the protected asset and where it interfaces to the network. For ethernet, that is between the asset and the switch. For wireless devices, it is between the asset and the Wi-Fi APs.
Compartmentalizing access is key to reducing the risk of resource misuse and ensuring sensitive resources can be isolated and protected from unauthorized access. Through the Byos Secure Lobby Overlay, administrators can establish networking “Zones” which are OSI Layer 2 enforced networking boundaries. Layer 3 and 4 access control routes to specific resources (ports and service combinations) can then be applied to specific microsegments, completely isolating assets and restricting access to only the necessary devices, ports/tasks, minimizing the potential for unauthorized or malicious activity. An admin is only authorized to access a resource within the Byos network after all three controls are completed to ensure granular secure communications across devices connecting from unknown networks.
Furthermore, a key factor in keeping the OT network completely protected requires an administrative interface that intuitively leads to the creation of consistent rules and policies. This simplifies the process of managing and maintaining the security measures as designed, reducing the likelihood of misconfigurations or policy deviations. It has the additional benefit that day-to-day administration can be performed by plant personnel without having to involve a highly-trained network and security specialist.
By leveraging these mechanisms, Byos’ isolated remote access enables organizations to establish a secure and controlled environment for remote support, allowing properly authorized individuals to perform their tasks while minimizing the risk of potential security breaches.
Benefits of Controlling Remote Access with Edge Microsegmentation
Numerous benefits emerge to address the challenges of opening remote access to OT devices while ensuring security and minimizing risk. Here are the key advantages:
- Eliminating open firewall ports reduces the attack surface. This minimizes the risk of unauthorized access and potential security breaches.
- Preventing access to the rest of the network from remote devices. Remote devices can communicate with a machine on the inside, but lateral movement isn’t allowed.
- Remote support vendors can only perform authorized tasks on the specific devices where they are authorized. This tight control maintains the network’s integrity.
Simplifying management and maintenance by eliminating the need for complex configuration changes on multiple security systems, saving time and effort for OT and security teams.## Creating Robust and Highly Secure Processes for Remote Support
Remote access requires planning and adherence to best practices to ensure its effectiveness and security. This involves tight coordination between IT Security and OT. Here are recommended practices:
- Joint initial network setup and configuration with both ITSec and Plant floor OT operators to establish the baseline networking policies and architecture.
- Delegate day-to-day administration tasks to plant floor personnel who are intimately familiar with OT. When the administrative procedures are developed within the framework of a well-planned access, visibility, and security policy, this delegation removes a large burden from the IT and security teams and speeds up operational processes.
- Establishing a review and approval process: Implement a well-defined review and approval process for ad hoc changes to remote access policies. This process should include a designated expiration point to ensure that temporary access permissions are revoked promptly.
- Regular audits and policy reviews identify changes to the best-practice design so that you maintain the consistency and effectiveness of remote support controls and adherence to security standards.
- Escalation procedures, clearly defined, aid operators in resolving operational and security issues, providing appropriate channels for reporting and resolving problems, and minimizing disruptions in operations.
Conclusion
Secure remote support is a major component to transforming OT, allowing assets to be diagnosed and troubleshooted faster, while reducing travel and personnel costs. It requires communication and availability that minimizes risk and streamlines procedures. Best practices are the design of robust processes, such as moving day-to-day administration to the front line, establishing workable escalation procedures, and conducting regular audits to make sure the procedures remain consistent with the way the OT works, further strengthening the security and effectiveness of remote support. With secure and controlled remote access, organizations can leverage the benefits of remote support while ensuring the integrity and confidentiality of their OT networks.## FAQs
1. How does secure remote support address the challenge of securing access to plant floor systems?
Secure remote support enables organizations to provide access to vendors while maintaining security. By isolating each asset onto its own microsegment and establishing a secure overlay network, it ensures that only authorized individuals can access the OT network, reducing the risk of unauthorized access and potential security breaches.
2. What are the challenges in opening remote access to OT for support?
Opening remote access in OT networks poses challenges such as strict access controls and limitations, concerns about VPN access, and the insufficiency of firewalls. Ensuring the authenticity and integrity of remote support vendors is crucial in preventing unauthorized access.
3. How does isolating remote access improve security in OT networks?
Isolating remote access creates a secure and controlled environment by enforcing an absolute least privilege policy. It restricts access to only necessary devices, ports, and tasks, minimizing the potential for unauthorized or malicious activity. It eliminates open ports on plant floor assets and prevents access to the rest of the network from remote devices.
4. What benefits does controlling remote access with device isolation offer?
Controlling remote access by isolating remote communications provides several benefits
Reduces the attack surface by eliminating open ports
Maintains the network's integrity, allowing remote support vendors to perform only authorized tasks
Simplifies management and maintenance, and minimizes the risk of security breaches.
5. How can organizations ensure security in isolated remote access?
To ensure security in isolated remote access, organizations should employ the latest methods for device user identification, implement end-to-end encryption for all communication, and monitor remote access activity for suspicious behavior. Regular audits and policy reviews are also important to maintain the consistency and effectiveness of remote support controls.
6. Can isolating remote support improve collaboration between IT and OT teams?
Such a collaboration is a win/win, allowing security to improve the way that remote support is performed. By providing a secure and controlled environment for remote support, it fosters effective communication and coordination between the teams. OT team implements security that meets the tolerances that security demands while the security team improves efficiency and problem resolution.
Platform
Use Cases (Industry)
Use Cases (Application)
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)