🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
Plant Floor Agility - Securely Connecting Legacy Assets
Industrial IoT | Operational Technology | Manufacturing
July 28th, 2023

Introduction
Over the last decade or so, OT has painfully learned that IT integration and security methods need to be adjusted significantly to adapt to the OT world. OT has significantly different business drivers, assets with different operational requirements, and different technical underpinnings. One of the biggest differences is legacy devices. This article explores the issues and most current best practices for integrating legacy technologies into your digital transformation initiative.
The Challenges of Legacy Assets
Legacy assets encompass the machinery, control systems, and sensors deployed prior to the Industry 4.0 era. These assets pose unique challenges. Integrating them into data acquisition systems can be complex and costly. For instance, the process of collecting data from airgapped devices opens the door to other vulnerabilities such as USB malware or staff forgetting to disconnect a temporary connection to the network after completing a scheduled task.
Plant Floor Agility
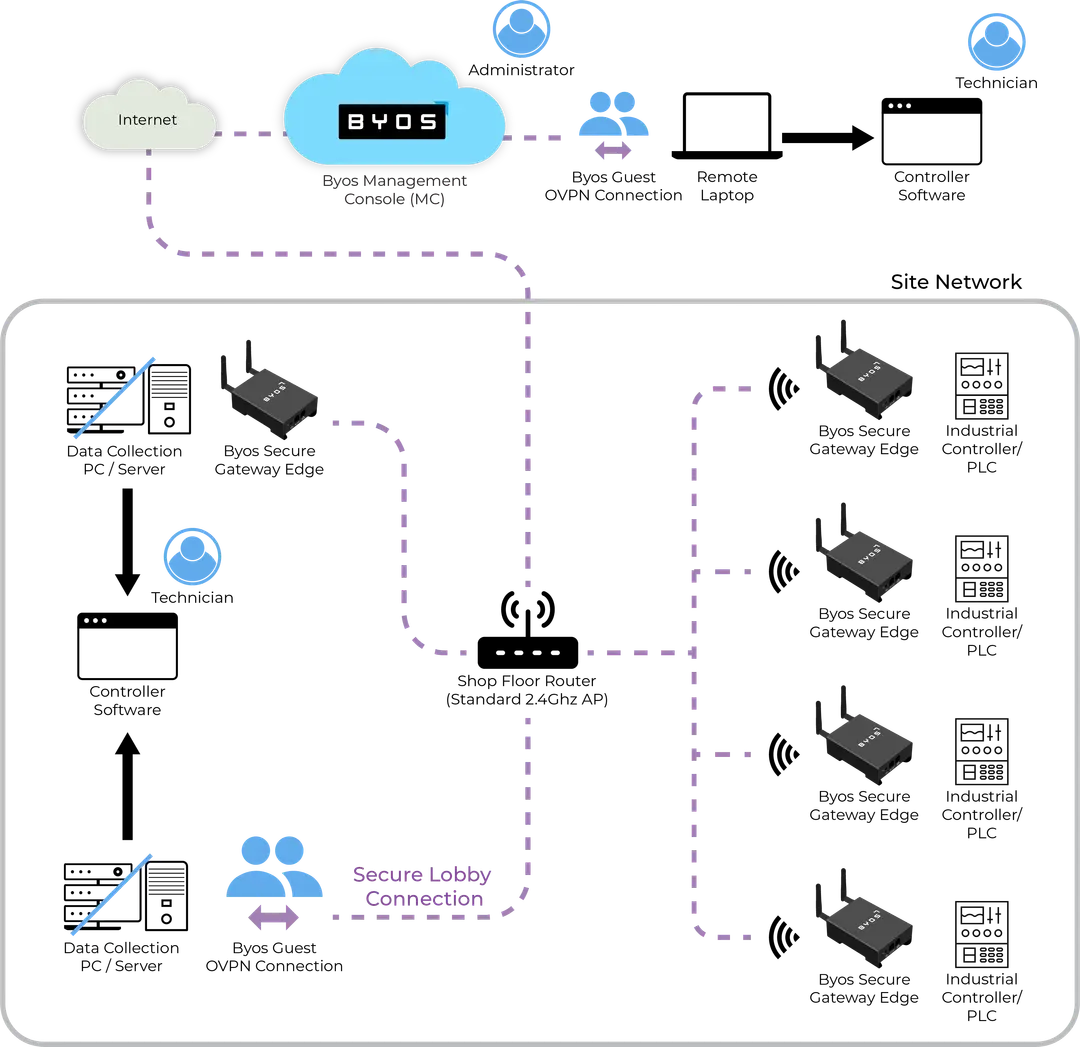
To grasp the significance of securely connecting legacy assets, it is essential to understand the concept of plant floor agility. Data drives decision-making, process optimization, and innovation. Acquiring real-time data from machines on the plant floor provides valuable insight into operations. Achieving plant floor agility involves the integration of the whole process built on effective data flows. Properly secured wireless on the plant floor lowers implementation cost and complexity while making moving of equipment simpler and faster.
Data is Gold!
So digital transformation in manufacturing relies heavily on collecting and analyzing data from various sources, including MES. CMMS, QMS, ERP, and other technologies. Securely connecting legacy assets improves plant floor operations. Establishing secure connections between these assets and central data acquisition systems is vital to mitigate these risks, ensuring data integrity, confidentiality, and availability.
One effective approach to securely connecting legacy assets is by isolating access control to each device individually so that only one device can communicate to it, while the legacy device is restricted from communicating to any other device, including back to the device that is communicating to it. This ensures that legacy assets are not the weakest link in the security chain. It greatly diminishes unauthorized access and lateral movement by potential attackers.
Best Practices for Securely Connecting Legacy Assets
When it comes to securely connecting legacy assets, traditional solutions like VPNs and next-generation firewalls fall short. These assets were not designed to support the advanced security controls necessary for protecting legacy assets. Once a VPN connection is established, a remote device (or user) becomes a trusted entity with access to the network, potentially compromising security. Similarly, firewalls, IDS/IPS systems, and cloud-based protections primarily focus on protecting the network perimeter, leaving the trusted assets inside vulnerable to malicious activities once connected. The asset on the inside becomes an attacker’s “pivot point” whereby the threat actor spreads its compromise first to the target asset and then to through the rest of the supposedly protected network.
Thus, relying on these solutions at the network perimeter, in the cloud, or within network switches is not effective. Instead, a different approach is required to ensure the security of the enterprise network, including legacy assets.
Radically Reducing Your Threat Surface
The goal is to ensure that each user and device has the minimum privileges necessary to accomplish their specific business functions. Access controls need to be unique to each user and device, as well as the policies to be enforced, reducing the risk of unauthorized access and minimizing potential damage.
(When evaluating vendor solutions, it's important to verify how vendors maintain least privilege access. Many vendors use terms like "zero trust" and microsegmentation loosely, so it's essential to seek demonstrations that showcase the specific implementation of absolute least privilege for legacy assets.)
Edge SDN Overlay
An Edge SDN (Software-Defined Network) overlay does three things:
1) It provides uniformity across your extended enterprise (IT, OT, cloud, remote employees, and third parties) providing a simpler, consistent view of your network.
2) It assures the availability of protected assets even when they do not have the ability to access the internet (as enforced by policy).
3) It lets all your assets, including legacy, securely communicate with central resources, including data acquisition systems, while remaining invisible to the underlying network and the internet.
Network Interface-Based Protection
Since legacy assets are incompatible with newer endpoint security solutions, an alternative approach is to implement protection at the network interface of the device. By adding security measures directly at the network interface, the legacy asset can benefit from enhanced security without impacting it’s core functionality. This approach ensures that any traffic initiated from the legacy asset is also subject to security controls, providing comprehensive protection.
End-to-End Encryption
Legacy devices often use outdated encryption. To fix this limitation, it is essential to augment the existing encryption with end-to-end encryption for communication between the legacy asset and assets it interacts with. End-to-end encryption ensures that data remains secure throughout its journey, protecting it from unauthorized access or tampering. The most significant benefit is that attackers are unable to snoop the communications from anywhere in the communication path.
In summary, when securing legacy assets, it is important to go beyond traditional solutions that are ill-suited for these assets. VPNs, next-generation firewalls, and endpoint security solutions may not be feasible options due to the limitations of legacy devices. Instead, focus on OT network security on two key principles:
- Network and device invisibility enabled by an overlay network that creates a simpler and more consistent view of the network across the entire enterprise.
- Absolute least privilege access at the network interface, which ensures end-to-end encryption to establish a strong security foundation for legacy assets.
Conclusion
In today's manufacturing landscape, achieving plant floor agility is crucial for optimizing operations and staying competitive. Securely connecting legacy assets plays a vital role in improving data acquisition and unlocking the potential of these assets. By implementing complete isolation access controls and following best practices, manufacturers can enhance plant floor agility and leverage their OT tools for better decision-making and operational efficiency.
FAQs
Q1: How can legacy assets be securely integrated with modern data acquisition systems?**
A1: Legacy assets can be securely integrated into modern data acquisition systems. A key strategy is to provide security capabilities that are equivalent to those of more up-to-date and powerful systems. Those capabilities include intrusion prevention at the edge, making the asset invisible to unauthorized entities, and accessibility from across the extended enterprise.
Q2: How does secure connectivity contribute to plant floor agility?
A2: When security is implemented properly, the use, administration, and control of the network are enhanced rather than diminished. The network’s organization is more consistent, and assets are easier to locate. With the right design of security, day-to-day administration can be performed by plant floor personnel without having to escalate to staff extensively trained and knowledgeable of networks and security.
Q3: What are the risks associated with legacy assets in terms of data acquisition?
A3: Legacy assets pose challenges in terms of outdated communication, limited processing power, and security vulnerabilities that cannot be updated, making air-gapping or complex compensating controls necessary.
Q4: How can an edge overlay benefit the security of legacy assets?
A4: An edge overlay provides uniformity across the extended enterprise, assures the availability of protected assets even when offline, and allows secure communication between all assets, including legacy, and central resources such as data acquisition systems. It ensures invisibility to the underlying network and the internet.
Q5: What are some best practices for securely connecting legacy assets?
A5: The key aspects of securing legacy assets include absolute least privilege access, network interface-based protection, and end-to-end encryption.
Platform
Use Cases (Industry)
Use Cases (Application)
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)