🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
How to Secure the Work From Home Initiative
Endpoint Microsegmentation | WFH | Wi-Fi Security
March 31st, 2020
Part 3/3 of our Series on Securing Work From Home Initiatives
In the first post of this series, we outlined the Half Dozen Risks of Using Dirty Public Wi-Fi Networks. These risks exist on Wi-Fi networks in coffee shops, hotels, airports, when employees are travelling or working outside of the office.
However when employees work from home (WFH), there are additional risks to consider. We’ve outlined the three ugly work from home Wi-Fi security realities in the second post of our series:
- Employees aren’t protected by the multi-million dollar on-premise corporate security stacks
- Unmanaged consumer devices like personal computers, smartphones, home IoT devices, gaming consoles on home networks increase the attack surface
- VPNs aren’t practical for full enterprise-scale usage and don’t actually protect the device from the network
But that’s enough about risk; let’s now shift the discussion away from the risks and focus more on the implementation: how enterprise security teams can improve security for WFH initiatives.
This post will first explore some fundamentals for establishing a baseline of home Wi-Fi hygiene. It will then compare two different strategies for enhancing WFH security: Network Segmentation vs. Endpoint Micro-segmentation, and the practicality of each for implementation at enterprise-scale.
Steps for Establishing a Baseline of Home Wi-Fi Hygiene
Before we dive in to more advanced strategies for improving WFH security, we acknowledge there are a few things tech savvy users can do to bring their home Wi-Fi up to par with foundational network security principles:
- Create strong passwords for Wi-Fi networks
- Change router’ default passwords
- Create separate Wi-Fi networks for guests and IoT devices
- Keep the router's firmware up to date
Security teams should be proactive in educating users about how and why these steps are necessary when working from home. However, it is likely to be an uphill battle as most users don’t have the knowledge of how to do these things and many of them won’t be bothered. Non-compliance then becomes the issue because security teams have no effective way of tracking or enforcing this behaviour. Overall these tips are achievable for individual employees, but do not scale across the enterprise for securing the WFH Initiative
Creating a More Secure Home Wi-Fi with a Traditional Network Segmentation Approach
Network segmentation is the traditional approach to improving the security of a network. It involves buying enterprise-grade hardware, installing it, configuring security policies, and periodically analyzing its effectiveness.
Security Researcher Scott Helme put together a great tutorial on how he made his own home Wi-Fi more secure.
While this is an effective way of boosting security, there are many practical barriers for organizations to adopt this approach, even for relatively small teams. Traditional network segmentation techniques are impractical because:
- Initial deployment and configuration would be too complicated for most users
- The set-up is intrusive to the rest of the home network.
- Day-to-day management would be complex and inefficient
Most importantly, security teams don’t need to have visibility and control over each employee’s ENTIRE home network; they are only concerned about protecting and managing their corporate-issued devices or any BYOD devices accessing enterprise applications.
A New Approach: Endpoint Micro-Segmentation
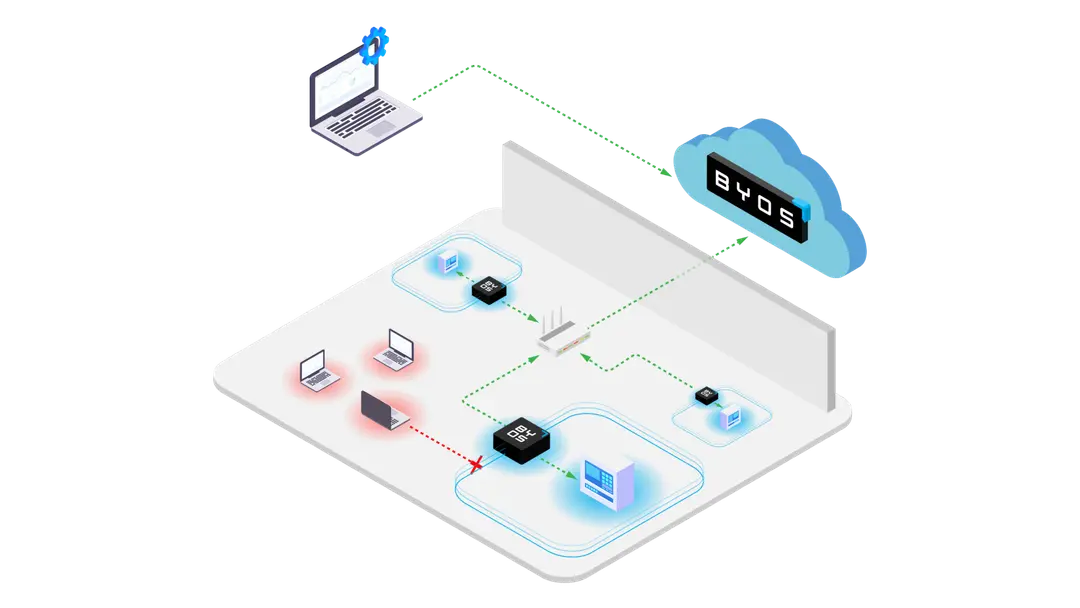
Endpoint micro-segmentation is the approach of creating a “micro-segment of one” where the endpoint device is completely isolated from the Wi-Fi network it connects to, yet still under the umbrella of the corporate security policies. This way security administrators can succeed in protecting only the assets they need to, without controlling the whole Wi-Fi network the device connects from.
At Byos, our solution – the Secure Endpoint Edge™ - creates this “microsegment of one”, extending Zero Trust principles to any Wi-Fi network connection. The Secure Endpoint Edge™ is a miniaturized network gateway, with an embedded security stack, protecting OSI layers 1 through 5. It physically isolates the device from the rest of the network, protecting it in a way security software alone cannot.
Combined with the reporting and analytics capabilities of our SaaS-based Management Console, security administrators can now have visibility and control over remote devices on home Wi-Fi networks. They also have real-time security policy enforcement capabilities through their deployed Secure Endpoint Edges™ without the need for setting up complex, segmented home Wi-Fi networks.
Our solution is simple and cost-effective to deploy, provision and manage at scale. More importantly, it’s simple for the user - the Secure Endpoint Edge™ is plug and play, eliminating the need to configure routers or create new networks.
Summary
In summary, all of us should practice basic Wi-Fi security hygiene, and it is a great time to educate and reinforce this with your WFH employees. However, as more and more sensitive work is done from untrusted home Wi-Fi networks, IT security teams should investigate and deploy scalable and secure solutions to eliminate this risk. Endpoint micro-segmentation is proven at lowering risk, and now with solutions like the Byos
Platform
Use Cases (Industry)
Use Cases (Application)
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)