🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
Byos vs. Software-Agent Microsegmentation: Two Paths Toward Zero Trust
Zero Trust | Microsegmentation
April 30th, 2025
As organizations continue to pursue Zero Trust security models, the debate over the best implementation strategy is far from settled. While most modern solutions rely on software agents installed directly on endpoints, Byos takes a fundamentally different approach—one that’s rooted in hardware-enforced isolation. The architectural differences between these approaches go far beyond technical preferences; they define what Zero Trust truly means in practice.
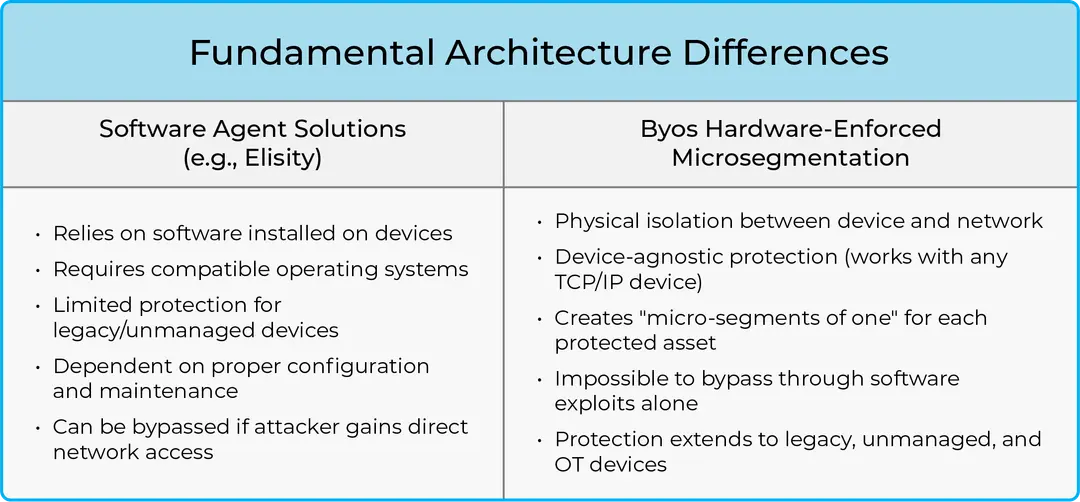
Two Architectures, Two Philosophies
Software-agent microsegmentation platforms like Elisity operate by installing software directly on devices to enforce security policies. This approach assumes a modern, consistent IT environment - one where every endpoint runs a compatible operating system, remains under active management, and can be reliably updated and patched. It also assumes the network perimeter is already breached, so every user and device must be continuously verified.
But this software-dependent model has limitations. Legacy devices, unmanaged endpoints, and specialized industrial equipment often can't support agent-based solutions. And once an attacker gains access to the network, they can often bypass or disable the software agent itself. This makes agent-based architectures a "trust but verify" approach - one that still allows for significant risk in unmanaged corners of the network.
Byos turns this model on its head. Our hardware-based approach physically isolates each endpoint from the broader network using plug-and-play devices that enforce microsegmentation at the edge. This means protection is not only stronger - it’s universal. Whether you're securing a laptop, a 20-year-old PLC, or a headless IoT device, Byos creates a "segment of one" for each asset, ensuring it is cloaked from the rest of the network. No software, no dependency on OS, and no way for attackers to slip through the cracks.
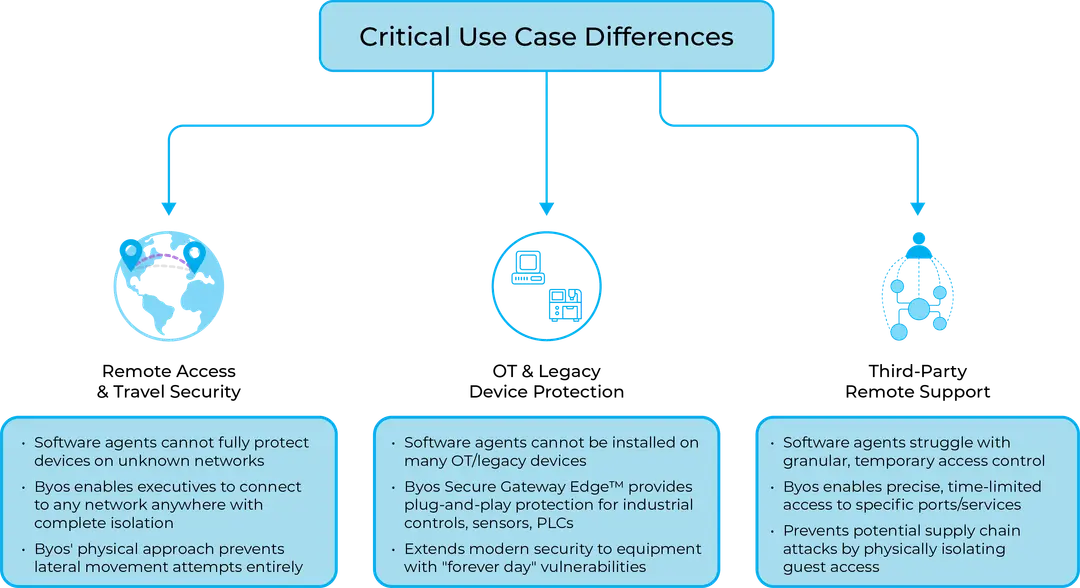
Real-World Use Cases Reveal the Gap
These architectural differences play out in dramatic fashion when applied to real-world use cases, especially in environments where traditional agent-based models fall short.
Remote Access is a perfect example. When executives or field workers connect to unfamiliar or unsecured networks, software agents can't guarantee protection from rogue devices or malicious infrastructure. In contrast, Byos empowers users to safely connect from anywhere in the world by maintaining a hardware-enforced isolation layer between the device and the network. Lateral movement attacks are completely neutralized, even on hostile networks.
Operational Technology (OT) environments and legacy equipment pose another challenge. These systems often run outdated operating systems - or none at all - and simply can't support software agents. The Byos Secure Gateway Edge™ solves this problem with a plug-and-play device that secures critical assets like PLCs, sensors, and controllers, extending Zero Trust protections to environments previously considered unsecurable.
Then there's third-party remote support, where granting access to vendors and contractors introduces enormous risk. Agent-based solutions often lack the ability to offer fine-grained, time-limited access to specific ports or services. Byos, however, enables granular control over who can access what, when, and for how long - all while keeping third-party sessions physically isolated from the rest of the network.
Security That Stops Lateral Movement Cold
One of the most dangerous phases of a cyberattack is lateral movement - when attackers move from an initial beachhead to more valuable targets across the network. Here, software-based segmentation struggles. Once a threat actor compromises a system, software agents can be bypassed or disabled, especially if misconfigurations or patching gaps exist.
Byos eliminates this problem by removing the attacker’s ability to move laterally in the first place. With each device isolated at Layer 2 and access explicitly controlled at Layer 3, the "blast radius" of a breach is reduced to a single device. No domain pivoting, no scanning adjacent assets, no spreading ransomware - just a dead end.
Built for Compliance from the Start
Security isn’t just about threat prevention - it’s also about meeting evolving regulatory and compliance requirements. Byos was designed with frameworks like the NSA’s Zero Trust Maturity Model in mind. Out of the box, it supports key principles for segmentation, visibility, and access control, helping organizations achieve intermediate to advanced levels of Zero Trust maturity faster.
Byos also meets the NSA Commercial Solutions for Classified (CSfC) requirements for secure retransmission devices, offering a modern, hardware-based alternative to mobile hotspots in high-security environments.
Trust Less. Protect More.
Ultimately, the distinction comes down to philosophy. When a software-agent vendor says "Zero Trust," they typically mean "verify, then trust." But at Byos, Zero Trust means "verify, but never trust" - and we back that promise with hardware-enforced protections that cannot be bypassed through software exploits alone.
This isn’t just about defense-in-depth. It’s about designing security architectures that assume compromise, eliminate implicit trust, and make exploitation not just harder - but physically impossible.
Platform
Use Cases (Industry)
Use Cases (Application)
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)