🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
Applying Network Microsegmentation Maturity Levels in Critical Infrastructure using NSA Guidelines
Zero Trust | Microsegmentation
May 14th, 2024
Introduction
The NSA recently released a new report called Advancing Zero Trust Maturity Throughout the Network and Environment Pillar.
For background context, Zero Trust has 7 pillars:
- User
- Device
- Application/Workload
- Data
- Network & Environment
- Automation and Orchestration
- Visibility and Analytics
The objective of the Network & Environment Pillar is to contain lateral movement through the network, preventing access to sensitive data and critical systems. This is suggested to be done by segmenting, Isolating, and controlling (physically and logically) the network environment with granular policies and access controls.
Some of the main network security controls recommended by the NSA are:
- Data flow mapping
- Macro and Microsegmentation
- Software-defined Networking
These security controls need to have various capabilities to meet the needs of Administrators:
- Host Isolation
- Network segmentation
- Enforcement of encryption
- Enterprise visibility
This blog post will break down each control by maturity level, showing how when a customer deploys Byos, out of the box they are at an Intermediate level for their critical infrastructure networks and devices. It will also describe the differences between types of Microsegmentation solutions offered in the market today.
Jump to a section...
Network & Environment Maturity using Byos
Microsegmentation Maturity Levels
Microsegmentation differs depending on the Target Use Case
Network & Environment Maturity using Byos
Below is a description of how the Byos Microsegmentation meets various maturity levels of the sub pillars of Network & Environment pillar of Zero Trust. Out of the box, it provides users with:
- Advanced maturity on Microsegmentation through use of it’s Byos Secure Edge™
- Advanced maturity on Software-defined Networking through it’s Secure Lobby™ overlay network
- Intermediate maturity on Data Flow Mapping using the Byos Management Console™
Microsegmentation Maturity Levels
|
Category |
Level |
NSA Recommendation |
Byos Capability |
|
Micro- segmentation |
Preparation |
Define different security levels on the network based on identity and application access. |
The Byos Management Console is the central control plane by which Administrators do the following:
|
|
Basic |
Organizations begin to transition toward service-specific interconnections and the isolation of critical data flows. |
External Routing Rules as set and configured in the Byos Management Console allow administrators to control various routing parameters of their protected assets:
This is for maximum control of critical data flows. | |
|
Intermediate |
Organizations deploy endpoint and application isolation mechanisms to more of their network architecture with ingress/egress controls between micro segments. Controls are tested and refined as needed. |
By deploying Byos Secure Edge™ devices, Assets are isolated and protected from the network.
| |
|
Advanced |
Organizations employ extensive micro segmentation based on application profiles and data flows, with continuous authentication of connectivity for service specific interconnections. Central management platforms are refined to provide automated and optimal visibility and security monitoring, including alerting on anomalous behavior. |
|
Software-defined Networking
|
Category |
Level |
NSA Recommendation |
Byos Capability |
|
Software-Defined Networking |
Preparation |
Organizations map network segments within their administrative purview and identify a roadmap for SDN component integrations |
With the Byos Secure Secure Lobby™ Overlay, all SDN capabilities come standard out of the box; there is no manual configuration or ongoing management of SDN components needed for the underlying network and devices. You plug in the Byos Edges, set the policies, and boom, the SL™ Overlay is operational. |
|
Basic |
Integrate SDN components and develop a central control plane, along with management policy, network configuration rules, and task schedule (such as updates). Map SDN APIs, establish roles, and configure the SDNC to make API calls using encryption and authentication. |
With the Byos solution, there is no need to maintain any SDN APIs or the SDN controller, as this is done automatically by the platform. Byos has automated everything related to the operation of its SDN including encryption, key management, authentication, updating policy rulesets, etc. It is point and click for any changes, which are automatically applied at the Edge. | |
|
Intermediate |
Test interconnectedness and set configurations to employ segmentation rules at the optimal level of granularity. Create alert systems to notify administrators of anomalous or suspicious behavior. |
Admins have maximum control over which Assets talk to which Assets, all while denying any non-approved traffic. The level of granularity employed is a choice made, not a limitation of the platform.
For example: if there is a compromised asset, talking over a non-standard port or communicating to the internet, the Admin isolates traffic to the SDN overlay to a single port and service. This effectively kills the bad actor's ability to do any more damage via their C2, but gives the Admin the ability to remediate the asset, removing the infection. The Byos platform alerts Administrators about the state of the network, so they can remediate and troubleshoot as necessary. | |
|
Advanced |
Employ advanced analytics and controls. Test the network to determine which network paths would allow an intruder to move between segments laterally or otherwise. Restrict the paths as appropriate with strict access controls. |
The Byos platform is the easiest solution for Software-defined Networking for Assets that are typically difficult to manage or protect. It was built for OT networks in critical infrastructure where networking needs to be high assurance - high security, high reliability, strict access. |
Data Flow Mapping Maturity
|
Category |
Level |
NSA Recommendation |
Byos Capability |
|
Data flow mapping |
Preparation |
Identify locations where data is stored and processed and in which state the data components are stored. |
Every Asset connected to a Byos Edge is auto-discovered, showing the exact ports and services that are exposed through the Asset's firewall. This gives the Administrator a high-level view of all of the Assets in their protected-Byos network. |
|
Basic |
Organizations begin the mapping of both physical and logical data flows. Mapping is primarily manual at this level. Unencrypted data flows are transitioned to encrypted data flows or within encrypted network tunnels or protocols |
The Byos Network Map displays all Edges and Assets within the SDN Overlay, showing which Assets are accessible through the Overlay. Every data flow in the network is autogenerated - Zone and Guest connections, discovered Assets, accessible re, etc. Every tunnel is encrypted with TLS1.3 on the outside and AES256 on the inside, with unique keys per tunnel. | |
|
Intermediate |
Organizations have a complete list of applications and have identified critical data flows. Some automation has been implemented to maintain the accuracy of mappings. Any anomalous data flows identified should be isolated or eliminated at this level. |
Byos is the secure plumbing for all data flows in a micro-segmented architecture. Byos gives the administrator the foundation for setting up upper layer automation rule sets. | |
|
Advanced |
Organizations have a complete inventory of data flows. Automation monitors for controls, and mitigates all current, new, or anomalous data flows. |
Unless an asset is connected to a Byos device, it won’t be discovered. |
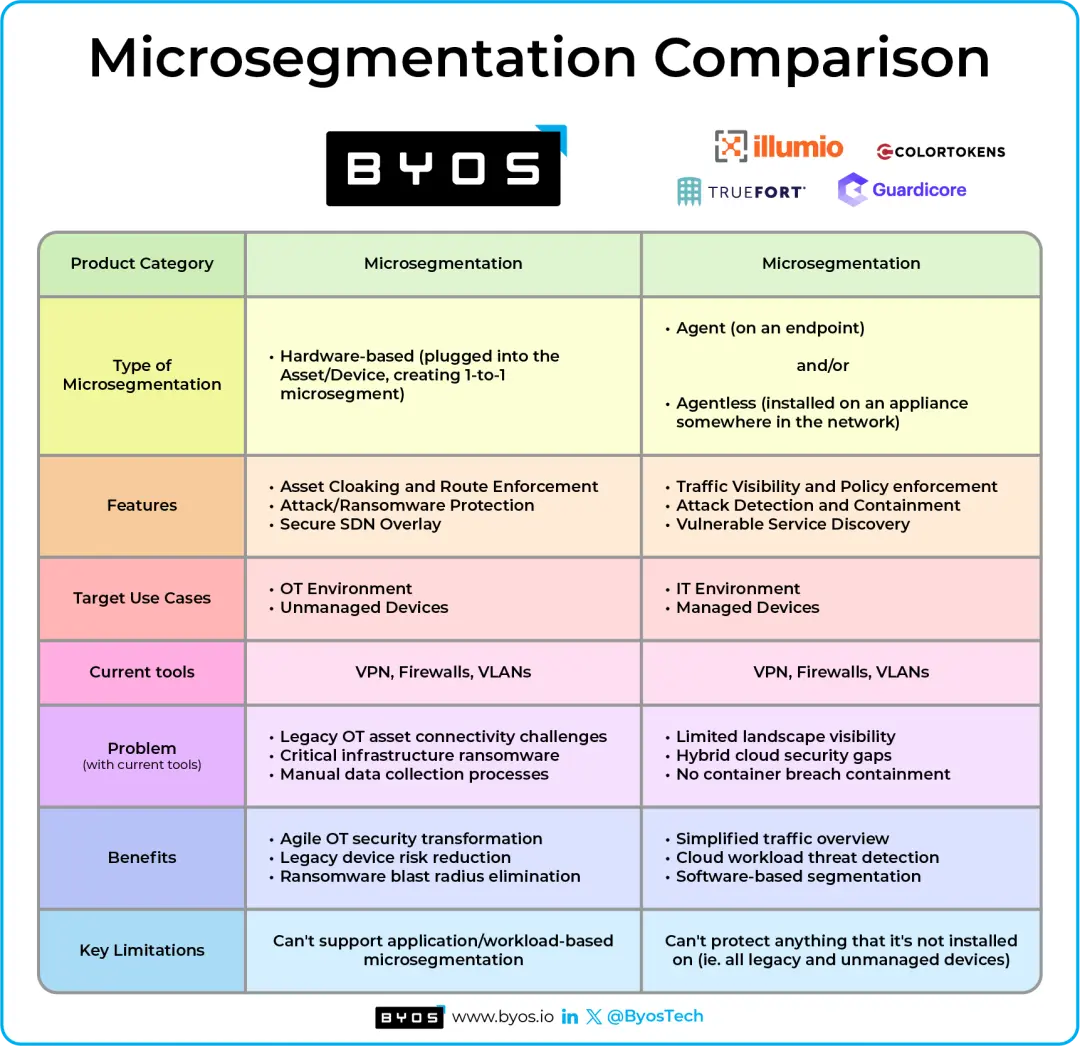
Microsegmentation differs depending on the Target Use Case
Microsegmentation can have different connotations depending on what type of networks, assets, devices, and applications you're running. Not all networks are moving workloads to the clouds and many networks still require Edge compute locally.
When the unit of protection is based on the application or the workload itself, **Application/Workload-based microsegmentation** is the best approach. Companies like Akamai Guardicore, Illumio, Colortokens offer solutions for this type of microsegmentation, where protecting cloud workloads, containers, and applications from malicious traffic and ransomware attacks are the main use cases. However, when the unit of protection is the physical Device or Asset itself, **Device/Asset-based microsegmentation** solutions are more appropriate. Agent-based microsegmentation solutions are suitable for many IT use cases with standard assets like laptops, VMs, and containers, however not all devices are suitable for "software-based segmentation". For example, Legacy Devices are difficult to protect and manage because security software can often not be installed on their incompatible OS. Other single purpose “dumb” devices also often have unpatchable vulnerabilities and can be DDoS'd or exploited very easily, making them a low-hanging fruit target.
A majority of devices in critical infrastructure OT networks are non-standard and need a hardware-based approach. Use Cases in manufacturing and utilities for Machine Data Capture are typical places where these devices are found. Byos is one such microsegmentation solution, where protection is applied at the Edge, and not actually installed on the asset. All things considered, this has many advantages when it comes to deployment, management, protection (Figure above for reference).
To further understand how hardware-enforced microsegmentation can be a robust solution, click here to see a full video explanation.
Platform
Use Cases (Industry)
Use Cases (Application)
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)